问题现象
今天一上班同事反应虚拟平台登录不了了
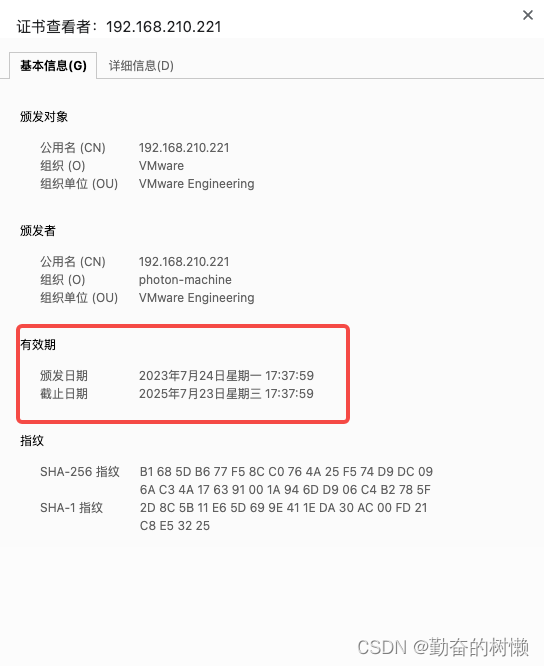
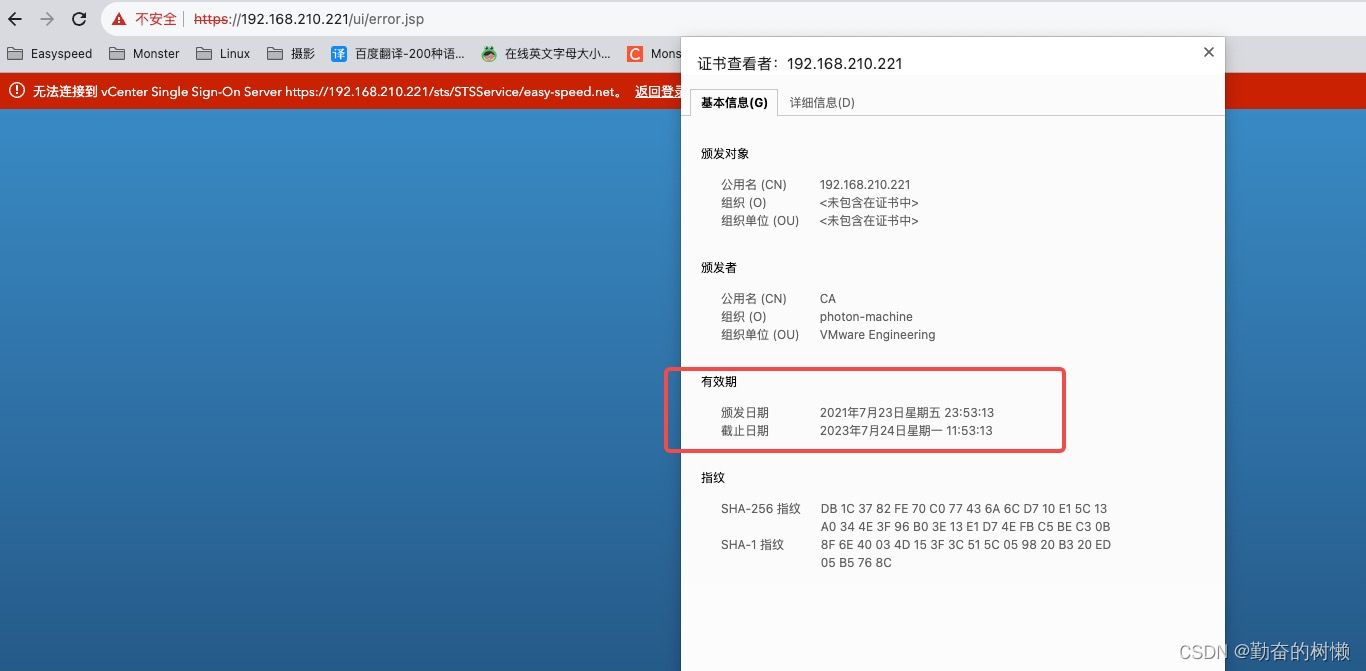
验证功能正常,输入正确密码后跳转如下错误界面,查看证书可以看见证书今天要过期了
但是当时还没到11:53:13,却已经用不了了
原因:从vCenter 6.5 Update2 (GA Date : 2018 年5 ⽉3 号) 及后⾯的版本,VC ⾃带的VMCA 签发的证书,有效期均为2 年。
解决过程
官方提示:
实操:
1.官网下载证书检测文件checksts.py:https://kb.vmware.com/s/article/79248?lang=en_us
2.使用root账户通过ssh登录,输入shell切换到命令行
Last login: Mon Jul 24 09:23:08 2023 from 192.168.159.154
Connected to service
* List APIs: "help api list"
* List Plugins: "help pi list"
* Launch BASH: "shell"
Command> shell
Shell access is granted to root
3.将checksts.py文件上传到/tmp目录下(懒的话可以直接在/tmp将下面新建个checksts.py文件,将下面代粘贴进去)
#!/opt/vmware/bin/python
"""
Copyright 2020-2022 VMware, Inc. All rights reserved. -- VMware Confidential
Author: Keenan Matheny (keenanm@vmware.com)
"""
##### BEGIN IMPORTS #####
import os
import sys
import json
import subprocess
import re
import pprint
import ssl
from datetime import datetime, timedelta
import textwrap
from codecs import encode, decode
import subprocess
from time import sleep
try:
# Python 3 hack.
import urllib.request as urllib2
import urllib.parse as urlparse
except ImportError:
import urllib2
import urlparse
sys.path.append(os.environ['VMWARE_PYTHON_PATH'])
from cis.defaults import def_by_os
sys.path.append(os.path.join(os.environ['VMWARE_CIS_HOME'],
def_by_os('vmware-vmafd/lib64', 'vmafdd')))
import vmafd
from OpenSSL.crypto import (load_certificate, dump_privatekey, dump_certificate, X509, X509Name, PKey)
from OpenSSL.crypto import (TYPE_DSA, TYPE_RSA, FILETYPE_PEM, FILETYPE_ASN1 )
today = datetime.now()
today = today.strftime("%d-%m-%Y")
vcsa_kblink = "https://kb.vmware.com/s/article/76719"
win_kblink = "https://kb.vmware.com/s/article/79263"
##### END IMPORTS #####
class parseCert( object ):
# Certificate parsing
def format_subject_issuer(self, x509name):
items = []
for item in x509name.get_components():
items.append('%s=%s' % (decode(item[0],'utf-8'), decode(item[1],'utf-8')))
return ", ".join(items)
def format_asn1_date(self, d):
return datetime.strptime(decode(d,'utf-8'), '%Y%m%d%H%M%SZ').strftime("%Y-%m-%d %H:%M:%S GMT")
def merge_cert(self, extensions, certificate):
z = certificate.copy()
z.update(extensions)
return z
def __init__(self, certdata):
built_cert = certdata
self.x509 = load_certificate(FILETYPE_PEM, built_cert)
keytype = self.x509.get_pubkey().type()
keytype_list = {TYPE_RSA:'rsaEncryption', TYPE_DSA:'dsaEncryption', 408:'id-ecPublicKey'}
extension_list = ["extendedKeyUsage",
"keyUsage",
"subjectAltName",
"subjectKeyIdentifier",
"authorityKeyIdentifier"]
key_type_str = keytype_list[keytype] if keytype in keytype_list else 'other'
certificate = {}
extension = {}
for i in range(self.x509.get_extension_count()):
critical = 'critical' if self.x509.get_extension(i).get_critical() else ''
if decode(self.x509.get_extension(i).get_short_name(),'utf-8') in extension_list:
extension[decode(self.x509.get_extension(i).get_short_name(),'utf-8')] = self.x509.get_extension(i).__str__()
certificate = {'Thumbprint': decode(self.x509.digest('sha1'),'utf-8'), 'Version': self.x509.get_version(),
'SignatureAlg' : decode(self.x509.get_signature_algorithm(),'utf-8'), 'Issuer' :self.format_subject_issuer(self.x509.get_issuer()),
'Valid From' : self.format_asn1_date(self.x509.get_notBefore()), 'Valid Until' : self.format_asn1_date(self.x509.get_notAfter()),
'Subject' : self.format_subject_issuer(self.x509.get_subject())}
combined = self.merge_cert(extension,certificate)
cert_output = json.dumps(combined)
self.subjectAltName = combined.get('subjectAltName')
self.subject = combined.get('Subject')
self.validfrom = combined.get('Valid From')
self.validuntil = combined.get('Valid Until')
self.thumbprint = combined.get('Thumbprint')
self.subjectkey = combined.get('subjectKeyIdentifier')
self.authkey = combined.get('authorityKeyIdentifier')
self.combined = combined
class parseSts( object ):
def __init__(self):
self.processed = []
self.results = {}
self.results['expired'] = {}
self.results['expired']['root'] = []
self.results['expired']['leaf'] = []
self.results['valid'] = {}
self.results['valid']['root'] = []
self.results['valid']['leaf'] = []
def get_certs(self,force_refresh):
urllib2.getproxies = lambda: {}
vmafd_client = vmafd.client('localhost')
domain_name = vmafd_client.GetDomainName()
dc_name = vmafd_client.GetAffinitizedDC(domain_name, force_refresh)
if vmafd_client.GetPNID() == dc_name:
url = (
'http://localhost:7080/idm/tenant/%s/certificates?scope=TENANT'
% domain_name)
else:
url = (
'https://%s/idm/tenant/%s/certificates?scope=TENANT'
% (dc_name,domain_name))
return json.loads(urllib2.urlopen(url).read().decode('utf-8'))
def check_cert(self,certificate):
cert = parseCert(certificate)
certdetail = cert.combined
# Attempt to identify what type of certificate it is
if cert.authkey:
cert_type = "leaf"
else:
cert_type = "root"
# Try to only process a cert once
if cert.thumbprint not in self.processed:
# Date conversion
self.processed.append(cert.thumbprint)
exp = cert.validuntil.split()[0]
conv_exp = datetime.strptime(exp, '%Y-%m-%d')
exp = datetime.strftime(conv_exp, '%d-%m-%Y')
now = datetime.strptime(today, '%d-%m-%Y')
exp_date = datetime.strptime(exp, '%d-%m-%Y')
# Get number of days until it expires
diff = exp_date - now
certdetail['daysUntil'] = diff.days
# Sort expired certs into leafs and roots, put the rest in goodcerts.
if exp_date <= now:
self.results['expired'][cert_type].append(certdetail)
else:
self.results['valid'][cert_type].append(certdetail)
def execute(self):
json = self.get_certs(force_refresh=False)
for item in json:
for certificate in item['certificates']:
self.check_cert(certificate['encoded'])
return self.results
def main():
warning = False
warningmsg = '''
WARNING!
You have expired STS certificates. Please follow the KB corresponding to your OS:
VCSA: %s
Windows: %s
''' % (vcsa_kblink, win_kblink)
parse_sts = parseSts()
results = parse_sts.execute()
valid_count = len(results['valid']['leaf']) + len(results['valid']['root'])
expired_count = len(results['expired']['leaf']) + len(results['expired']['root'])
#### Display Valid ####
print("\n%s VALID CERTS\n================" % valid_count)
print("\n\tLEAF CERTS:\n")
if len(results['valid']['leaf']) > 0:
for cert in results['valid']['leaf']:
print("\t[] Certificate %s will expire in %s days (%s years)." % (cert['Thumbprint'], cert['daysUntil'], round(cert['daysUntil']/365)))
else:
print("\tNone")
print("\n\tROOT CERTS:\n")
if len(results['valid']['root']) > 0:
for cert in results['valid']['root']:
print("\t[] Certificate %s will expire in %s days (%s years)." % (cert['Thumbprint'], cert['daysUntil'], round(cert['daysUntil']/365)))
else:
print("\tNone")
#### Display expired ####
print("\n%s EXPIRED CERTS\n================" % expired_count)
print("\n\tLEAF CERTS:\n")
if len(results['expired']['leaf']) > 0:
for cert in results['expired']['leaf']:
print("\t[] Certificate: %s expired on %s!" % (cert.get('Thumbprint'),cert.get('Valid Until')))
continue
else:
print("\tNone")
print("\n\tROOT CERTS:\n")
if len(results['expired']['root']) > 0:
for cert in results['expired']['root']:
print("\t[] Certificate: %s expired on %s!" % (cert.get('Thumbprint'),cert.get('Valid Until')))
continue
else:
print("\tNone")
if expired_count > 0:
print(warningmsg)
if __name__ == '__main__':
exit(main())
4.给checkstst.py执行权限
chmod +x checkstst.py
5.执行检测文件checksts.py显示证书情况
./checksts.py
6.从这个官方页面下载fixsts.sh,懒的话可以直接在/tmp下新建个fixsts.sh脚本文件,将下面的代码复制进去:https://kb.vmware.com/s/article/76719
#!/bin/bash
# Copyright (c) 2020-2021 VMware, Inc. All rights reserved.
# VMware Confidential
#
# Run this from the affected PSC/VC
#
# NOTE: This works on external and embedded PSCs
# This script will do the following
# 1: Regenerate STS certificate
#
# What is needed?
# 1: Offline snapshots of VCs/PSCs
# 2: SSO Admin Password
NODETYPE=$(cat /etc/vmware/deployment.node.type)
if [ "$NODETYPE" = "management" ]; then
echo "Detected this node is a vCenter server with external PSC."
echo "Please run this script from a vCenter with embedded PSC, or an external PSC"
exit 1
fi
if [ "$NODETYPE" = "embedded" ] && [ ! -f /usr/lib/vmware-vmdir/sbin/vmdird ]; then
echo "Detected this node is a vCenter gateway"
echo "Please run this script from a vCenter with embedded PSC, or an external PSC"
exit 1
fi
echo "NOTE: This works on external and embedded PSCs"
echo "This script will do the following"
echo "1: Regenerate STS certificate"
echo "What is needed?"
echo "1: Offline snapshots of VCs/PSCs"
echo "2: SSO Admin Password"
echo "IMPORTANT: This script should only be run on a single PSC per SSO domain"
mkdir -p /tmp/vmware-fixsts
SCRIPTPATH="/tmp/vmware-fixsts"
LOGFILE="$SCRIPTPATH/fix_sts_cert.log"
echo "==================================" | tee -a $LOGFILE
echo "Resetting STS certificate for $HOSTNAME started on $(date)" | tee -a $LOGFILE
echo ""| tee -a $LOGFILE
echo ""
DN=$(/opt/likewise/bin/lwregshell list_values '[HKEY_THIS_MACHINE\Services\vmdir]' | grep dcAccountDN | awk '{$1=$2=$3="";print $0}'|tr -d '"'|sed -e 's/^[ \t]*//')
echo "Detected DN: $DN" | tee -a $LOGFILE
PNID=$(/opt/likewise/bin/lwregshell list_values '[HKEY_THIS_MACHINE\Services\vmafd\Parameters]' | grep PNID | awk '{print $4}'|tr -d '"')
echo "Detected PNID: $PNID" | tee -a $LOGFILE
PSC=$(/opt/likewise/bin/lwregshell list_values '[HKEY_THIS_MACHINE\Services\vmafd\Parameters]' | grep DCName | awk '{print $4}'|tr -d '"')
echo "Detected PSC: $PSC" | tee -a $LOGFILE
DOMAIN=$(/opt/likewise/bin/lwregshell list_values '[HKEY_THIS_MACHINE\Services\vmafd\Parameters]' | grep DomainName | awk '{print $4}'|tr -d '"')
echo "Detected SSO domain name: $DOMAIN" | tee -a $LOGFILE
SITE=$(/opt/likewise/bin/lwregshell list_values '[HKEY_THIS_MACHINE\Services\vmafd\Parameters]' | grep SiteName | awk '{print $4}'|tr -d '"')
MACHINEID=$(/usr/lib/vmware-vmafd/bin/vmafd-cli get-machine-id --server-name localhost)
echo "Detected Machine ID: $MACHINEID" | tee -a $LOGFILE
IPADDRESS=$(ifconfig | grep eth0 -A1 | grep "inet addr" | awk -F ':' '{print $2}' | awk -F ' ' '{print $1}')
echo "Detected IP Address: $IPADDRESS" | tee -a $LOGFILE
DOMAINCN="dc=$(echo "$DOMAIN" | sed 's/\./,dc=/g')"
echo "Domain CN: $DOMAINCN"
ADMIN="cn=administrator,cn=users,$DOMAINCN"
USERNAME="administrator@${DOMAIN^^}"
ROOTCERTDATE=$(openssl x509 -in /var/lib/vmware/vmca/root.cer -text | grep "Not After" | awk -F ' ' '{print $7,$4,$5}')
TODAYSDATE=$(date +"%Y %b %d")
echo "#" > $SCRIPTPATH/certool.cfg
echo "# Template file for a CSR request" >> $SCRIPTPATH/certool.cfg
echo "#" >> certool.cfg
echo "# Country is needed and has to be 2 characters" >> $SCRIPTPATH/certool.cfg
echo "Country = DS" >> $SCRIPTPATH/certool.cfg
echo "Name = $PNID" >> $SCRIPTPATH/certool.cfg
echo "Organization = VMware" >> $SCRIPTPATH/certool.cfg
echo "OrgUnit = VMware" >> $SCRIPTPATH/certool.cfg
echo "State = VMware" >> $SCRIPTPATH/certool.cfg
echo "Locality = VMware" >> $SCRIPTPATH/certool.cfg
echo "IPAddress = $IPADDRESS" >> $SCRIPTPATH/certool.cfg
echo "Email = email@acme.com" >> $SCRIPTPATH/certool.cfg
echo "Hostname = $PNID" >> $SCRIPTPATH/certool.cfg
echo "==================================" | tee -a $LOGFILE
echo "==================================" | tee -a $LOGFILE
echo ""
echo "Detected Root's certificate expiration date: $ROOTCERTDATE" | tee -a $LOGFILE
echo "Detected today's date: $TODAYSDATE" | tee -a $LOGFILE
echo "==================================" | tee -a $LOGFILE
flag=0
if [[ $TODAYSDATE > $ROOTCERTDATE ]];
then
echo "IMPORTANT: Root certificate is expired, so it will be replaced" | tee -a $LOGFILE
flag=1
mkdir /certs && cd /certs
cp $SCRIPTPATH/certool.cfg /certs/vmca.cfg
/usr/lib/vmware-vmca/bin/certool --genselfcacert --outprivkey /certs/vmcacert.key --outcert /certs/vmcacert.crt --config /certs/vmca.cfg
/usr/lib/vmware-vmca/bin/certool --rootca --cert /certs/vmcacert.crt --privkey /certs/vmcacert.key
fi
echo "#" > $SCRIPTPATH/certool.cfg
echo "# Template file for a CSR request" >> $SCRIPTPATH/certool.cfg
echo "#" >> $SCRIPTPATH/certool.cfg
echo "# Country is needed and has to be 2 characters" >> $SCRIPTPATH/certool.cfg
echo "Country = DS" >> $SCRIPTPATH/certool.cfg
echo "Name = STS" >> $SCRIPTPATH/certool.cfg
echo "Organization = VMware" >> $SCRIPTPATH/certool.cfg
echo "OrgUnit = VMware" >> $SCRIPTPATH/certool.cfg
echo "State = VMware" >> $SCRIPTPATH/certool.cfg
echo "Locality = VMware" >> $SCRIPTPATH/certool.cfg
echo "IPAddress = $IPADDRESS" >> $SCRIPTPATH/certool.cfg
echo "Email = email@acme.com" >> $SCRIPTPATH/certool.cfg
echo "Hostname = $PNID" >> $SCRIPTPATH/certool.cfg
echo ""
echo "Exporting and generating STS certificate" | tee -a $LOGFILE
echo ""
cd $SCRIPTPATH
/usr/lib/vmware-vmca/bin/certool --server localhost --genkey --privkey=sts.key --pubkey=sts.pub
/usr/lib/vmware-vmca/bin/certool --gencert --cert=sts.cer --privkey=sts.key --config=$SCRIPTPATH/certool.cfg
openssl x509 -outform der -in sts.cer -out sts.der
CERTS=$(csplit -f root /var/lib/vmware/vmca/root.cer '/-----BEGIN CERTIFICATE-----/' '{*}' | wc -l)
openssl pkcs8 -topk8 -inform pem -outform der -in sts.key -out sts.key.der -nocrypt
i=1
until [ $i -eq $CERTS ]
do
openssl x509 -outform der -in root0$i -out vmca0$i.der
((i++))
done
echo ""
echo ""
read -s -p "Enter password for administrator@$DOMAIN: " DOMAINPASSWORD
echo ""
# Find the highest tenant credentials index
MAXCREDINDEX=1
while read -r line
do
INDEX=$(echo "$line" | tr -dc '0-9')
if [ $INDEX -gt $MAXCREDINDEX ]
then
MAXCREDINDEX=$INDEX
fi
done < <(/opt/likewise/bin/ldapsearch -h localhost -p 389 -b "cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" "(objectclass=vmwSTSTenantCredential)" cn | grep cn:)
# Sequentially search for tenant credentials up to max index and delete if found
echo "Highest tenant credentials index : $MAXCREDINDEX" | tee -a $LOGFILE
i=1
if [ ! -z $MAXCREDINDEX ]
then
until [ $i -gt $MAXCREDINDEX ]
do
echo "Exporting tenant $i to $SCRIPTPATH" | tee -a $LOGFILE
echo ""
ldapsearch -h localhost -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" -b "cn=TenantCredential-$i,cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" > $SCRIPTPATH/tenantcredential-$i.ldif
if [ $? -eq 0 ]
then
echo "Deleting tenant $i" | tee -a $LOGFILE
ldapdelete -h localhost -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" "cn=TenantCredential-$i,cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" | tee -a $LOGFILE
else
echo "Tenant $i not found" | tee -a $LOGFILE
echo ""
fi
((i++))
done
fi
echo ""
# Find the highest trusted cert chains index
MAXCERTCHAINSINDEX=1
while read -r line
do
INDEX=$(echo "$line" | tr -dc '0-9')
if [ $INDEX -gt $MAXCERTCHAINSINDEX ]
then
MAXCERTCHAINSINDEX=$INDEX
fi
done < <(/opt/likewise/bin/ldapsearch -h localhost -p 389 -b "cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" "(objectclass=vmwSTSTenantTrustedCertificateChain)" cn | grep cn:)
# Sequentially search for trusted cert chains up to max index and delete if found
echo "Highest trusted cert chains index: $MAXCERTCHAINSINDEX" | tee -a $LOGFILE
i=1
if [ ! -z $MAXCERTCHAINSINDEX ]
then
until [ $i -gt $MAXCERTCHAINSINDEX ]
do
echo "Exporting trustedcertchain $i to $SCRIPTPATH" | tee -a $LOGFILE
echo ""
ldapsearch -h localhost -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" -b "cn=TrustedCertChain-$i,cn=TrustedCertificateChains,cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" > $SCRIPTPATH/trustedcertchain-$i.ldif
if [ $? -eq 0 ]
then
echo "Deleting trustedcertchain $i" | tee -a $LOGFILE
ldapdelete -h localhost -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" "cn=TrustedCertChain-$i,cn=TrustedCertificateChains,cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" | tee -a $LOGFILE
else
echo "Trusted cert chain $i not found" | tee -a $LOGFILE
fi
echo ""
((i++))
done
fi
echo ""
i=1
echo "dn: cn=TenantCredential-1,cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" > sso-sts.ldif
echo "changetype: add" >> sso-sts.ldif
echo "objectClass: vmwSTSTenantCredential" >> sso-sts.ldif
echo "objectClass: top" >> sso-sts.ldif
echo "cn: TenantCredential-1" >> sso-sts.ldif
echo "userCertificate:< file:sts.der" >> sso-sts.ldif
until [ $i -eq $CERTS ]
do
echo "userCertificate:< file:vmca0$i.der" >> sso-sts.ldif
((i++))
done
echo "vmwSTSPrivateKey:< file:sts.key.der" >> sso-sts.ldif
echo "" >> sso-sts.ldif
echo "dn: cn=TrustedCertChain-1,cn=TrustedCertificateChains,cn=$DOMAIN,cn=Tenants,cn=IdentityManager,cn=Services,$DOMAINCN" >> sso-sts.ldif
echo "changetype: add" >> sso-sts.ldif
echo "objectClass: vmwSTSTenantTrustedCertificateChain" >> sso-sts.ldif
echo "objectClass: top" >> sso-sts.ldif
echo "cn: TrustedCertChain-1" >> sso-sts.ldif
echo "userCertificate:< file:sts.der" >> sso-sts.ldif
i=1
until [ $i -eq $CERTS ]
do
echo "userCertificate:< file:vmca0$i.der" >> sso-sts.ldif
((i++))
done
echo ""
echo "Applying newly generated STS certificate to SSO domain" | tee -a $LOGFILE
/opt/likewise/bin/ldapmodify -x -h localhost -p 389 -D "cn=administrator,cn=users,$DOMAINCN" -w "$DOMAINPASSWORD" -f sso-sts.ldif | tee -a $LOGFILE
echo ""
echo "Replacement finished - Please restart services on all vCenters and PSCs in your SSO domain" | tee -a $LOGFILE
echo "==================================" | tee -a $LOGFILE
echo "IMPORTANT: In case you're using HLM (Hybrid Linked Mode) without a gateway, you would need to re-sync the certs from Cloud to On-Prem after following this procedure" | tee -a $LOGFILE
echo "==================================" | tee -a $LOGFILE
echo "==================================" | tee -a $LOGFILE
if [ $flag == 1 ]
then
echo "Since your Root certificate was expired and was replaced, you will need to replace your MachineSSL and Solution User certificates" | tee -a $LOGFILE
echo "You can do so following this KB: https://kb.vmware.com/s/article/2097936" | tee -a $LOGFILE
fi
7.给fixsts.sh执行权限
chmod +x fixsts.sh
8.运行脚本./fixsts.sh,会提示你输入账户的密码
root@photon-machine [ /tmp ]# chmod +x fixsts.sh
root@photon-machine [ /tmp ]# ./fixsts.sh
NOTE: This works on external and embedded PSCs
This script will do the following
1: Regenerate STS certificate
What is needed?
1: Offline snapshots of VCs/PSCs
2: SSO Admin Password
IMPORTANT: This script should only be run on a single PSC per SSO domain
==================================
Resetting STS certificate for photon-machine started on Mon Jul 24 07:36:32 UTC 2023
Detected DN: cn=192.168.210.221,ou=Domain Controllers,dc=easy-speed,dc=net
Detected PNID: 192.168.210.221
Detected PSC: 192.168.210.221
Detected SSO domain name: easy-speed.net
Detected Machine ID: a4d1fd92-497b-4ee2-a7e6-93c215e80ce6
Detected IP Address: 192.168.210.221
Domain CN: dc=easy-speed,dc=net
==================================
==================================
Detected Root's certificate expiration date: 2031 Jul 18
Detected today's date: 2023 Jul 24
==================================
Exporting and generating STS certificate
Status : Success
Using config file : /tmp/vmware-fixsts/certool.cfg
Status : Success
Enter password for administrator@easy-speed.net:
Highest tenant credentials index : 1
Exporting tenant 1 to /tmp/vmware-fixsts
Deleting tenant 1
Highest trusted cert chains index: 1
Exporting trustedcertchain 1 to /tmp/vmware-fixsts
Deleting trustedcertchain 1
Applying newly generated STS certificate to SSO domain
adding new entry "cn=TenantCredential-1,cn=easy-speed.net,cn=Tenants,cn=IdentityManager,cn=Services,dc=easy-speed,dc=net"
adding new entry "cn=TrustedCertChain-1,cn=TrustedCertificateChains,cn=easy-speed.net,cn=Tenants,cn=IdentityManager,cn=Services,dc=easy-speed,dc=net"
Replacement finished - Please restart services on all vCenters and PSCs in your SSO domain
==================================
IMPORTANT: In case you're using HLM (Hybrid Linked Mode) without a gateway, you would need to re-sync the certs from Cloud to On-Prem after following this procedure
==================================
==================================
root@photon-machine [ /tmp ]#
9.重启服务
service-control --stop --all && service-control --start --all
会发现有几个服务无法启动,导致web界面报错503,不能正常访问
没有启动起来的服务直接无视,因为证书还没替换
重新分配证书
执行以下命令替换证书配置
/usr/lib/vmware-vmca/bin/certificate-manager
输入“8”按提示填入,可回车直接跳过按默认值设置
root@photon-machine [ ~ ]# /usr/lib/vmware-vmca/bin/certificate-manager
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
| |
| *** Welcome to the vSphere 6.7 Certificate Manager *** |
| |
| -- Select Operation -- |
| |
| 1. Replace Machine SSL certificate with Custom Certificate |
| |
| 2. Replace VMCA Root certificate with Custom Signing |
| Certificate and replace all Certificates |
| |
| 3. Replace Machine SSL certificate with VMCA Certificate |
| |
| 4. Regenerate a new VMCA Root Certificate and |
| replace all certificates |
| |
| 5. Replace Solution user certificates with |
| Custom Certificate |
| |
| 6. Replace Solution user certificates with VMCA certificates |
| |
| 7. Revert last performed operation by re-publishing old |
| certificates |
| |
| 8. Reset all Certificates |
|_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _|
Note : Use Ctrl-D to exit.
Option[1 to 8]: 8
Do you wish to generate all certificates using configuration file : Option[Y/N] ? : Y
Please provide valid SSO and VC privileged user credential to perform certificate operations.
Enter username [Administrator@vsphere.local]:administrator@easy-speed.net
Enter password:
Please configure certool.cfg with proper values before proceeding to next step.
Press Enter key to skip optional parameters or use Default value.
Enter proper value for 'Country' [Default value : US] :
Enter proper value for 'Name' [Default value : CA] :
Enter proper value for 'Organization' [Default value : VMware] :
Enter proper value for 'OrgUnit' [Default value : VMware Engineering] :
Enter proper value for 'State' [Default value : California] :
Enter proper value for 'Locality' [Default value : Palo Alto] :
Enter proper value for 'IPAddress' (Provide comma separated values for multiple IP addresses) [optional] : 192.168.210.221
Enter proper value for 'Email' [Default value : email@acme.com] :
Enter proper value for 'Hostname' (Provide comma separated values for multiple Hostname entries) [Enter valid Fully Qualified Domain Name(FQDN), For Example : example.domain.com] : 192.168.210.221
Enter proper value for VMCA 'Name' :192.168.210.221
Continue operation : Option[Y/N] ? : Y
You are going to reset by regenerating Root Certificate and replace all certificates using VMCA
Continue operation : Option[Y/N] ? : Y
Get site nameCompleted [Reset Machine SSL Cert...]
default-site
Lookup all services
Get service default-site:557656a5-0379-42d2-9b3a-b778ae353b65
Update service default-site:557656a5-0379-42d2-9b3a-b778ae353b65; spec: /tmp/svcspec_4cnfxa7v
Get service default-site:21b0edf5-3202-4423-9f8f-0d77d4f7dd8b
Update service default-site:21b0edf5-3202-4423-9f8f-0d77d4f7dd8b; spec: /tmp/svcspec_61cuyj1d
Get service default-site:144df4ab-30bc-4b6e-ba81-53b54df7012a
Update service default-site:144df4ab-30bc-4b6e-ba81-53b54df7012a; spec: /tmp/svcspec_zvkdu0xv
Get service 3299a9ad-d930-404e-a424-6aab1037bc2d
Update service 3299a9ad-d930-404e-a424-6aab1037bc2d; spec: /tmp/svcspec_08a59hjc
Get service 02ee5039-1108-41b8-9b05-8ad9874effec
Update service 02ee5039-1108-41b8-9b05-8ad9874effec; spec: /tmp/svcspec_ae_5nli4
Get service e4a92e69-c94f-4b28-a22f-2616e01ebebd
Update service e4a92e69-c94f-4b28-a22f-2616e01ebebd; spec: /tmp/svcspec_uskymho0
Get service 1935cb5b-b659-4f06-996e-afe52ddf4c32
Update service 1935cb5b-b659-4f06-996e-afe52ddf4c32; spec: /tmp/svcspec_u89o8z42
Get service a50c3030-ade4-4098-a3be-ecffc298e4ba
Update service a50c3030-ade4-4098-a3be-ecffc298e4ba; spec: /tmp/svcspec_yvmts1rq
Get service 4d876793-b99f-4fdb-b569-2262c0ff4f79
Update service 4d876793-b99f-4fdb-b569-2262c0ff4f79; spec: /tmp/svcspec_4sto08zq
Get service ab793d77-ab2e-40c9-a0a4-cefd20f5e4f1
Update service ab793d77-ab2e-40c9-a0a4-cefd20f5e4f1; spec: /tmp/svcspec_g04z603j
Get service 4ec2ce2e-8252-4058-9ceb-535b7c61bc12
Update service 4ec2ce2e-8252-4058-9ceb-535b7c61bc12; spec: /tmp/svcspec_4bt34fjo
Get service e4a92e69-c94f-4b28-a22f-2616e01ebebd_kv
Update service e4a92e69-c94f-4b28-a22f-2616e01ebebd_kv; spec: /tmp/svcspec_aaemzckl
Get service 5f1460a8-b7ec-4f06-9307-7c11438db661
Update service 5f1460a8-b7ec-4f06-9307-7c11438db661; spec: /tmp/svcspec_6klo0e_r
Get service e4a92e69-c94f-4b28-a22f-2616e01ebebd_authz
Update service e4a92e69-c94f-4b28-a22f-2616e01ebebd_authz; spec: /tmp/svcspec_wwhv0w42
Get service 118e7636-9292-4c27-9a31-d12659db81c5
Update service 118e7636-9292-4c27-9a31-d12659db81c5; spec: /tmp/svcspec_sy_lktv8
Get service 0b848923-3990-48c5-ad17-903f52b091c8
Update service 0b848923-3990-48c5-ad17-903f52b091c8; spec: /tmp/svcspec__wfw4xht
Get service 156b9746-05fa-4457-81d1-dea20f915400_com.vmware.vsphere.client
Don't update service 156b9746-05fa-4457-81d1-dea20f915400_com.vmware.vsphere.client
Get service 60dd1be9-72ec-4f4d-8064-116136f2211a
Update service 60dd1be9-72ec-4f4d-8064-116136f2211a; spec: /tmp/svcspec_42kz3zk7
Get service 0d885ea6-eb55-453f-bdb9-fa1a360d0649
Update service 0d885ea6-eb55-453f-bdb9-fa1a360d0649; spec: /tmp/svcspec_5_c6g6vd
Get service 69441fe6-e425-49d3-a791-7fb528f8d052
Update service 69441fe6-e425-49d3-a791-7fb528f8d052; spec: /tmp/svcspec_zdy75xjf
Get service 0afb77db-bcc8-487a-9843-d905fe3736ec
Update service 0afb77db-bcc8-487a-9843-d905fe3736ec; spec: /tmp/svcspec_gb1o9ebe
Get service 3038f67f-6ed1-4c41-9825-a4bd7f4d30c0
Update service 3038f67f-6ed1-4c41-9825-a4bd7f4d30c0; spec: /tmp/svcspec_ro0hmpnd
Get service 156b9746-05fa-4457-81d1-dea20f915400
Update service 156b9746-05fa-4457-81d1-dea20f915400; spec: /tmp/svcspec_ibl0k8gz
Get service 91040752-705e-455d-b7f7-8a2a5b55198f
Update service 91040752-705e-455d-b7f7-8a2a5b55198f; spec: /tmp/svcspec_i_cb11bn
Get service b7cc1d16-dea8-4133-bb41-c5aff1f51878
Update service b7cc1d16-dea8-4133-bb41-c5aff1f51878; spec: /tmp/svcspec_9sclpoxe
Get service 0b58d64e-5e65-4aaa-b9e4-51eec1f4d859
Update service 0b58d64e-5e65-4aaa-b9e4-51eec1f4d859; spec: /tmp/svcspec_v_egt44s
Get service d71cd23e-18f1-4148-844b-194d5247cfd9
Update service d71cd23e-18f1-4148-844b-194d5247cfd9; spec: /tmp/svcspec_dhbem4d2
Get service de1bad12-40c0-44c7-8988-9ba0816e0f40
Update service de1bad12-40c0-44c7-8988-9ba0816e0f40; spec: /tmp/svcspec_5q9wcetx
Get service fc55c1fe-d7a7-472f-8d94-d40b8ecd32f9
Update service fc55c1fe-d7a7-472f-8d94-d40b8ecd32f9; spec: /tmp/svcspec_d0oey4sj
Get service 804093e3-2303-4d4f-8295-ec915a28a106
Update service 804093e3-2303-4d4f-8295-ec915a28a106; spec: /tmp/svcspec_4lykbwn7
Get service fecde711-151d-473b-a69f-dd2b62bddabe
Update service fecde711-151d-473b-a69f-dd2b62bddabe; spec: /tmp/svcspec_5o8i4djz
Get service 8670ec91-5f8a-406d-b6b5-ad157ee31e20
Update service 8670ec91-5f8a-406d-b6b5-ad157ee31e20; spec: /tmp/svcspec_eo4polw3
Get service b816b1d3-6ae8-45ac-9429-bfac4399ecf2
Update service b816b1d3-6ae8-45ac-9429-bfac4399ecf2; spec: /tmp/svcspec_m7zk30de
Get service 778f10b9-c79d-4ac0-823c-5536a9fd9d64
Update service 778f10b9-c79d-4ac0-823c-5536a9fd9d64; spec: /tmp/svcspec_5b838h59
Get service 20601d5d-ac8b-4153-9828-d7a250a251c6
Update service 20601d5d-ac8b-4153-9828-d7a250a251c6; spec: /tmp/svcspec_d8ca0t6q
Updated 34 service(s)
Status : 60% Completed [Reset vpxd-extension Cert...]
2023-07-24T09:49:39.358Z Updating certificate for "com.vmware.vim.eam" extension
2023-07-24T09:49:39.708Z Updating certificate for "com.vmware.rbd" extension
2023-07-24T09:49:40.046Z Updating certificate for "com.vmware.imagebuilder" extension
Reset status : 85% Completed [starting services...]
Reset status : 100% Completed [Reset completed successfully]
问题解决
现在访问VC,正常登录
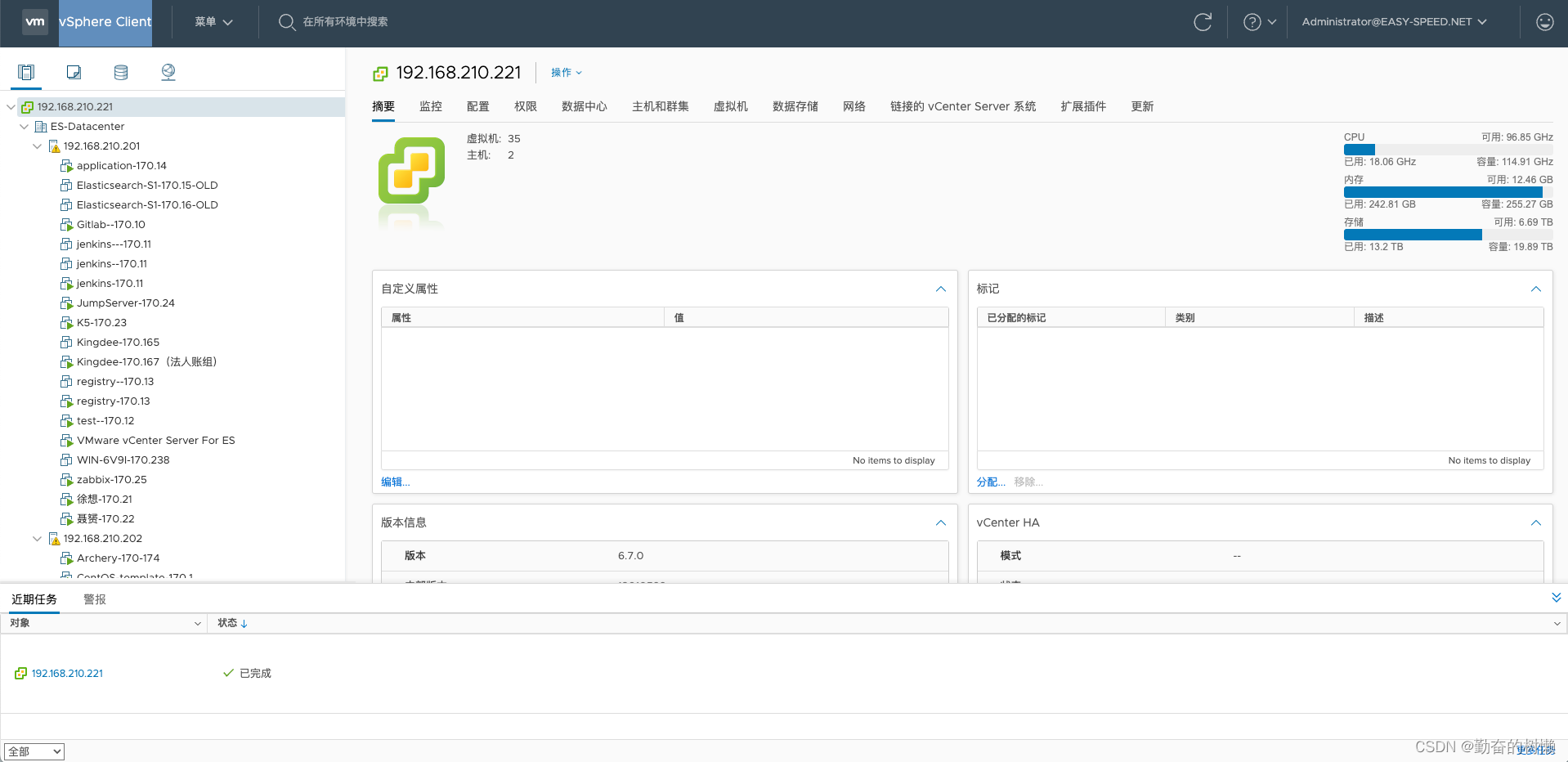
再来查看证书有效期又加了2年