成功不易,加倍努力!
- OpenSSL
- 1 OpenSSL 介绍
- 2 Base64 编码
- 3 openssl命令
- 3.1 openssl命令对称加密
- 3.2 openssl命令单向哈希加密
- 3.3 openssl命令生成用户密码
- 3.4 openssl命令生成随机数
- 3.5 openssl命令实现PKI
- 4 建立私有CA实现证书申请颁发
- 4.1 创建私有CA
- 4.2 申请证书并颁发证书
- 4.3 吊销证书
- 4.4 CentOS 7 创建自签名证书
- 4.5 实战案例
OpenSSL
1 OpenSSL 介绍
官网:https://www.openssl.org/
OpenSSL计划在1998年开始,其目标是发明一套自由的加密工具,在互联网上使用。OpenSSL以Eric Young以及Tim Hudson两人开发的SSLeay为基础,随着两人前往RSA公司任职,SSLeay在1998年12月停止开发。因此在1998年12月,社群另外分支出OpenSSL,继续开发下去。
OpenSSL管理委员会当前由7人组成有13个开发人员[3]具有提交权限(其中许多人也是OpenSSL管理委员会的一部分)。只有两名全职员工(研究员),其余的是志愿者,该项目每年的预算不到100万美元,主要依靠捐款。 TLS 1.3的开发由 Akamai 赞助。
OpenSSL是一个开放源代码的软件库包,应用程序可以使用这个包来进行安全通信,避免窃听,同时确认另一端连线者的身份。这个包广泛被应用在互联网的网页服务器上。
其主要库是以C语言所写成,实现了基本的加密功能,实现了SSL与TLS协议。OpenSSL可以运行在OpenVMS、 Microsoft Windows以及绝大多数类Unix操作系统上(包括Solaris,Linux,Mac OS X与各种版本的开放源代码BSD操作系统)。
心脏出血漏洞:OpenSSL 1.0.1版本(不含1.0.1g)含有一个严重漏洞,可允许攻击者读取服务器的内存信息。该漏洞于2014年4月被公诸于世,影响三分之二的活跃网站。
包括三个组件:
- libcrypto:用于实现加密和解密的库
- libssl:用于实现ssl通信协议的安全库
- openssl:多用途命令行工具
2 Base64 编码
Base64是网络上最常见的用于传输 8Bit 字节码的编码方式之一,Base64就是一种基于64个可打印字符来表示二进制数据的方法
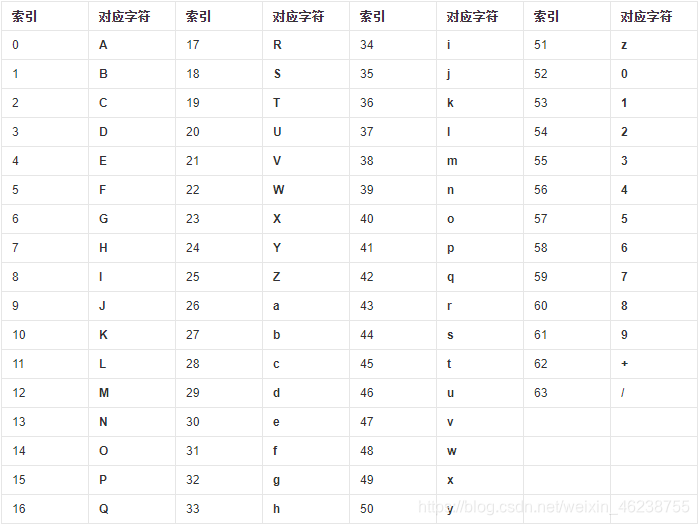
base64的编码过程如下:
将每3个字节放入一个24位的缓冲区中,最后不足3个字节的,缓冲区的剩余部分用0来填补。然后每次取出6位(2的6次方为64,使用64个字符即可表示所有),将高2位用0来填充,组成一个新的字节,计算出这个新字节的十进制值,对应上面的编码表,输出相应的字符。这样不断地进行下去,就可完成对所有数据的编码工作。
按照以上规则对文本Man编码如下:
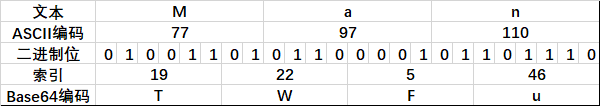
范例:
[root@centos8 ~]
TWFu
[root@centos8 ~]
Man[root@centos8 ~]
[root@centos8 ~]
YWI=
[root@centos8 ~]
ab[root@centos8 ~]
范例:破解下面密文
JXU0ZjYwJXU1OTdkJXU2NzBiJXU1M2NiJXVmZjAxJXU2MjExJXU2NjJmJXU3MzhiJXU2NjUzJXU2NjI1
JXVmZjBjJXU2MjExJXU3Njg0JXU1ZmFlJXU0ZmUxJXVmZjFhMjkzMDg2MjAldWZmMGMldTUzZWYldTRl
ZTUldTUyYTAldTRlMmEldTU5N2QldTUzY2IldTU0MTcldWZmMWYK
3 openssl命令
两种运行模式:
三种子命令:
范例:
[root@centos8 ~]
OpenSSL 1.1.1c FIPS 28 May 2019
[root@centos8 ~]
Standard commands
asn1parse ca ciphers cms
crl crl2pkcs7 dgst dhparam
dsa dsaparam ec ecparam
enc engine errstr gendsa
genpkey genrsa help list
nseq ocsp passwd pkcs12
pkcs7 pkcs8 pkey pkeyparam
[root@centos8 ~]
OpenSSL> help
Standard commands
asn1parse ca ciphers cms
crl crl2pkcs7 dgst dhparam
......
OpenSSL> ca --help
Usage: ca [options]
Valid options are:
-help Display this summary
-verbose Verbose output during processing
-config val A config file
......
OpenSSL> q
3.1 openssl命令对称加密
工具:openssl enc, gpg
算法:3des, aes, blowfish, twofish
enc命令:帮助:man enc
加密:
openssl enc -e -des3 -a -salt -in testfile -out testfile.cipher
解密:
openssl enc -d -des3 -a -salt -in testfile.cipher -out testfile
3.2 openssl命令单向哈希加密
工具:openssl dgst
算法:md5sum, sha1sum, sha224sum,sha256sum…
dgst命令:帮助:man dgst
openssl dgst -md5 [-hex默认] /PATH/SOMEFILE
openssl dgst -md5 testfile
md5sum /PATH/TO/SOMEFILE
[root@centos8 data]
MD5(fstab)= ba52d047da74624f1b009f1f73c4a54a
[root@centos8 data]
SHA512(fstab)= 6b814b403efe8da89edc8219ffe280b857a51f19ec864880d1135da46d441d9dea40a85092515dbb42bdf823a2148ab4ba94b78e7aa0b55c439ada07069190f5
[root@centos8 data]
6b814b403efe8da89edc8219ffe280b857a51f19ec864880d1135da46d441d9dea40a85092515dbb42bdf823a2148ab4ba94b78e7aa0b55c439ada07069190f5 fstab
补充知识:
MAC: Message Authentication Code,单向加密的一种延伸应用,用于实现网络通信中保证所传输数据的完整性机制
HMAC:hash-based MAC,使用md5或sha1算法
3.3 openssl命令生成用户密码
passwd命令:帮助:man sslpasswd
[root@centos8 ~]
Usage: passwd [options]
Valid options are:
-help Display this summary
-in infile Read passwords from file
-noverify Never verify when reading password from terminal
-quiet No warnings
-table Format output as table
-reverse Switch table columns
-salt val Use provided salt
-stdin Read passwords from stdin
-6 SHA512-based password algorithm
-5 SHA256-based password algorithm
-apr1 MD5-based password algorithm, Apache variant
-1 MD5-based password algorithm
-aixmd5 AIX MD5-based password algorithm
-crypt Standard Unix password algorithm (default)
-rand val Load the file(s) into the random number generator
-writerand outfile Write random data to the specified file
范例:
[root@centos8 ~]
cui:$6$ARZrof3ZBlFLYESn$SrsreMQqIOTtT/8NIn6w1nil/jrXY67nT3gXcs6Z9AH4iz5t4GakIJUiiu6/rnnDbNAhy68f.YBS0acCFuYT8/::0:99999:7:::
[root@centos8 ~]
$6$ARZrof3ZBlFLYESn$SrsreMQqIOTtT/8NIn6w1nil/jrXY67nT3gXcs6Z9AH4iz5t4GakIJUiiu6/rnnDbNAhy68f.YBS0acCFuYT8/
[root@centos8 ~]
$6$ARZrof3ZBlFLYESn$SrsreMQqIOTtT/8NIn6w1nil/jrXY67nT3gXcs6Z9AH4iz5t4GakIJUiiu6/rnnDbNAhy68f.YBS0acCFuYT8/
范例:创建新用户同时指定密码,在CentOS和Ubuntu都通用
[root@centos8 ~]
[root@centos8 ~]
zhang:$6$ARZrof3ZBlFLYESn$SrsreMQqIOTtT/8NIn6w1nil/jrXY67nT3gXcs6Z9AH4iz5t4GakIJUiiu6/rnnDbNAhy68f.YBS0acCFuYT8/:18402:0:99999:7:::
[root@centos8 ~]
zhang:$6$ARZrof3ZBlFLYESn$SrsreMQqIOTtT/8NIn6w1nil/jrXY67nT3gXcs6Z9AH4iz5t4GakIJUiiu6/rnnDbNAhy68f.YBS0acCFuYT8/:18402:0:99999:7:::
cui:$6$ARZrof3ZBlFLYESn$SrsreMQqIOTtT/8NIn6w1nil/jrXY67nT3gXcs6Z9AH4iz5t4GakIJUiiu6/rnnDbNAhy68f.YBS0acCFuYT8/::0:99999:7:::
范例:
openssl passwd -1 -salt SALT(最多8位)
openssl passwd -1 –salt centos
3.4 openssl命令生成随机数
随机数生成器:伪随机数字,利用键盘和鼠标,块设备中断生成随机数
/dev/random:仅从熵池返回随机数;随机数用尽,阻塞
/dev/urandom:从熵池返回随机数;随机数用尽,会利用软件生成伪随机数,非阻塞
帮助:man sslrand
openssl rand -base64|-hex NUM
NUM: 表示字节数,使用-hex,每个字符为十六进制,相当于4位二进制,出现的字符数为NUM*2
范例:生成随机10位长度密码
[root@centos8 ~]
6SOm1c6y1c[root@centos8 ~]
[root@centos8 ~]
GbfE24koEK[root@centos8 ~]
3.5 openssl命令实现PKI
公钥加密:
- 算法:RSA, ELGamal
- 工具:gpg, openssl rsautl(man rsautl)
数字签名:
密钥交换:
- 算法:dh
- DSA:Digital Signature Algorithm
- DSS:Digital Signature Standard
- RSA:
openssl命令生成密钥对儿:man genrsa
生成私钥
openssl genrsa -out /PATH/TO/PRIVATEKEY.FILE [-des3] [NUM_BITS,默认2048]
范例:
[root@centos8 ~]
Generating RSA private key, 2048 bit long modulus (2 primes)
...............+++++
.............+++++
e is 65537 (0x010001)
[root@centos8 ~]
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEA07M+D3J8MdAEj2Mx35XXjpqKZ5OmfsSWY5wJQDHDSEQ6KRYS
8pRaKOQUfMqJfa2cdclZ8q0M38uxn+YdeL1y4qP095qD/KWpx83vlnoDB7Zqtf/P
8yydCjcNloH7frfFOaQ8d7qzwzLlDAMWpa1gv9S1MvgsX2fSpL+Lu+SL4hzir4xC
1seAiG/32FCyDSI04w8PXf3boBXheNmCH0Ug2XSDyE96w3KU32Px8PijxF1wRgnJ
RLlDhzgJ4O2dinh+6hwWi3uEcq8H+qkyNkIAeuuyWJ7WqMIXz77+s6JPv9GPqnUz
EPDsXlnRrww4JfmbC5fzlW6HWja+FU7VteGE6QIDAQABAoIBAAsBY3WMHxa72LDX
mE0mTgl00UMnMt2ePK86+mQi8iL8oQVnx15jBfjgOoxuPw2Qi/S3nfx2sJel0Dse
zGNtfd54ZZDFsJzew9/GPfFVsHijLBMAFIBwzk0spYEwirGAvjkL57TVuOip6axh
MLk2NTRjy3O14SColhPIfWwsKnV7sLH+LK8Q6GDyTCuQM4ttgTBdqiA1xZMlsXO9
LADrV3TIlGMN1mGUzVj+TA4cstCKOrdOuymhWdNYHZRO0hgGmOE+cXBVbUr+h8wF
3Km8W8FGcXVW00cqT9QilLJXFPcDql3VUJe1q9A41TEjx8G/dMbdmVXJ2NZe/us5
i6BVrnECgYEA9unVESGrC64NznPjGpc+W+EFhLKT5tpASAfS13iwFMqRu1Esk0Jk
zukIpwhnF4DxM0ZKeAyDi66xjGYF8P8Wc1fZhZCIqsoBdp+NxLeVH+gLptH9V4Gg
tfN3ui5U/u6muSkyEoD9VPQy/1U9AmWmAqlDKFBfdj+jElxp13hKXh0CgYEA232q
q5DGPPXVarLrvhwre/69/Vd9qKmjD4c4baFyYS6EUexDCAIN7c0098YF3oXq+q+K
O8cWIBZLXHZKmjjT9rHLWAqWdPC//h2+bcAewHEMLACizYYjL6I9b+HQtixDmvUA
OJrm7cIEJrwEysnHMgUhTvXF6LzQvMMnWjhh+D0CgYAjrMNhN0kcZeiOxMWyaNnU
sp12f8rI1w3kmmTHRyPBzUbjFqZnHHeuQZNDdv5WMgYnj2dhEwXKn9H9ZBxFpsWa
or3GA40LiCZP+lukaZX9RyyvzLVa+Fq9D1FkMB+NufOS2zXl4Ic5yBK6O5mWCBPF
XKlcYMh6MFWiaIHOZQ3xrQKBgQDHq7tuFebxH+ZFCX1B1diNFUH6zPOoUqHfB3EC
8oLd+3YuHJMiHtRTB4HvATrnosYPxU8ocEUlbYKjG41kXNweqMFGV2NmAHl4D9Dj
gIm5IV4kTXPNKgCqXZosRK4ce4oI1macF/aKRhyGrDZj0EmgrGAPt6+RuOrfPV14
SqB9NQKBgDLD5vkjFovDLVg0hqHaMoZ8fqAOonVobBNX7UOwf2M1WwJzZfcVKG/j
MQdxm7H0uE1NrSEKC+gRJZmzp8GodTJ9Y+iu7kv7Ju/uDBgcFk75/Y3zEf1tYAZi
gyEGDH7ME9+X6xitjMAHYnQNUT2Sq7/cxjX4USiIirIVR44eXnRp
-----END RSA PRIVATE KEY-----
[root@centos8 ~]
Generating RSA private key, 2048 bit long modulus (2 primes)
........+++++
......................+++++
e is 65537 (0x010001)
Enter pass phrase for /data/app2.key:
Verifying - Enter pass phrase for /data/app2.key:
[root@centos8 ~]
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,170BB158ABFA1750
WAVQIqG6Ts1QV0tMGbaG+9Y4/jgVPQsYaew/WuS2S71VxPVw3bN9jk+ZhentebDf
E5RTLn4aV9HUhyDO8tSKtJVwy7kKDVX7QqQNg0G/ZhLKR1afuDjKiBrAt0z9gU2B
GkSPcfhJFraGyu4n+G3uBeK+h0bpFwcIqqWOVVU/GQJ76dCtkEu9CjPXdQBjPfPN
Hm5fgAG2OqYEmyPoDUnAWCGHNceGz8+N4jmbZ4kZDvcguoV+IlehrlJrDW9MO/Lq
QUaxVONp6W/CVt1ZKIOyRQ3Xmti2jcLOzDv+2RnSleo//iIvbThQcG9ABDVhMgIx
hOa0iYhAoGsdsAogiwGQX1pfYRRdrW3LR/jJP5asYYGOgYG7+fC3LqaFEVic+SZ+
rhtwcrkQi2zwxevlg2Fo08olzjuY1wiuzZWGuz2uDBjRKz+APlIHulqA7tX7esA+
fm995sXvATL26HR8LJ5MTCsRrghuK/b1YlHFoOAFy0EikcKz2gvtHYUscZMsdscu
AUvZZdnL/P2KEum55mnBjPjqKB1Pw8K9lGBApzmVHteoHigDOeVeWPpVMM9ra8Si
9AJdpmXWSVRnZoaTmsGdO4gsRHtkDUpKhgFXBbPw5yYSzm3n/jIDheWjUFIURwvk
b+wJeTK2J3u/ebp7Kx/UAAKZWWwg+8aoepLhrKjYagjS8IHLxt8OQ2+Zs9SOF7v6
lbo2KkKjsJ3U9coItum9GAqNiszVDLrVO7YStSFxoB85WRf6+vycgRctWKHITLSd
SlNMZAAYmj3JLRMg7B0Kvmu2iUGRBVhAhyZ9CRMiLI6XP02/JMpeUdGJQ3wNlqa6
eBtFowThkD6SABi+RM+g49a6a38kfkgUHXvy8cY4FVtZhsDOtb16FDPUsLFRdOtX
G3uXwltIstctKtAw18TPYZxT3vNp0HYFc/JOO31pCpY1vDH+K55WoyY1pLzcWcPG
IoP44klIY4KYBGPj85O+pNeaUh9W/HdfRPsSgjokLl/0DHDqQnPj0X55eaMmQVnx
f47EqyE0JVQkPo5VINHon8ZIa+QWPYc2UZz6oLWCfTXx2ON7Lp0NGDosN+BmqGmL
xD/BeC++HVWTmulc00yVs0BtR/E+F4ppwbupQuUfDT23M8SZ+UCrniMTYFJDCdU8
CcAtcqxvEsjsCwr5f7tmtKVZ+L8E+iEwEmqWb3Z2076QbePI+J4KC0gxvaHAiZS8
BcwJAmVx06sXxJolCdHAQNnml87DAn3s1lVddl0qH8PW57p1BUZwPmF0l124kyjz
iGhs3DTnOjRIUux91iK4A8LDmSu2E4goaaqUasYbhJANKfPGmzJc3aQDAmy6AbLb
dXi5J2mgq1g2N8/esvonwPLq6T4GdJbotdRasDEBdte+R+PcTKP1x2BxNMRqk8O6
sJd2pEo+j0h5IGUrWcnQ1VLJXrulu08fAWmfZzIISkB84iEv0f9aahjnmbnDg6hr
+M+VCufsdjRcVeplfhYHRr/QUb66aDkQEw3VEbmBYshfbRqJg8ALtNMmGI3MvMBQ
d6gN5WRktAEmX20oI4Z588d79d9op5KTTJYWf6GXqComrA/e3TJzFw==
-----END RSA PRIVATE KEY-----
从私钥中提取出公钥
openssl rsa -in PRIVATEKEYFILE –pubout –out PUBLICKEYFILE
范例:
openssl rsa –in test.key –pubout –out test.key.pub
范例:
[root@centos8 ~]
writing RSA key
[root@centos8 ~]
total 8
-rw------- 1 root root 1675 May 20 22:34 app.key
-rw-r--r-- 1 root root 451 May 20 22:35 app.pub.key
[root@centos8 ~]
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwtz/zur9wEVQ4p2FB8yf
oFCGqYgtjJtYd/ZDC9K4OV3+o+eX4YjRigx2MZ1t0AK26d+e3UXOVprAgkwTg40f
wVye0iQaWCOZwySmLZybyZiGSwFViefEkrE9r5Bvn9iIRu+2zIA21R0DV2CnAdp1
AMEMysovBF6sy6unGAj8tYovDyPvH5tOM03pXkckrt58md8AFOKeW4CyIF31LDM1
94kPUqWzM7GQqdk86VbR46lppXPj0Hxe8Fg2zQqgShWzWpskBjtPX5cWxtjq0D90
M07w4klNGbR43vTOzgquC4VZyuk7Y1RWftKKp7JphAR5Q2DLVLdzHe8/Zqg/YqoM
/wIDAQAB
-----END PUBLIC KEY-----
范例:
[root@centos8 ~]
Enter pass phrase for /data/app2.key:
writing RSA key
[root@centos8 ~]
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAwAkdfjBQowO/BQl05s+C
sZ2Q7CFfcNL5fiIReQhmDZm8BDGUwX/Pps7EO5YTC3T45Nt0zgbRqimoZ6g5soQm
GMMId3j5Du1Pjl9gYqDx6Jf5X6jSzq/r5TYgn4Gc0SsrG8fB00MN7xwUEsuE4GK8
Z9cQpt9HhjaqC4Va21e4JH33dhwzpjKzaUuD0dmjVJdsZV+BQFT4FTpneu0RIo8r
8VocXh1Vn/U77g2VFn5Xm4BhrqxqgX48r0AQZB6wxgE2xrjij2GInVJpiFL1SGYc
nZ6m2VS4Gwe6QoUi1GC1bKeElGh8vgcPF8oX2vb0ulZCJVlSkM8n91J9yrEmCZOR
WQIDAQAB
-----END PUBLIC KEY-----
范例:生成加密的私钥,并解密
[root@centos8 ~]
Generating RSA private key, 1024 bit long modulus (2 primes)
.........+++++
................+++++
e is 65537 (0x010001)
Enter pass phrase for /data/app.key:
Verifying - Enter pass phrase for /data/app.key:
[root@centos8 ~]
total 4
-rw------- 1 root root 963 May 20 22:44 app.key
[root@centos8 ~]
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,9907D3F8A9C64B87
PE7S9Acrq2LSaPe5DKEq/LSiDqyNnb7LQYlmEuypJozAJbTf1UyrZXn94grGlolO
P6/AhF3I13x1WxBjFPFVPI/MsVPR6mrnHJMv+X1DnZil94uQHpSWCCANbBch+PBm
+nPU9dWsMJXKUwGTnn40OZiApk2nbKowVUxiUrTP9zHUIbz7ZH91QAesrsk5i+c6
zQPovM+nKSk2X4SMXwyq6/KqfsIG6S3JNpODfWPCXvJcPRwaTT1/6ACDyMuF9L8S
R6FUXkeolKRvQGTm+5jHCcwRpXlNsJP3FXpISlidFfGkrQeOXI3aWGuVzQcIq+Nx
9rk+o9zYN/e+UursCGMCpMqueIYHnrxEYmev35DagmBP+FITLRE0aNZZW7ZEgttK
lRE7GSdIoZTQ6ydKG+QpU8ws7WkRwXvnPKS+ECbL9n8Gvw2x/HK0Pe11PFjs0r1B
QMrEP26ZogfT8t5YxLBeJcZEe4aDsGx/Qk9s+TJjwqWQzaMHHg6OXBjDf6uMH0kQ
3FHmvrygHLgG92lLYv7B2c/pDGduX1FiqROeTdAlEljB/zvdcLpP54gCJ5SdhgWV
SCTvI9J2EQDP0PWr+KywtQ+VS9JDv5Em9HJUt/GWJBPsUmWLrGrGc0N8N1ENBbGX
aM/0x3KJld4GhFYAoMR/oRZoofRLzdapGBaUvRQuqFCJJiNbELRKGKLpt8GPGIHY
pUBxSUE/I+5jGhdfa0uHGmbdbJ4yaNfi4yNQRUS4sSOztPAZR8Hde1+RkawP8eKl
pjoJMxVeYR72U9dQDV6ICFfUXhmMQNUkJ1ZbG3aqg3Hu+Tl6vM52jw==
-----END RSA PRIVATE KEY-----
[root@centos8 ~]
Enter pass phrase for /data/app.key:
writing RSA key
[root@centos8 ~]
total 8
-rw------- 1 root root 963 May 20 22:44 app.key
-rw------- 1 root root 887 May 20 22:45 app.key2
[root@centos8 ~]
-----BEGIN RSA PRIVATE KEY-----
MIICXAIBAAKBgQCs3jHl3Wr3r9YtA4HePmnBj/KGKM+KODoDGOXtJ9PDLIAc3BcD
NbMtZTfghwztRobLAS8yg27nUhj8W2xehklNjT0Ewb2X3nfftOSx9Ly692y9TSPL
KJN6uVNJTYO4dG7TVo5sG74E0CsW0rHoSYSiWSIFJS/8O0c3r9jTb8Xi6wIDAQAB
AoGAOAW+WAdc3i5vE6F6WgMSFPfImi/pqpq0OkK8aRIqL6thTXkKQDEMA181L5+0
0cS0dF/K4uzzaSYTEN20DiIo6N9ejLQ8832JAqIjzsEmYhkgttiFt8umsNfYGEBu
G4gLhnJxHD3knlfZYcevBwJHsOgT9+yw2dEnNKVwUbSlVBkCQQDj2ZPjKZUCfbGO
yKW4QvxmRdQOT177NjB82ypNX7YoGe1S5out8TYL+NzYBy1+wKmjcQjebQpkojrb
Zz8IQf/nAkEAwjmmts5y5qBYUlDUmUWx/T+MYku7/VzA8VRn8Nc3xt1iVRfbCoGz
Y0E8wCmbO5mdLgVbx192cuQgDcsuo4c0XQJAKVgt0aaV92G/el1GVO0yx4wcMoyM
e6EVo1JRlsCrWRN7UPOsnN+MIxgBWuHSi5GCNrooFdRLcn9NlsphUapIOQJAQyMm
i75lXW9D2IB0XN8InZ/f6QKA4x2y3DjvDQN4Flfka8GpR8J5ve+JDmvTaxC4knXr
uck36pMMuXfokUJlSQJBANF55bBcWbr/5zanKRdwar3bUwtHkTfIesHiHr+mfo64
s7t7IaxUY02BS4V1prq7fxOV8HSqhcsYs+SE2CPmtiY=
-----END RSA PRIVATE KEY-----
4 建立私有CA实现证书申请颁发
建立私有CA:
- OpenCA:OpenCA开源组织使用Perl对OpenSSL进行二次开发而成的一套完善的PKI免费软件
- openssl
证书申请及签署步骤:
1、生成申请请求
2、RA核验
3、CA签署
4、获取证书
范例:openssl-libs包
[root@centos8 ~]
/etc/pki/tls
/etc/pki/tls/certs
/etc/pki/tls/ct_log_list.cnf
/etc/pki/tls/misc
/etc/pki/tls/openssl.cnf
/etc/pki/tls/private
/usr/lib/.build-id
/usr/lib/.build-id/2f
/usr/lib/.build-id/2f/d658368c8d16cc6d2bc9584eca2b757c98df18
openssl的配置文件:
/etc/pki/tls/openssl.cnf
三种策略:match匹配、optional可选、supplied提供
match:要求申请填写的信息跟CA设置信息必须一致
optional:可有可无,跟CA设置信息可不一致
supplied:必须填写这项申请信息
范例:
[root@centos8 ~]
......
[ ca ]
default_ca = CA_default
[ CA_default ]
dir = /etc/pki/CA
certs = $dir/certs
crl_dir = $dir/crl
database = $dir/index.txt
new_certs_dir = $dir/newcerts
certificate = $dir/cacert.pem
serial = $dir/serial
crlnumber = $dir/crlnumber
crl = $dir/crl.pem
private_key = $dir/private/cakey.pem
x509_extensions = usr_cert
name_opt = ca_default
cert_opt = ca_default
default_days = 365
default_crl_days= 30
default_md = sha256
preserve = no
policy = policy_match
[ policy_match ]
countryName = match
stateOrProvinceName = match
organizationName = match
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
[ policy_anything ]
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = supplied
emailAddress = optional
......
4.1 创建私有CA
1、创建CA所需要的文件
touch /etc/pki/CA/index.txt
echo 01 > /etc/pki/CA/serial
2、 生成CA私钥
cd /etc/pki/CA/
(umask 066; openssl genrsa -out private/cakey.pem 2048)
3、生成CA自签名证书
openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem
选项说明:
-new:生成新证书签署请求
-x509:专用于CA生成自签证书
-key:生成请求时用到的私钥文件
-days n:证书的有效期限
-out /PATH/TO/SOMECERTFILE: 证书的保存路径
国家代码:https://country-code.cl/
范例:生成自签名证书
[root@centos8 ~]
Generating a RSA private key
..+++++
..............................+++++
writing new private key to 'app.key'
-----
[root@centos8 ~]
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
6a:69:ec:c8:85:98:9c:e3:6a:99:a5:56:b1:22:76:c4:fb:1d:85:41
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = www.magedu.org
Validity
Not Before: May 24 04:38:24 2020 GMT
Not After : Jun 23 04:38:24 2020 GMT
Subject: CN = www.magedu.org
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (1024 bit)
Modulus:
00:d3:f2:95:7c:4c:17:91:8d:93:7a:c6:91:31:f3:
fb:97:c9:c2:6b:3d:47:d3:47:e4:c7:f9:ef:97:65:
dc:64:6a:a5:ba:dc:2f:40:64:86:d0:40:b3:70:fb:
38:5a:11:b4:ec:21:e1:68:23:a4:53:66:dc:a4:76:
a2:91:75:d9:7b:51:4b:fb:3e:a8:86:44:72:99:7a:
41:d2:07:82:69:28:a9:06:74:42:e3:ce:9e:63:75:
9c:d0:d7:3c:96:79:ad:80:d6:9b:72:9a:33:25:46:
ec:50:b1:c0:3b:9c:65:38:ba:15:3a:17:8f:ff:43:
6e:28:53:01:c3:6c:31:c4:91
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
45:A2:CA:F2:21:4F:17:82:A6:A4:D2:CA:36:FE:17:A0:97:C6:DB:29
X509v3 Authority Key Identifier:
keyid:45:A2:CA:F2:21:4F:17:82:A6:A4:D2:CA:36:FE:17:A0:97:C6:DB:29
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
c8:06:8e:ab:a6:ea:ca:34:5e:d6:77:e1:25:fd:44:d5:cb:55:
a7:25:cc:7f:9a:da:65:f0:5c:b5:f4:c6:c8:2e:dc:64:f9:e8:
b4:77:74:ed:f9:10:b0:0f:d4:a9:3a:35:0e:c0:7d:23:98:2b:
07:df:70:94:dc:62:2f:c4:c0:7a:9c:41:0d:3c:ca:b2:2c:6e:
39:fc:05:45:71:f6:81:df:92:ab:23:c7:28:eb:f5:65:28:44:
e2:9f:cc:ea:72:fc:20:ab:86:fd:79:00:6e:bc:16:93:b3:80:
d1:c8:0d:c9:06:65:26:af:21:dc:e7:76:4c:42:1b:de:e6:43:
21:27
4.2 申请证书并颁发证书
1、为需要使用证书的主机生成生成私钥
(umask 066; openssl genrsa -out /data/test.key 2048)
2、为需要使用证书的主机生成证书申请文件
openssl req -new -key /data/test.key -out /data/test.csr
3、在CA签署证书并将证书颁发给请求者
openssl ca -in /tmp/test.csr -out /etc/pki/CA/certs/test.crt -days 100
注意:默认要求 国家,省,公司名称三项必须和CA一致
4、查看证书中的信息:
openssl x509 -in /PATH/FROM/CERT_FILE -noout -text|issuer|subject|serial|dates
openssl ca -status SERIAL
4.3 吊销证书
在客户端获取要吊销的证书的serial
openssl x509 -in /PATH/FROM/CERT_FILE -noout -serial -subject
在CA上,根据客户提交的serial与subject信息,对比检验是否与index.txt文件中的信息一致,吊销证书:
openssl ca -revoke /etc/pki/CA/newcerts/SERIAL.pem
指定第一个吊销证书的编号,注意:第一次更新证书吊销列表前,才需要执行
echo 01 > /etc/pki/CA/crlnumber
更新证书吊销列表
openssl ca -gencrl -out /etc/pki/CA/crl.pem
查看crl文件:
openssl crl -in /etc/pki/CA/crl.pem -noout -text
4.4 CentOS 7 创建自签名证书
[root@Centos7 ~]
[root@Centos7 certs]
This makefile allows you to create:
o public/private key pairs
o SSL certificate signing requests (CSRs)
o self-signed SSL test certificates
To create a key pair, run "make SOMETHING.key".
To create a CSR, run "make SOMETHING.csr".
To create a test certificate, run "make SOMETHING.crt".
To create a key and a test certificate in one file, run "make SOMETHING.pem".
To create a key for use with Apache, run "make genkey".
To create a CSR for use with Apache, run "make certreq".
To create a test certificate for use with Apache, run "make testcert".
To create a test certificate with serial number other than random, add SERIAL=num
You can also specify key length with KEYLEN=n and expiration in days with DAYS=n
Any additional options can be passed to openssl req via EXTRA_FLAGS
Examples:
make server.key
make server.csr
make server.crt
make stunnel.pem
make genkey
make certreq
make testcert
make server.crt SERIAL=1
make stunnel.pem EXTRA_FLAGS=-sha384
make testcert DAYS=600
[root@Centos7 certs]
ca-bundle.crt make-dummy-cert renew-dummy-cert
ca-bundle.trust.crt Makefile
[root@Centos7 certs]
UTF8 := $(shell locale -c LC_CTYPE -k | grep -q charmap.*UTF-8 && echo -utf8)
DAYS=365
KEYLEN=2048
TYPE=rsa:$(KEYLEN)
EXTRA_FLAGS=
ifdef SERIAL
EXTRA_FLAGS+=-set_serial $(SERIAL)
endif
.PHONY: usage
.SUFFIXES: .key .csr .crt .pem
.PRECIOUS: %.key %.csr %.crt %.pem
usage:
@echo "This makefile allows you to create:"
@echo " o public/private key pairs"
@echo " o SSL certificate signing requests (CSRs)"
@echo " o self-signed SSL test certificates"
@echo
@echo "To create a key pair, run \"make SOMETHING.key\"."
@echo "To create a CSR, run \"make SOMETHING.csr\"."
@echo "To create a test certificate, run \"make SOMETHING.crt\"."
@echo "To create a key and a test certificate in one file, run \"make SOMETHING.pem\"."
@echo
@echo "To create a key for use with Apache, run \"make genkey\"."
@echo "To create a CSR for use with Apache, run \"make certreq\"."
@echo "To create a test certificate for use with Apache, run \"make testcert\"."
@echo
@echo "To create a test certificate with serial number other than random, add SERIAL=num"
@echo "You can also specify key length with KEYLEN=n and expiration in days with DAYS=n"
@echo "Any additional options can be passed to openssl req via EXTRA_FLAGS"
@echo
@echo Examples:
@echo " make server.key"
@echo " make server.csr"
@echo " make server.crt"
@echo " make stunnel.pem"
@echo " make genkey"
@echo " make certreq"
@echo " make testcert"
@echo " make server.crt SERIAL=1"
@echo " make stunnel.pem EXTRA_FLAGS=-sha384"
@echo " make testcert DAYS=600"
%.pem:
umask 77 ; \
PEM1=`/bin/mktemp /tmp/openssl.XXXXXX` ; \
PEM2=`/bin/mktemp /tmp/openssl.XXXXXX` ; \
/usr/bin/openssl req $(UTF8) -newkey $(TYPE) -keyout $$PEM1 -nodes -x509 -days $(DAYS) -out $$PEM2 $(EXTRA_FLAGS) ; \
cat $$PEM1 > $@ ; \
echo "" >> $@ ; \
cat $$PEM2 >> $@ ; \
$(RM) $$PEM1 $$PEM2
%.key:
umask 77 ; \
/usr/bin/openssl genrsa -aes128 $(KEYLEN) > $@
%.csr: %.key
umask 77 ; \
/usr/bin/openssl req $(UTF8) -new -key $^ -out $@
%.crt: %.key
umask 77 ; \
/usr/bin/openssl req $(UTF8) -new -key $^ -x509 -days $(DAYS) -out $@ $(EXTRA_FLAGS)
TLSROOT=/etc/pki/tls
KEY=$(TLSROOT)/private/localhost.key
CSR=$(TLSROOT)/certs/localhost.csr
CRT=$(TLSROOT)/certs/localhost.crt
genkey: $(KEY)
certreq: $(CSR)
testcert: $(CRT)
$(CSR): $(KEY)
umask 77 ; \
/usr/bin/openssl req $(UTF8) -new -key $(KEY) -out $(CSR)
$(CRT): $(KEY)
umask 77 ; \
/usr/bin/openssl req $(UTF8) -new -key $(KEY) -x509 -days $(DAYS) -out $(CRT) $(EXTRA_FLAGS)
[root@Centos7 certs]
umask 77 ; \
/usr/bin/openssl genrsa -aes128 2048 > app.key
Generating RSA private key, 2048 bit long modulus
....................................+++
............................................+++
e is 65537 (0x10001)
Enter pass phrase:
139637690505104:error:28069065:lib(40):UI_set_result:result too small:ui_lib.c:831:You must type in 4 to 1023 characters
Enter pass phrase:
Verifying - Enter pass phrase:
umask 77 ; \
/usr/bin/openssl req -utf8 -new -key app.key -x509 -days 365 -out app.crt
Enter pass phrase for app.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:hubei
Locality Name (eg, city) [Default City]:wuhan
Organization Name (eg, company) [Default Company Ltd]:magedu
Organizational Unit Name (eg, section) []:it
Common Name (eg, your name or your server's hostname) []:www.magedu.org
Email Address []:admin@magedu.org
[root@Centos7 certs]
app.crt ca-bundle.crt make-dummy-cert renew-dummy-cert
app.key ca-bundle.trust.crt Makefile
[root@Centos7 certs]
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
89:3c:a6:35:21:46:a3:1d
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=hubei, L=wuhan, O=magedu, OU=it, CN=www.magedu.org/emailAddress=admin@magedu.org
Validity
Not Before: May 24 04:48:53 2020 GMT
Not After : May 24 04:48:53 2021 GMT
Subject: C=CN, ST=hubei, L=wuhan, O=magedu, OU=it, CN=www.magedu.org/emailAddress=admin@magedu.org
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:ca:64:c0:73:2d:59:f0:35:49:5f:1f:4b:e9:91:
5b:c4:94:18:31:3a:f0:44:53:a9:20:c7:9d:5b:46:
d8:54:7f:32:cf:6c:c0:d0:0e:a5:7a:1e:b5:f4:17:
40:65:4e:13:57:0d:cb:1c:a1:86:0e:5d:18:f4:07:
7f:d3:b2:d7:f8:82:52:77:37:70:29:57:bb:ac:fd:
8a:6b:6c:d3:55:8f:1f:66:25:16:54:77:ba:8f:f6:
2b:15:aa:59:c2:9b:3b:4a:be:9d:50:06:e7:38:54:
8c:0a:52:7c:08:38:18:17:32:fb:13:bb:51:2e:81:
6a:43:ad:88:e1:6b:6d:df:c6:21:2d:4b:9d:d9:9c:
1e:a4:8d:f3:ca:ed:10:8b:38:1b:8f:0f:c0:0d:73:
f8:a6:67:cb:6f:50:2e:73:ce:a2:56:fb:2b:e3:59:
3a:1f:65:d1:be:4b:28:84:31:69:65:13:33:2d:d8:
1f:2b:e1:9a:ba:b6:ac:06:14:d5:8b:70:d9:c8:7c:
59:c3:4f:d0:48:b7:ce:47:a3:c0:e1:e1:0b:15:e7:
e1:68:04:93:b3:17:f0:f9:c5:24:91:10:8f:36:ad:
d8:f5:8e:c2:5c:13:76:b5:64:aa:1e:56:5f:3b:37:
f0:47:15:7b:44:d5:9f:f1:97:7e:7b:77:4a:8f:1a:
db:9d
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
7F:9C:20:BD:21:CC:AB:3B:2A:46:D6:00:BC:84:47:46:90:E8:1D:73
X509v3 Authority Key Identifier:
keyid:7F:9C:20:BD:21:CC:AB:3B:2A:46:D6:00:BC:84:47:46:90:E8:1D:73
X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
41:4a:41:87:f2:c9:99:54:64:96:0c:e2:1d:8a:05:fb:c3:77:
0f:45:34:fe:3a:7e:64:3b:24:00:a3:0d:c0:12:e1:35:ae:b5:
20:8c:00:61:e6:5c:ec:dd:34:be:9e:0c:5e:2f:db:db:37:9a:
5f:52:58:e7:84:90:14:5c:61:0d:d8:91:8a:94:2a:b7:b3:04:
17:f9:38:9b:27:07:36:b1:49:5e:e3:27:ad:31:c8:12:64:85:
7f:a1:09:85:31:da:6b:21:30:50:e2:44:ee:df:66:8d:85:3c:
ce:5c:f2:8c:53:0b:a3:7c:9e:05:bf:fd:90:0e:a9:dc:0c:a5:
85:7d:69:c3:3f:96:37:56:5c:0e:a3:a0:61:0d:09:b3:c7:82:
d3:42:d5:ba:bf:b8:c7:c9:f8:6c:60:79:ed:35:d2:52:06:f9:
f1:9f:38:48:c4:6c:17:cb:54:d1:62:14:e0:34:43:67:6a:f1:
6d:d5:52:11:1a:12:5e:19:08:3c:13:90:d5:e4:f6:a1:cb:17:
d6:32:c0:cd:21:53:44:33:96:66:b1:1e:d5:cc:70:2b:2b:13:
02:21:3c:74:8e:8c:c4:57:8b:5b:94:9f:d2:85:b5:1e:20:2f:
89:e5:96:83:62:1d:ee:61:14:87:d9:c0:85:5c:3d:5e:6a:32:
1d:ce:1d:90
4.5 实战案例
4.5.1 创建CA相关目录和文件
[root@centos8 ~]
mkdir: created directory '/etc/pki/CA'
mkdir: created directory '/etc/pki/CA/certs'
mkdir: created directory '/etc/pki/CA/crl'
mkdir: created directory '/etc/pki/CA/newcerts'
mkdir: created directory '/etc/pki/CA/private'
[root@centos8 ~]
/etc/pki/CA
├── certs
├── crl
├── newcerts
└── private
4 directories, 0 files
[root@centos8 ~]
[root@centos8 ~]
index.txt和serial文件在颁发证书时需要使用,如果不存在,会出现以下错误提示
[root@centos8 ~]
/etc/pki/CA/certs/app1.crt -days 1000
Using configuration from /etc/pki/tls/openssl.cnf
140040142845760:error:02001002:system library:fopen:No such file or
directory:crypto/bio/bss_file.c:72:fopen('/etc/pki/CA/index.txt','r')
140040142845760:error:2006D080:BIO routines:BIO_new_file:no such
file:crypto/bio/bss_file.c:79:
[root@centos8 ~]
/etc/pki/CA/certs/app1.crt -days 1000
Using configuration from /etc/pki/tls/openssl.cnf
/etc/pki/CA/serial: No such file or directory
error while loading serial number
140240559408960:error:02001002:system library:fopen:No such file or
directory:crypto/bio/bss_file.c:72:fopen('/etc/pki/CA/serial','r')
140240559408960:error:2006D080:BIO routines:BIO_new_file:no such
file:crypto/bio/bss_file.c:79:
4.5.2 创建CA的私钥
[root@centos8 ~]
[root@centos8 CA]
Generating RSA private key, 2048 bit long modulus (2 primes)
............................................................+++++
.....+++++
e is 65537 (0x010001)
[root@centos8 CA]
.
├── certs
├── crl
├── index.txt
├── newcerts
└── private
└── cakey.pem
4 directories, 2 files
[root@centos8 CA]
total 4
-rw------- 1 root root 1679 May 21 09:05 cakey.pem
[root@centos8 CA]
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAvpyGHD0NWrXCWDeEp1BK6RshJItFyMAM6kntDPHMPxhzuMLC
uSubbb+afJv7TXHTpUOuVJJxu0e8vK2aTmBuhKR6/C/IFY78MQip6ELNYy1cCKrs
BHAawXC6Zi71v5VMwlPkDLcjTPMnlpQrRRJtBB+fzyMaTBvF+0GJPU6vLCqOmRB9
0jB2ElpLVWAIEHjVqpIoXPNFjYfi0yYxnjWTKy5ZyGINiSB5/kJF0epE2EWdhD3f
v3oYZcjY0uSbjN7SDWFCEz1OF1K9jiWQbUBolBEOStq607rsRJQ9AcXAlk+voHuA
6jMMiuzK8daclFxhHT8M/wVO4gxtwLAcSyRSdwIDAQABAoIBABEO3u2eBRjuFTNh
3IxAokOUOvYTRK5/iWhaL02uQfIPlSOewmBh56n9sKygJPA8VI2ArhRBes4g0GIu
QxXqiVlzgtIY0JYlUqpstQ/lEo5im87mxPJsueg/116Xq0R27wShD1KX/R/AzvUp
02l+CaWJ0vptkMfo4GHo7og/B2wzRyzqh6ZMQI236cKWLXTf588T+kkHgDVPJfUl
sU7jEQ+OHofHGrGFEWIP7jjr4KTS+Oe4Hosk3O9ef7uhpKV3gaPTkwB94PUYXR+v
xNWInmiVkfJRDI1FjNwLdxVfiEYLstKa3ncXTRNDtGCDJ1Pt+YG8Pd6i1rPdrsUK
NeGnMnECgYEA6uGm2jwA3qDOBNpQ3fTghox4RkjGHfEkab9qZc61iy8eQpBKmjcU
1N2QJ4I0qyqHKwxLZB8e/iIF4STzO3qkrWPx66sxMuEnJhcXWNJm/3etKbDFHbmQ
HU+DbDoE/nhYhsMuXB3u1q5O01S1OXAZUBgKQesN8bGXRS3ntX4tXf8CgYEAz7/k
tC5DMkRZ4j3HcpsqHBfIBpzObTIAP2d3mM2xtKz2o8XKm6sZcTlBn4SmpdN5JQyR
9sqta7QB3GSvD4jQa9alS33KIickHkAQEkWgie0IQETtBqyxEPjOKIV3nkzCFqZR
PmC54VVFmBnP0JDCdUtRLqVqq1VeILqMNp5M+4kCgYEAnCgHmSG5Zkm8jodiqh4q
w+lR8VBivvdaQR/sqeDi27UoxhJONvcV12uyckHjqESu9tTGrrruDQErrYK2Xz3r
jAddiFQZcn00XOOPNxMzPPcg3g3TDy8WfBYoBuUP+uqh2H6dLMsNxha++0te7N/1
REWnVCnk7GIocurRGN3ZZZsCgYAXv9QhVPiRkobD+lQGof5aX82aE+r1SLYGiYl+
imU6RlubtUzIJvMtomICHmP+qQI8XgeBswHIQjfEPi5VFErfSRZ0XtjwtpDGdIRh
0lvb6KD81+RQ0wUa75aBw2A9VIELnc/D1cLqI5llHe5H5YSVbBrHvllHZObxzuGg
jNA4IQKBgQCk9pjm+VsQtRLxD4mgNp/wtexBNUtuHVKCYiWilHLfbk0ytmR8qH6K
G88Ar4Q1mWU2dJdn1UVEBlp/kVC1ASrI2sK3Zj9SrJ8DB9aDUXwRmNn3Nhfzqa2/
f8vH5vmlj6EM5oUQMiVfm5v4DwosLESmXWSH9V9OaPX5FgzwtrGKew==
-----END RSA PRIVATE KEY-----
4.5.3 给CA颁发自签名证书
[root@centos8 ~]
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:beijing
Locality Name (eg, city) [Default City]:beijing
Organization Name (eg, company) [Default Company Ltd]:magedu
Organizational Unit Name (eg, section) []:devops
Common Name (eg, your name or your server's hostname) []:ca.magedu.org
Email Address []:admin@magedu.org
[root@centos8 ~]
/etc/pki/CA
├── cacert.pem
├── certs
├── crl
├── index.txt
├── newcerts
└── private
└── cakey.pem
4 directories, 3 files
[root@centos8 ~]
-----BEGIN CERTIFICATE-----
MIID+zCCAuOgAwIBAgIUXz48j2oJhLgLULPo0zennqQfrMIwDQYJKoZIhvcNAQEL
BQAwgYwxCzAJBgNVBAYTAkNOMRAwDgYDVQQIDAdiZWlqaW5nMRAwDgYDVQQHDAdi
ZWlqaW5nMQ8wDQYDVQQKDAZtYWdlZHUxDzANBgNVBAsMBmRldm9wczEWMBQGA1UE
AwwNY2EubWFnZWR1Lm9yZzEfMB0GCSqGSIb3DQEJARYQYWRtaW5AbWFnZWR1Lm9y
ZzAeFw0yMDA1MjEwMTE3MTRaFw0zMDA1MTkwMTE3MTRaMIGMMQswCQYDVQQGEwJD
TjEQMA4GA1UECAwHYmVpamluZzEQMA4GA1UEBwwHYmVpamluZzEPMA0GA1UECgwG
bWFnZWR1MQ8wDQYDVQQLDAZkZXZvcHMxFjAUBgNVBAMMDWNhLm1hZ2VkdS5vcmcx
HzAdBgkqhkiG9w0BCQEWEGFkbWluQG1hZ2VkdS5vcmcwggEiMA0GCSqGSIb3DQEB
AQUAA4IBDwAwggEKAoIBAQC+nIYcPQ1atcJYN4SnUErpGyEki0XIwAzqSe0M8cw/
GHO4wsK5K5ttv5p8m/tNcdOlQ65UknG7R7y8rZpOYG6EpHr8L8gVjvwxCKnoQs1j
LVwIquwEcBrBcLpmLvW/lUzCU+QMtyNM8yeWlCtFEm0EH5/PIxpMG8X7QYk9Tq8s
Ko6ZEH3SMHYSWktVYAgQeNWqkihc80WNh+LTJjGeNZMrLlnIYg2JIHn+QkXR6kTY
RZ2EPd+/ehhlyNjS5JuM3tINYUITPU4XUr2OJZBtQGiUEQ5K2rrTuuxElD0BxcCW
T6+ge4DqMwyK7Mrx1pyUXGEdPwz/BU7iDG3AsBxLJFJ3AgMBAAGjUzBRMB0GA1Ud
DgQWBBTNgbGBr6Yj9F+g3Zsy5cky9kg6DTAfBgNVHSMEGDAWgBTNgbGBr6Yj9F+g
3Zsy5cky9kg6DTAPBgNVHRMBAf8EBTADAQH/MA0GCSqGSIb3DQEBCwUAA4IBAQAs
CrQ9qCf5fA4darrRTtuPaRvWucPxCafUKi5R3p1I2dYBQwid5FpMn5Ad80fBdnoY
UI3/+/Z2mGp7LI5T2P5Fd1U4cQFyBRZ6wYSQKdcDG6r7KMkVoxe8azaIN8UtnUdb
qMr1C6KURluEfBDbj/4jWB+HHV7tqgjXKF/BK0/B3+7MGtHNFfznYhrynFgR8QFU
HuFkXHxvvKMyO4+564IwCyvMxwAkTBAg4w2ovBpmsF/zDhlNEaa05nACVbvv7D5u
M0alHV206fcZz9ZZgy7ZZ8B89iVtj5Fk1WfVUGD1e8Kg5Um0jM2O5WuiFyZurgOj
COrfD29YyiupDOkd1Hui
-----END CERTIFICATE-----
[root@centos8 ~]
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
5f:3e:3c:8f:6a:09:84:b8:0b:50:b3:e8:d3:37:a7:9e:a4:1f:ac:c2
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = beijing, L = beijing, O = magedu, OU = devops, CN = ca.magedu.org, emailAddress = admin@magedu.org
Validity
Not Before: May 21 01:17:14 2020 GMT
Not After : May 19 01:17:14 2030 GMT
Subject: C = CN, ST = beijing, L = beijing, O = magedu, OU = devops, CN = ca.magedu.org, emailAddress = admin@magedu.org
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:be:9c:86:1c:3d:0d:5a:b5:c2:58:37:84:a7:50:
4a:e9:1b:21:24:8b:45:c8:c0:0c:ea:49:ed:0c:f1:
cc:3f:18:73:b8:c2:c2:b9:2b:9b:6d:bf:9a:7c:9b:
fb:4d:71:d3:a5:43:ae:54:92:71:bb:47:bc:bc:ad:
9a:4e:60:6e:84:a4:7a:fc:2f:c8:15:8e:fc:31:08:
a9:e8:42:cd:63:2d:5c:08:aa:ec:04:70:1a:c1:70:
ba:66:2e:f5:bf:95:4c:c2:53:e4:0c:b7:23:4c:f3:
27:96:94:2b:45:12:6d:04:1f:9f:cf:23:1a:4c:1b:
c5:fb:41:89:3d:4e:af:2c:2a:8e:99:10:7d:d2:30:
76:12:5a:4b:55:60:08:10:78:d5:aa:92:28:5c:f3:
45:8d:87:e2:d3:26:31:9e:35:93:2b:2e:59:c8:62:
0d:89:20:79:fe:42:45:d1:ea:44:d8:45:9d:84:3d:
df:bf:7a:18:65:c8:d8:d2:e4:9b:8c:de:d2:0d:61:
42:13:3d:4e:17:52:bd:8e:25:90:6d:40:68:94:11:
0e:4a:da:ba:d3:ba:ec:44:94:3d:01:c5:c0:96:4f:
af:a0:7b:80:ea:33:0c:8a:ec:ca:f1:d6:9c:94:5c:
61:1d:3f:0c:ff:05:4e:e2:0c:6d:c0:b0:1c:4b:24:
52:77
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
CD:81:B1:81:AF:A6:23:F4:5F:A0:DD:9B:32:E5:C9:32:F6:48:3A:0D
X509v3 Authority Key Identifier:
keyid:CD:81:B1:81:AF:A6:23:F4:5F:A0:DD:9B:32:E5:C9:32:F6:48:3A:0D
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
2c:0a:b4:3d:a8:27:f9:7c:0e:1d:6a:ba:d1:4e:db:8f:69:1b:
d6:b9:c3:f1:09:a7:d4:2a:2e:51:de:9d:48:d9:d6:01:43:08:
9d:e4:5a:4c:9f:90:1d:f3:47:c1:76:7a:18:50:8d:ff:fb:f6:
76:98:6a:7b:2c:8e:53:d8:fe:45:77:55:38:71:01:72:05:16:
7a:c1:84:90:29:d7:03:1b:aa:fb:28:c9:15:a3:17:bc:6b:36:
88:37:c5:2d:9d:47:5b:a8:ca:f5:0b:a2:94:46:5b:84:7c:10:
db:8f:fe:23:58:1f:87:1d:5e:ed:aa:08:d7:28:5f:c1:2b:4f:
c1:df:ee:cc:1a:d1:cd:15:fc:e7:62:1a:f2:9c:58:11:f1:01:
54:1e:e1:64:5c:7c:6f:bc:a3:32:3b:8f:b9:eb:82:30:0b:2b:
cc:c7:00:24:4c:10:20:e3:0d:a8:bc:1a:66:b0:5f:f3:0e:19:
4d:11:a6:b4:e6:70:02:55:bb:ef:ec:3e:6e:33:46:a5:1d:5d:
b4:e9:f7:19:cf:d6:59:83:2e:d9:67:c0:7c:f6:25:6d:8f:91:
64:d5:67:d5:50:60:f5:7b:c2:a0:e5:49:b4:8c:cd:8e:e5:6b:
a2:17:26:6e:ae:03:a3:08:ea:df:0f:6f:58:ca:2b:a9:0c:e9:
1d:d4:7b:a2
[root@centos8 ~]
4.5.4 用户生成私钥和证书申请
[root@centos8 ~]
[root@centos8 ~]
Generating RSA private key, 2048 bit long modulus (2 primes)
...............+++++
.......+++++
e is 65537 (0x010001)
[root@centos8 ~]
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAsRVfHE3adsNc5lTetzwcpCLS6lgcL4nzSI19sBfzWr4duo2W
zUR/UE8Tl6aJeiKz/htMHf/MuNsyEURIpGUflVGmrafEt/+sEWHRSUOmSxJQYXf0
VtDqmd72MtdJlJN5rM3iQBst27VGteXP4TveZxnKuqH/CWPe45JjYib72eCnTTkk
RT4ESQ5JrzJMVxoQ6AqvH/0qyRpcQjwk9LPekhYbQwgIk2jckwCdRE937Rf2SjED
MV0fjGPiSe3MRT14gYIIwB16weFoKNlWboDxQa1EHxS19JoF/Oulc9XiVCdEVXkY
3NgQ13KjTClqiPvt2tgLwHzoz0O/SiBsAqkUZwIDAQABAoIBACy7dFInDHeRtCbu
62+n/Kgtr8/IwB32IAGE1GomMrAKdGIKoDxsACkeQJm/VN0IZSVcaebuFh3gKQ6Z
jCwS616ByLP3PEcqi6G8buyt7RTrpGhqr8s6bPi/jLudDJY+hq7zNyLweq4UZa9P
RSrlP7IVntN0VoNduhEMipRhup73qD29mDGAY/irhr5Nlu5hgpvHPaOFQCslmeUl
zJtpgHxyqDQ3GzzcgEpRqvN0rSsex2ccsgSWZrKkT6glcmWKAh4hVaNxzePdJbS9
QVfIhv5Y0EPhyqY0LDjCxtdf2/R0PSZyLrZNNyA0X8vbayzGLU0Xc57tFZKqQSK6
oXCXSlkCgYEA3rkoFmwJhWXN0rxpWPFAGksWRr2A8mBd/op5+96S1xKCoARMJexG
31DsC+L8ueazBTEqRt+EZQvKd9b63jkLpfBWI6eByWO7Z5zeQc7M7AD4BEoxjx1B
6RaznBcbMt76lMZfjr+sv4cdjBwxV+LLWx/yOi2WWFBmdLP6LW2orWsCgYEAy4qP
HUuMpXftO63T3U0Ckig08kcCFABsAEZuLnL0kq/h10Vc7ot85cGYCQkf42dWIpFJ
Bq4IvRWHdTxMiHepEVTrEzZGpz6GWNiCwcjigfARevQjbPvzBU2IAUmyu2QJsqAq
m9/HofMz687ycY/S7KWTxfB5uU7SWKCy/dkTl/UCgYBVmmrK+2lJaVCLj7kZ41fV
A0kjlVCLV/iojcbGxMxBd67XG++8n6y5xluDUhH6za2+8B+kr+IuCDMgjnNLmDde
5xnkiEw9AGUWNNfECVz/1Ht/Apk7vW4IzZ3o/4SHr+Y16mzt68PUtXTo1iks81Ff
y86JB96CQRyv/EDK1xv+0wKBgBk/7RUTRDVatUFMBRZU8Va0Si0sBeP5UWyPUCfO
9uwjiX6tCiRFhY7y/ytPyHbrYNIU99wuRsM+Inm2qz/aqEyQHkFZ4FXq+buX0FC9
3OuFnoWEN8jTUIh937tZKyT3+gQAvohrsFY012IPYCAaWW4l9Dj/5fnI/2sjNFEt
VrLpAoGAZXR6WMX3VBsMfNsdv8O3KjQvHxpd++Btx4WukCjRMyEoasXKPpDfVIxQ
yXqHAJgTgxiOK+bTS0qTLPMHTZNO9MEELRpd8G8JhnXd6NhKel3Iu9WPgPgsYeaw
cYLGALw+2ZO5Zw4kWK7e6GvA64LiFdyJY5HKHka8Q75lvFrPriQ=
-----END RSA PRIVATE KEY-----
[root@centos8 ~]
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:beijing
Locality Name (eg, city) [Default City]:bj
Organization Name (eg, company) [Default Company Ltd]:magedu
Organizational Unit Name (eg, section) []:it
Common Name (eg, your name or your server's hostname) []:app1.magedu.org
Email Address []:root@magedu.org
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:.
[root@centos8 ~]
total 8
-rw-r--r-- 1 root root 1045 May 21 09:34 app1.csr
-rw------- 1 root root 1675 May 21 09:31 app1.key
默认有三项内容必须和CA一致:国家,省份,组织,如果不同,会出现下面的提示
[root@centos8 ~]
/etc/pki/CA/certs/app2.crt
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
The stateOrProvinceName field is different between
CA certificate (beijing) and the request (hubei)
4.5.5 CA颁发证书
[root@centos8 ~]
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 15 (0xf)
Validity
Not Before: May 21 01:50:22 2020 GMT
Not After : Feb 15 01:50:22 2023 GMT
Subject:
countryName = CN
stateOrProvinceName = beijing
organizationName = magedu
organizationalUnitName = it
commonName = app1.magedu.org
emailAddress = root@magedu.org
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
98:6F:F9:85:BF:03:75:91:89:78:A8:2F:B0:11:14:13:3A:70:09:D1
X509v3 Authority Key Identifier:
keyid:CD:81:B1:81:AF:A6:23:F4:5F:A0:DD:9B:32:E5:C9:32:F6:48:3A:0D
Certificate is to be certified until Feb 15 01:50:22 2023 GMT (1000 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@centos8 ~]
/etc/pki/CA/
├── cacert.pem
├── certs
│ └── app1.crt
├── crl
├── index.txt
├── index.txt.attr
├── index.txt.old
├── newcerts
│ └── 0F.pem
├── private
│ └── cakey.pem
├── serial
└── serial.old
4 directories, 9 files
4.5.6 查看证书
[root@centos8 ~]
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 15 (0xf)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=beijing, L=beijing, O=magedu, OU=devops, CN=ca.magedu.org/emailAddress=admin@magedu.org
Validity
Not Before: May 21 01:50:22 2020 GMT
Not After : Feb 15 01:50:22 2023 GMT
Subject: C=CN, ST=beijing, O=magedu, OU=it, CN=app1.magedu.org/emailAddress=root@magedu.org
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:b1:15:5f:1c:4d:da:76:c3:5c:e6:54:de:b7:3c:
1c:a4:22:d2:ea:58:1c:2f:89:f3:48:8d:7d:b0:17:
f3:5a:be:1d:ba:8d:96:cd:44:7f:50:4f:13:97:a6:
89:7a:22:b3:fe:1b:4c:1d:ff:cc:b8:db:32:11:44:
48:a4:65:1f:95:51:a6:ad:a7:c4:b7:ff:ac:11:61:
d1:49:43:a6:4b:12:50:61:77:f4:56:d0:ea:99:de:
f6:32:d7:49:94:93:79:ac:cd:e2:40:1b:2d:db:b5:
46:b5:e5:cf:e1:3b:de:67:19:ca:ba:a1:ff:09:63:
de:e3:92:63:62:26:fb:d9:e0:a7:4d:39:24:45:3e:
04:49:0e:49:af:32:4c:57:1a:10:e8:0a:af:1f:fd:
2a:c9:1a:5c:42:3c:24:f4:b3:de:92:16:1b:43:08:
08:93:68:dc:93:00:9d:44:4f:77:ed:17:f6:4a:31:
03:31:5d:1f:8c:63:e2:49:ed:cc:45:3d:78:81:82:
08:c0:1d:7a:c1:e1:68:28:d9:56:6e:80:f1:41:ad:
44:1f:14:b5:f4:9a:05:fc:eb:a5:73:d5:e2:54:27:
44:55:79:18:dc:d8:10:d7:72:a3:4c:29:6a:88:fb:
ed:da:d8:0b:c0:7c:e8:cf:43:bf:4a:20:6c:02:a9:
14:67
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
98:6F:F9:85:BF:03:75:91:89:78:A8:2F:B0:11:14:13:3A:70:09:D1
X509v3 Authority Key Identifier:
keyid:CD:81:B1:81:AF:A6:23:F4:5F:A0:DD:9B:32:E5:C9:32:F6:48:3A:0D
Signature Algorithm: sha256WithRSAEncryption
60:27:00:48:59:79:ab:00:48:9b:a7:18:42:27:b0:bc:43:3f:
6a:56:99:64:6b:0b:00:63:76:68:b5:a3:fb:df:25:c0:4e:15:
5b:0b:b4:b0:8b:56:59:57:c5:65:f5:7a:d8:33:42:ce:60:56:
ef:be:84:db:d7:e9:fe:11:ec:23:61:0e:15:66:d6:8a:da:94:
2a:d9:22:d3:29:70:0f:3a:b6:00:52:63:91:1e:16:67:13:73:
24:3b:b5:ab:c2:85:fe:20:bb:e3:ac:e8:d1:4a:a6:f0:0e:e3:
07:bf:36:b6:3d:2a:ef:a2:2f:bf:2d:8a:29:b0:0e:37:fa:8d:
6b:7a:44:ff:08:8d:69:d5:07:c6:dd:98:2a:95:f2:02:87:cd:
c0:02:46:eb:c1:19:9f:7d:11:31:66:95:2d:f6:f5:d9:40:81:
af:8e:45:7c:ae:79:3c:f9:55:42:29:38:47:8a:89:f5:18:76:
9b:cf:9b:b9:df:f0:df:0d:2a:89:73:96:76:04:a2:31:ff:58:
64:3a:f4:58:b9:ee:0d:b4:f9:4b:a2:c1:4b:49:8f:f0:90:df:
68:2f:2f:dd:96:06:55:4c:39:a2:53:c7:37:b6:eb:26:2f:78:
fd:1d:16:7d:af:51:c7:a0:90:a0:aa:30:70:4d:64:3a:f2:2c:
83:29:f2:03
-----BEGIN CERTIFICATE-----
MIID+jCCAuKgAwIBAgIBDzANBgkqhkiG9w0BAQsFADCBjDELMAkGA1UEBhMCQ04x
EDAOBgNVBAgMB2JlaWppbmcxEDAOBgNVBAcMB2JlaWppbmcxDzANBgNVBAoMBm1h
Z2VkdTEPMA0GA1UECwwGZGV2b3BzMRYwFAYDVQQDDA1jYS5tYWdlZHUub3JnMR8w
HQYJKoZIhvcNAQkBFhBhZG1pbkBtYWdlZHUub3JnMB4XDTIwMDUyMTAxNTAyMloX
DTIzMDIxNTAxNTAyMlowdzELMAkGA1UEBhMCQ04xEDAOBgNVBAgMB2JlaWppbmcx
DzANBgNVBAoMBm1hZ2VkdTELMAkGA1UECwwCaXQxGDAWBgNVBAMMD2FwcDEubWFn
ZWR1Lm9yZzEeMBwGCSqGSIb3DQEJARYPcm9vdEBtYWdlZHUub3JnMIIBIjANBgkq
hkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAsRVfHE3adsNc5lTetzwcpCLS6lgcL4nz
SI19sBfzWr4duo2WzUR/UE8Tl6aJeiKz/htMHf/MuNsyEURIpGUflVGmrafEt/+s
EWHRSUOmSxJQYXf0VtDqmd72MtdJlJN5rM3iQBst27VGteXP4TveZxnKuqH/CWPe
45JjYib72eCnTTkkRT4ESQ5JrzJMVxoQ6AqvH/0qyRpcQjwk9LPekhYbQwgIk2jc
kwCdRE937Rf2SjEDMV0fjGPiSe3MRT14gYIIwB16weFoKNlWboDxQa1EHxS19JoF
/Oulc9XiVCdEVXkY3NgQ13KjTClqiPvt2tgLwHzoz0O/SiBsAqkUZwIDAQABo3sw
eTAJBgNVHRMEAjAAMCwGCWCGSAGG+EIBDQQfFh1PcGVuU1NMIEdlbmVyYXRlZCBD
ZXJ0aWZpY2F0ZTAdBgNVHQ4EFgQUmG/5hb8DdZGJeKgvsBEUEzpwCdEwHwYDVR0j
BBgwFoAUzYGxga+mI/RfoN2bMuXJMvZIOg0wDQYJKoZIhvcNAQELBQADggEBAGAn
AEhZeasASJunGEInsLxDP2pWmWRrCwBjdmi1o/vfJcBOFVsLtLCLVllXxWX1etgz
Qs5gVu++hNvX6f4R7CNhDhVm1oralCrZItMpcA86tgBSY5EeFmcTcyQ7tavChf4g
u+Os6NFKpvAO4we/NrY9Ku+iL78tiimwDjf6jWt6RP8IjWnVB8bdmCqV8gKHzcAC
RuvBGZ99ETFmlS329dlAga+ORXyueTz5VUIpOEeKifUYdpvPm7nf8N8NKolzlnYE
ojH/WGQ69Fi57g20+UuiwUtJj/CQ32gvL92WBlVMOaJTxze26yYveP0dFn2vUceg
kKCqMHBNZDryLIMp8gM=
-----END CERTIFICATE-----
[root@centos8 ~]
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 15 (0xf)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = beijing, L = beijing, O = magedu, OU = devops, CN = ca.magedu.org, emailAddress = admin@magedu.org
Validity
Not Before: May 21 01:50:22 2020 GMT
Not After : Feb 15 01:50:22 2023 GMT
Subject: C = CN, ST = beijing, O = magedu, OU = it, CN = app1.magedu.org, emailAddress = root@magedu.org
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:b1:15:5f:1c:4d:da:76:c3:5c:e6:54:de:b7:3c:
1c:a4:22:d2:ea:58:1c:2f:89:f3:48:8d:7d:b0:17:
f3:5a:be:1d:ba:8d:96:cd:44:7f:50:4f:13:97:a6:
89:7a:22:b3:fe:1b:4c:1d:ff:cc:b8:db:32:11:44:
48:a4:65:1f:95:51:a6:ad:a7:c4:b7:ff:ac:11:61:
d1:49:43:a6:4b:12:50:61:77:f4:56:d0:ea:99:de:
f6:32:d7:49:94:93:79:ac:cd:e2:40:1b:2d:db:b5:
46:b5:e5:cf:e1:3b:de:67:19:ca:ba:a1:ff:09:63:
de:e3:92:63:62:26:fb:d9:e0:a7:4d:39:24:45:3e:
04:49:0e:49:af:32:4c:57:1a:10:e8:0a:af:1f:fd:
2a:c9:1a:5c:42:3c:24:f4:b3:de:92:16:1b:43:08:
08:93:68:dc:93:00:9d:44:4f:77:ed:17:f6:4a:31:
03:31:5d:1f:8c:63:e2:49:ed:cc:45:3d:78:81:82:
08:c0:1d:7a:c1:e1:68:28:d9:56:6e:80:f1:41:ad:
44:1f:14:b5:f4:9a:05:fc:eb:a5:73:d5:e2:54:27:
44:55:79:18:dc:d8:10:d7:72:a3:4c:29:6a:88:fb:
ed:da:d8:0b:c0:7c:e8:cf:43:bf:4a:20:6c:02:a9:
14:67
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
98:6F:F9:85:BF:03:75:91:89:78:A8:2F:B0:11:14:13:3A:70:09:D1
X509v3 Authority Key Identifier:
keyid:CD:81:B1:81:AF:A6:23:F4:5F:A0:DD:9B:32:E5:C9:32:F6:48:3A:0D
Signature Algorithm: sha256WithRSAEncryption
60:27:00:48:59:79:ab:00:48:9b:a7:18:42:27:b0:bc:43:3f:
6a:56:99:64:6b:0b:00:63:76:68:b5:a3:fb:df:25:c0:4e:15:
5b:0b:b4:b0:8b:56:59:57:c5:65:f5:7a:d8:33:42:ce:60:56:
ef:be:84:db:d7:e9:fe:11:ec:23:61:0e:15:66:d6:8a:da:94:
2a:d9:22:d3:29:70:0f:3a:b6:00:52:63:91:1e:16:67:13:73:
24:3b:b5:ab:c2:85:fe:20:bb:e3:ac:e8:d1:4a:a6:f0:0e:e3:
07:bf:36:b6:3d:2a:ef:a2:2f:bf:2d:8a:29:b0:0e:37:fa:8d:
6b:7a:44:ff:08:8d:69:d5:07:c6:dd:98:2a:95:f2:02:87:cd:
c0:02:46:eb:c1:19:9f:7d:11:31:66:95:2d:f6:f5:d9:40:81:
af:8e:45:7c:ae:79:3c:f9:55:42:29:38:47:8a:89:f5:18:76:
9b:cf:9b:b9:df:f0:df:0d:2a:89:73:96:76:04:a2:31:ff:58:
64:3a:f4:58:b9:ee:0d:b4:f9:4b:a2:c1:4b:49:8f:f0:90:df:
68:2f:2f:dd:96:06:55:4c:39:a2:53:c7:37:b6:eb:26:2f:78:
fd:1d:16:7d:af:51:c7:a0:90:a0:aa:30:70:4d:64:3a:f2:2c:
83:29:f2:03
[root@centos8 ~]
issuer=C = CN, ST = beijing, L = beijing, O = magedu, OU = devops, CN = ca.magedu.org, emailAddress = admin@magedu.org
[root@centos8 ~]
[root@centos8 ~]
notBefore=May 21 01:50:22 2020 GMT
notAfter=Feb 15 01:50:22 2023 GMT
[root@centos8 ~]
serial=0F
[root@centos8 ~]
Using configuration from /etc/pki/tls/openssl.cnf
0F=Valid (V)
[root@centos8 ~]
V 230215015022Z 0F unknown /C=CN/ST=beijing/O=magedu/OU=it/CN=app1.magedu.org/emailAddress=root@magedu.org
[root@centos8 ~]
[root@centos8 ~]
10
[root@centos8 ~]
0F
4.5.7 将证书相关文件发送到用户端使用
[root@centos8 ~]
[root@centos8 ~]
/data/app1/
├── app1.crt
├── app1.csr
└── app1.key
0 directories, 3 files
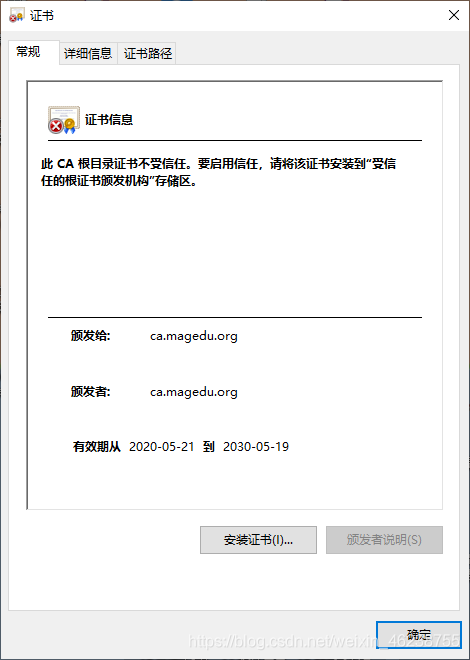
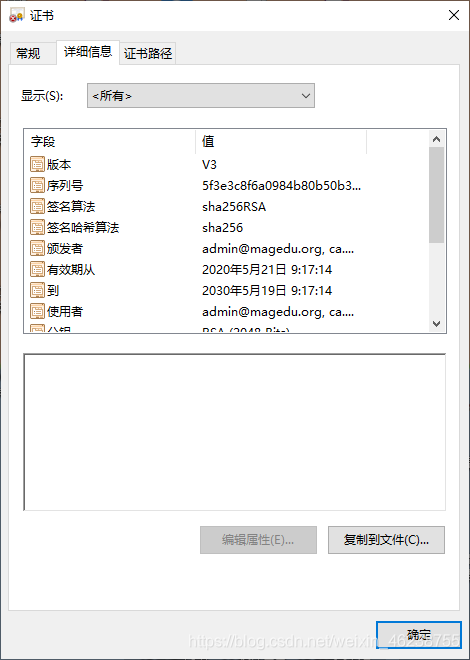
4.5.8 证书的信任
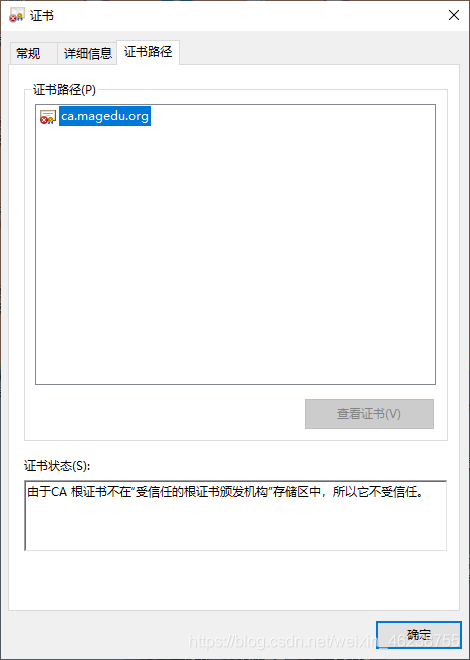
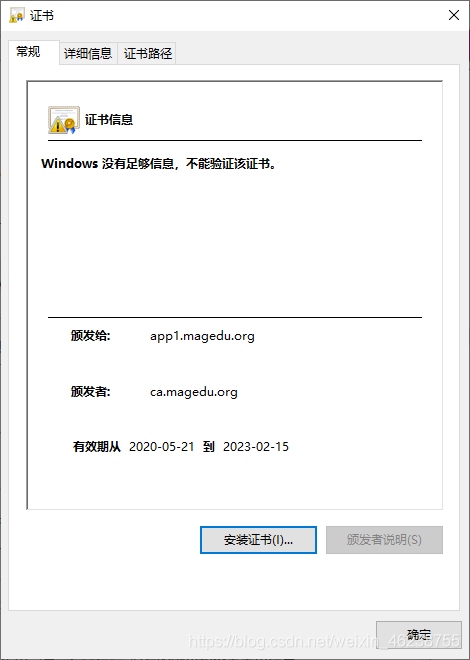
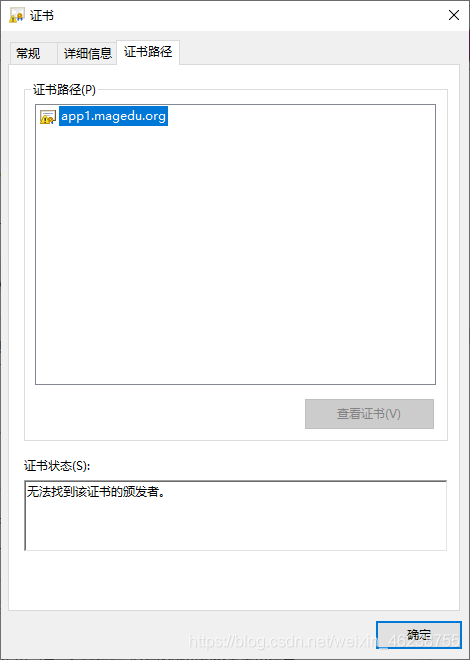
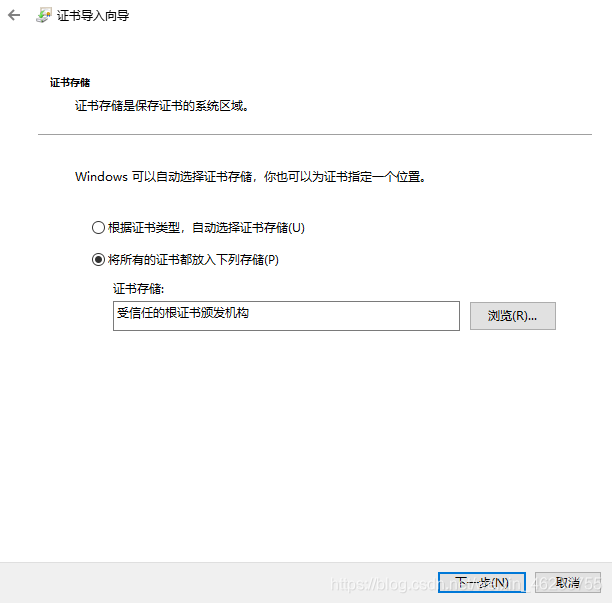
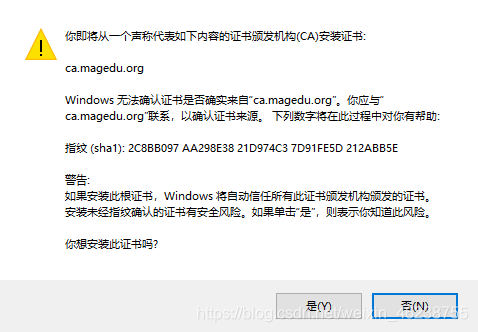
默认生成的证书,在windows上是不被信任的,可以通过下面的操作实现信任
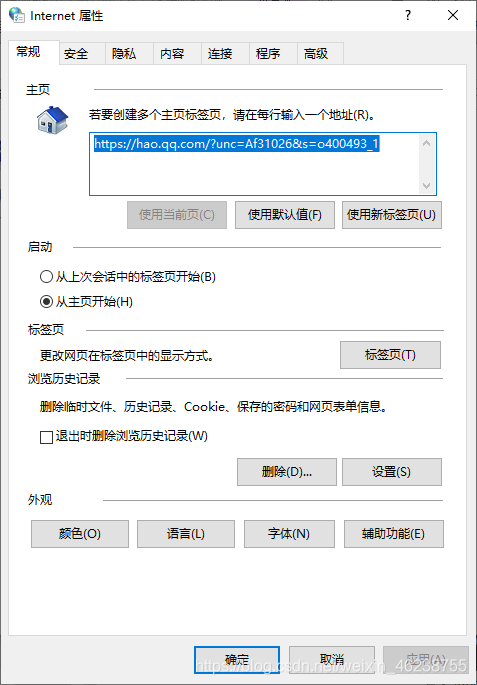
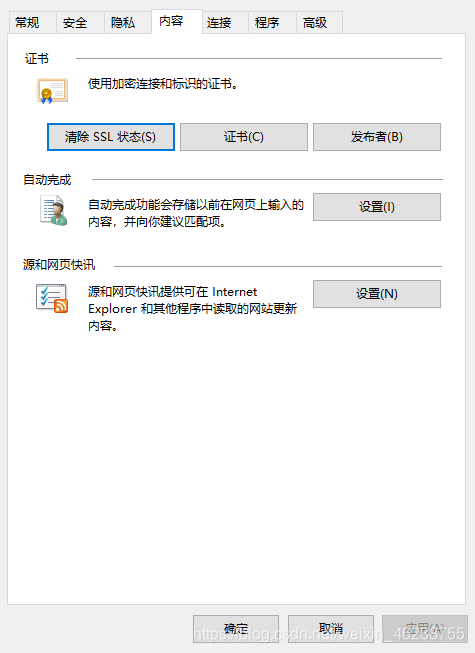
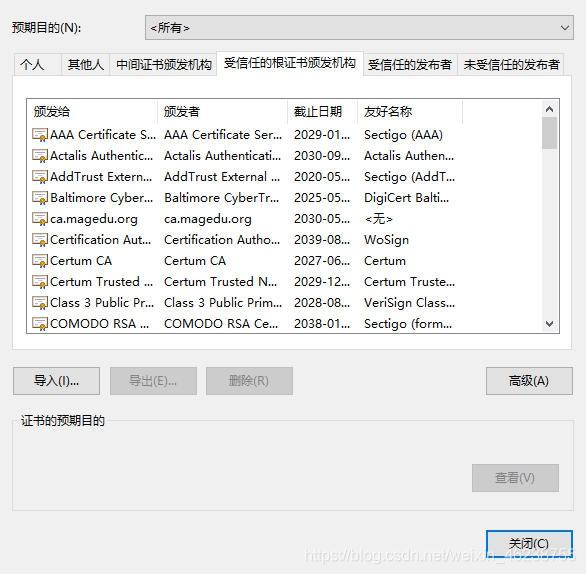
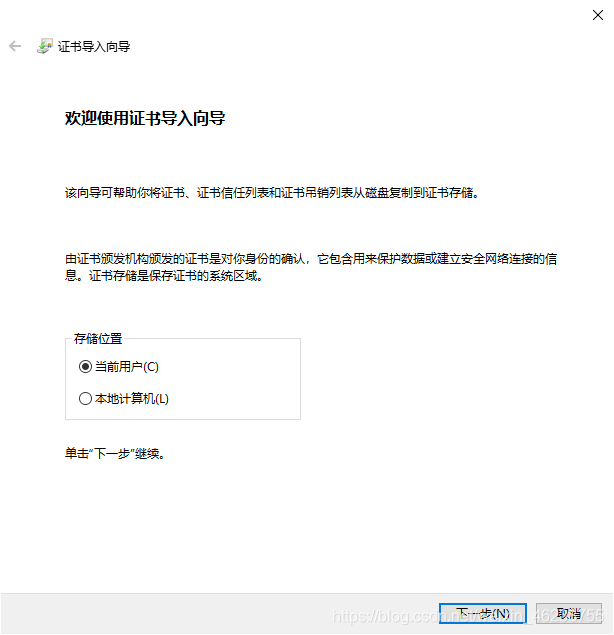
打开internet属性
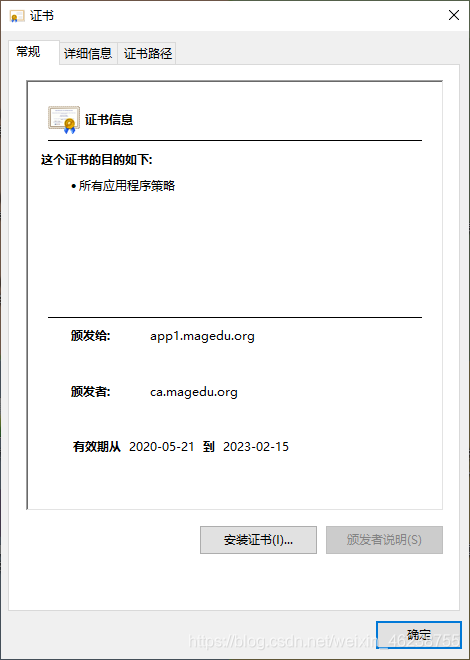
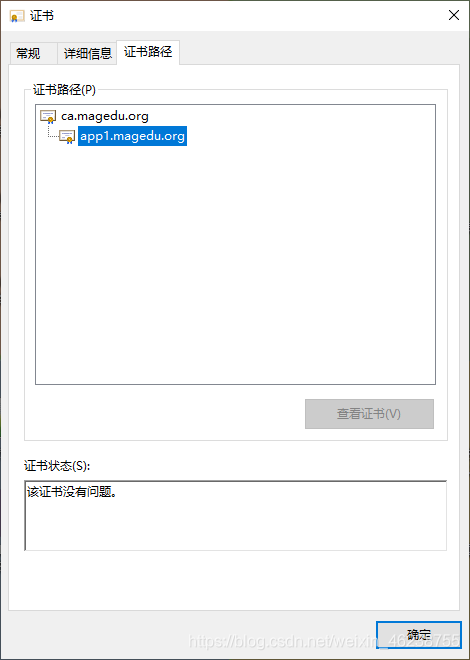
4.5.9 证书的吊销
[root@centos8 ~]
Using configuration from /etc/pki/tls/openssl.cnf
Revoking Certificate 11.
Data Base Updated
[root@centos8 ~]
Using configuration from /etc/pki/tls/openssl.cnf
11=Revoked (R)
[root@centos8 ~]
V 230214062101Z 0F unknown
/C=CN/ST=beijing/O=magedu/OU=it/CN=app1.magedu.org/emailAddress=root@magedu.org
V 210520064452Z 10 unknown
/C=CN/ST=hubei/L=wuhan/O=wangedu/OU=sales/CN=app2.wangedu.org/emailAddress=admin
@wangedu.org
R 210520065000Z 200520065821Z 11 unknown
/C=CN/ST=hubei/L=wuhan/O=wangedu/OU=sales/CN=app2.wangedu.org/emailAddress=admin
@wangedu.org
4.5.10 生成证书吊销列表文件
[root@centos8 ~]
Using configuration from /etc/pki/tls/openssl.cnf
/etc/pki/CA/crlnumber: No such file or directory
error while loading CRL number
140511895181120:error:02001002:system library:fopen:No such file or
directory:crypto/bio/bss_file.c:72:fopen('/etc/pki/CA/crlnumber','r')
140511895181120:error:2006D080:BIO routines:BIO_new_file:no such
file:crypto/bio/bss_file.c:79:
[root@centos8 ~]
[root@centos8 ~]
Using configuration from /etc/pki/tls/openssl.cnf
[root@centos8 ~]
02
[root@centos8 ~]
-----BEGIN X509 CRL-----
MIIB/DCB5QIBATANBgkqhkiG9w0BAQsFADCBjDELMAkGA1UEBhMCQ04xEDAOBgNV
BAgMB2JlaWppbmcxEDAOBgNVBAcMB2JlaWppbmcxDzANBgNVBAoMBm1hZ2VkdTEP
MA0GA1UECwwGZGV2b3BzMRYwFAYDVQQDDA1jYS5tYWdlZHUub3JnMR8wHQYJKoZI
hvcNAQkBFhBhZG1pbkBtYWdlZHUub3JnFw0yMDA1MjAwNzAzNTdaFw0yMDA2MTkw
NzAzNTdaMBQwEgIBERcNMjAwNTIwMDY1ODIxWqAOMAwwCgYDVR0UBAMCAQEwDQYJ
KoZIhvcNAQELBQADggEBAJURX2tzn05nPkxynNwYLimWUIdgQn9UZxZaDmbQg9j5
5xmhXV+5Tz6qV8gI4+sPwyUGXRcURDHDEW2SCIK6s/Cmx9sYNZRsNpp3sQKYBM6e
NbtIh1fIGx3927bxPwNc7Lbq6fHYL349RUOgcjI9oKS8TU/LdIzlofVVQdzFqEda
Fb/HLHOp3/nhuuH2WHR9nb6jNCX6a8qLUA+M0eEGMSqsLv+3lqmyZ9F7GE97I1lG
KW/iyJWlu5Ogjummp241J+bmuxyZLVqsd5dOywIP8kZpGQJq+Ga4uUMGY9CvR15M
y7JW6tZnJVQnw/29jNWhIEsrcn3NErWvg1R7ljjW5g0=
-----END X509 CRL-----
[root@centos8 ~]
Certificate Revocation List (CRL):
Version 2 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = beijing, L = beijing, O = magedu, OU = devops, CN =
ca.magedu.org, emailAddress = admin@magedu.org
Last Update: May 20 07:03:57 2020 GMT
Next Update: Jun 19 07:03:57 2020 GMT
CRL extensions:
X509v3 CRL Number:
1
Revoked Certificates:
Serial Number: 11
Revocation Date: May 20 06:58:21 2020 GMT
Signature Algorithm: sha256WithRSAEncryption
95:11:5f:6b:73:9f:4e:67:3e:4c:72:9c:dc:18:2e:29:96:50:
87:60:42:7f:54:67:16:5a:0e:66:d0:83:d8:f9:e7:19:a1:5d:
5f:b9:4f:3e:aa:57:c8:08:e3:eb:0f:c3:25:06:5d:17:14:44:
31:c3:11:6d:92:08:82:ba:b3:f0:a6:c7:db:18:35:94:6c:36:
9a:77:b1:02:98:04:ce:9e:35:bb:48:87:57:c8:1b:1d:fd:db:
b6:f1:3f:03:5c:ec:b6:ea:e9:f1:d8:2f:7e:3d:45:43:a0:72:
32:3d:a0:a4:bc:4d:4f:cb:74:8c:e5:a1:f5:55:41:dc:c5:a8:
47:5a:15:bf:c7:2c:73:a9:df:f9:e1:ba:e1:f6:58:74:7d:9d:
be:a3:34:25:fa:6b:ca:8b:50:0f:8c:d1:e1:06:31:2a:ac:2e:
ff:b7:96:a9:b2:67:d1:7b:18:4f:7b:23:59:46:29:6f:e2:c8:
95:a5:bb:93:a0:8e:e9:a6:a7:6e:35:27:e6:e6:bb:1c:99:2d:
5a:ac:77:97:4e:cb:02:0f:f2:46:69:19:02:6a:f8:66:b8:b9:
43:06:63:d0:af:47:5e:4c:cb:b2:56:ea:d6:67:25:54:27:c3:
fd:bd:8c:d5:a1:20:4b:2b:72:7d:cd:12:b5:af:83:54:7b:96:
38:d6:e6:0d
[root@centos8 ~]
本文内容由网友自发贡献,版权归原作者所有,本站不承担相应法律责任。如您发现有涉嫌抄袭侵权的内容,请联系:hwhale#tublm.com(使用前将#替换为@)