SSH远程登录RaspberryPi命令行响应缓慢问题
- 1. 问题
- 2. 分析
- 3. 解决
- 3.1 去掉PAM部分鉴权模块
- 3.2 去掉sshd的DNS设置
- 3.3 无线WiFi信号优化
-
- 4. 结果
- 4.1 测试结果一
- 4.2 测试结果二
- 4.3 RootCause
- 5. 补充资料
- 5.1 [排除wifi网卡功率自管理问题](https://raspberrypi.stackexchange.com/questions/96606/make-iw-wlan0-set-power-save-off-permanent)
- 5.2 hostname已经修改(不存在重复)
- 6. 参考资料
1. 问题
远程登录Raspberry Zero WH命令行,操作响应缓慢,应该说极其缓慢,简直无法仍受。
注:刚开始烧录映像文件的时候,倒是没有类似的问题。
2. 分析
通过SSH日志文件分析响应缓慢问题,修改配置参数“LogLevel”将其设置为最大级别DEBUG3,这样我们就可以通过SSH服务日志文件“/var/log/auth.log”日志的详细信息了解缓慢问题出在哪里。
$ sudo nano /etc/ssh/sshd_config
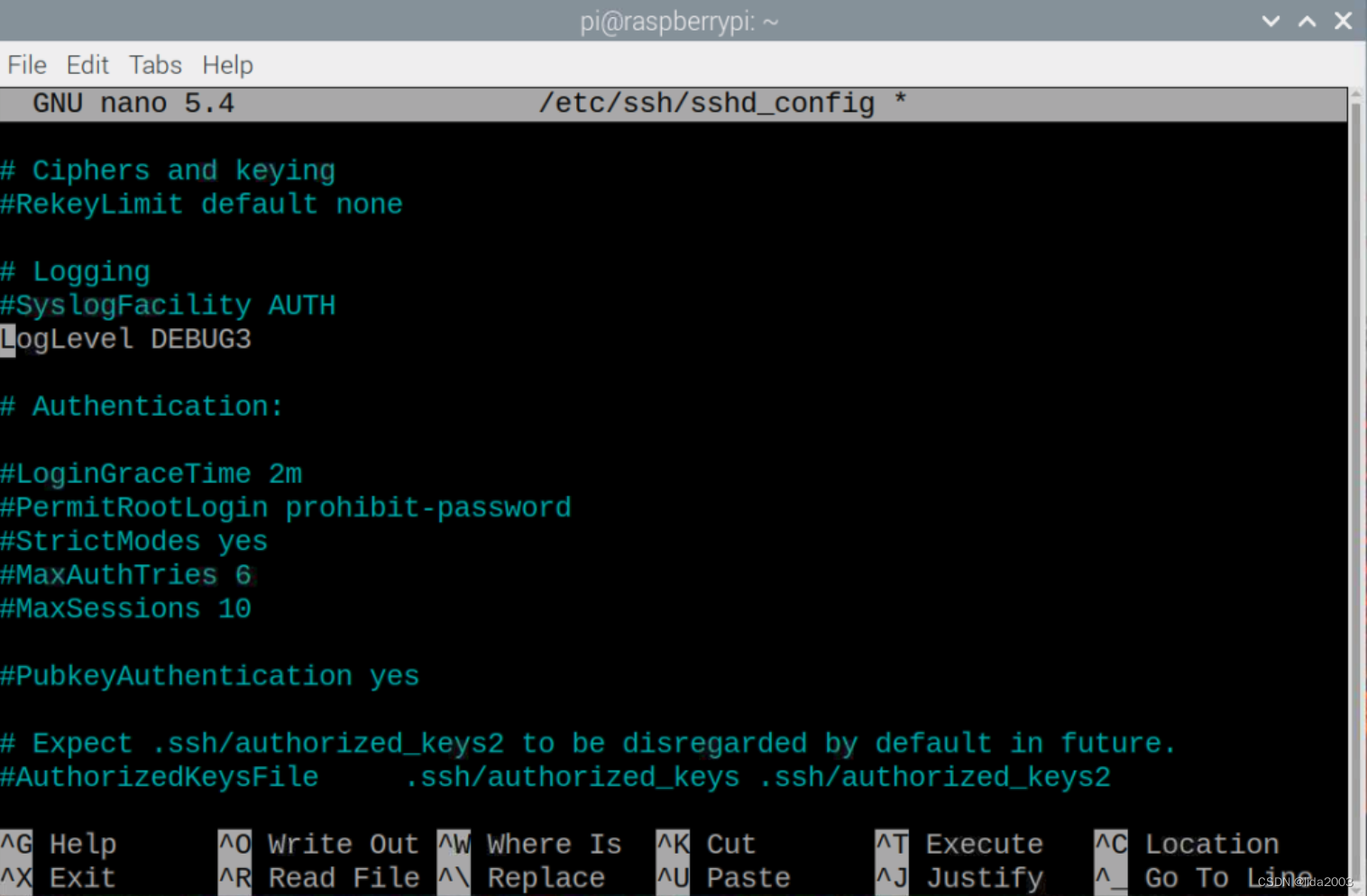
3. 解决
3.1 去掉PAM部分鉴权模块
$ sudo nano /etc/pam.d/common-session
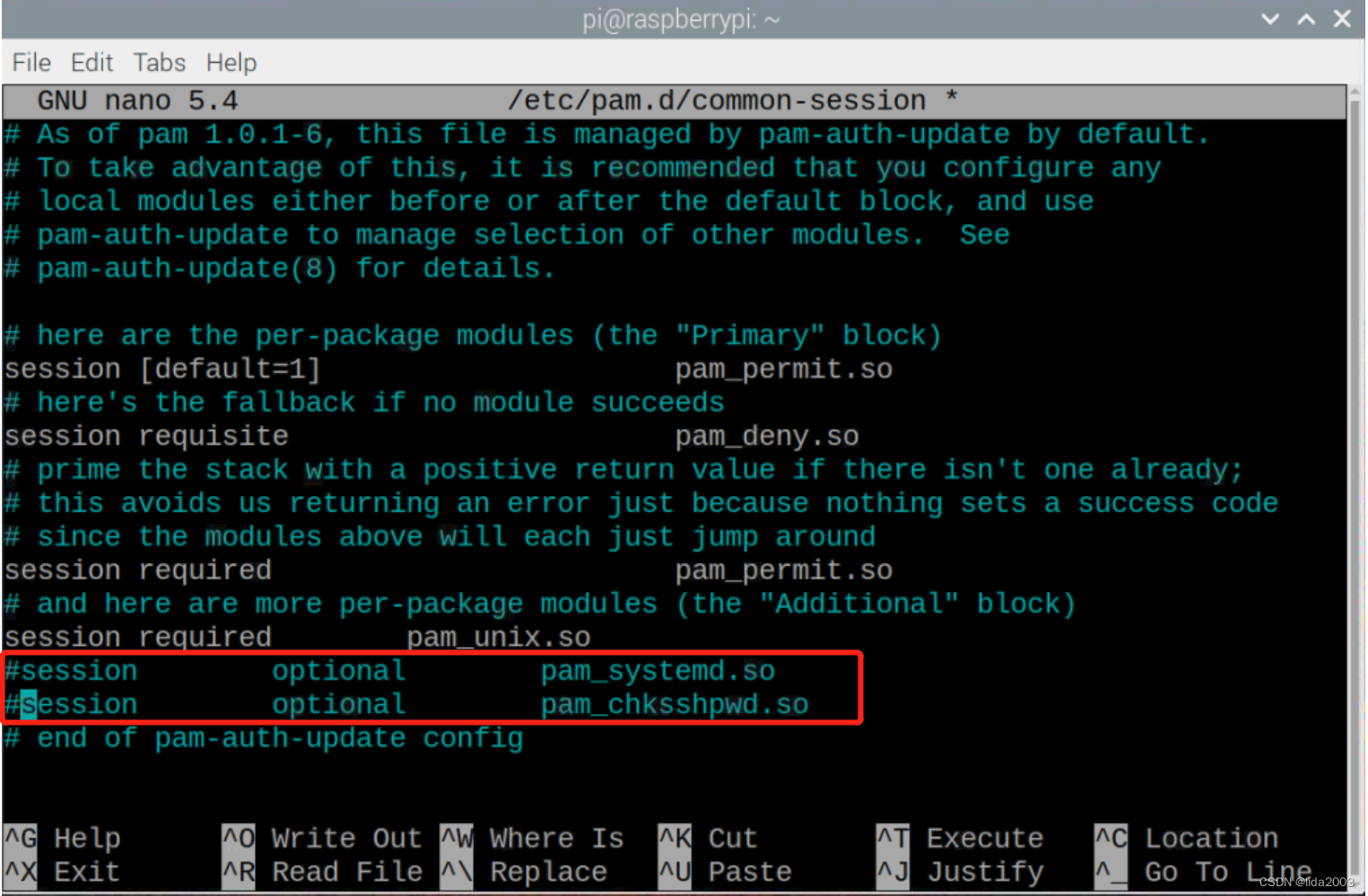
3.2 去掉sshd的DNS设置
$ sudo nano /etc/ssh/sshd_config
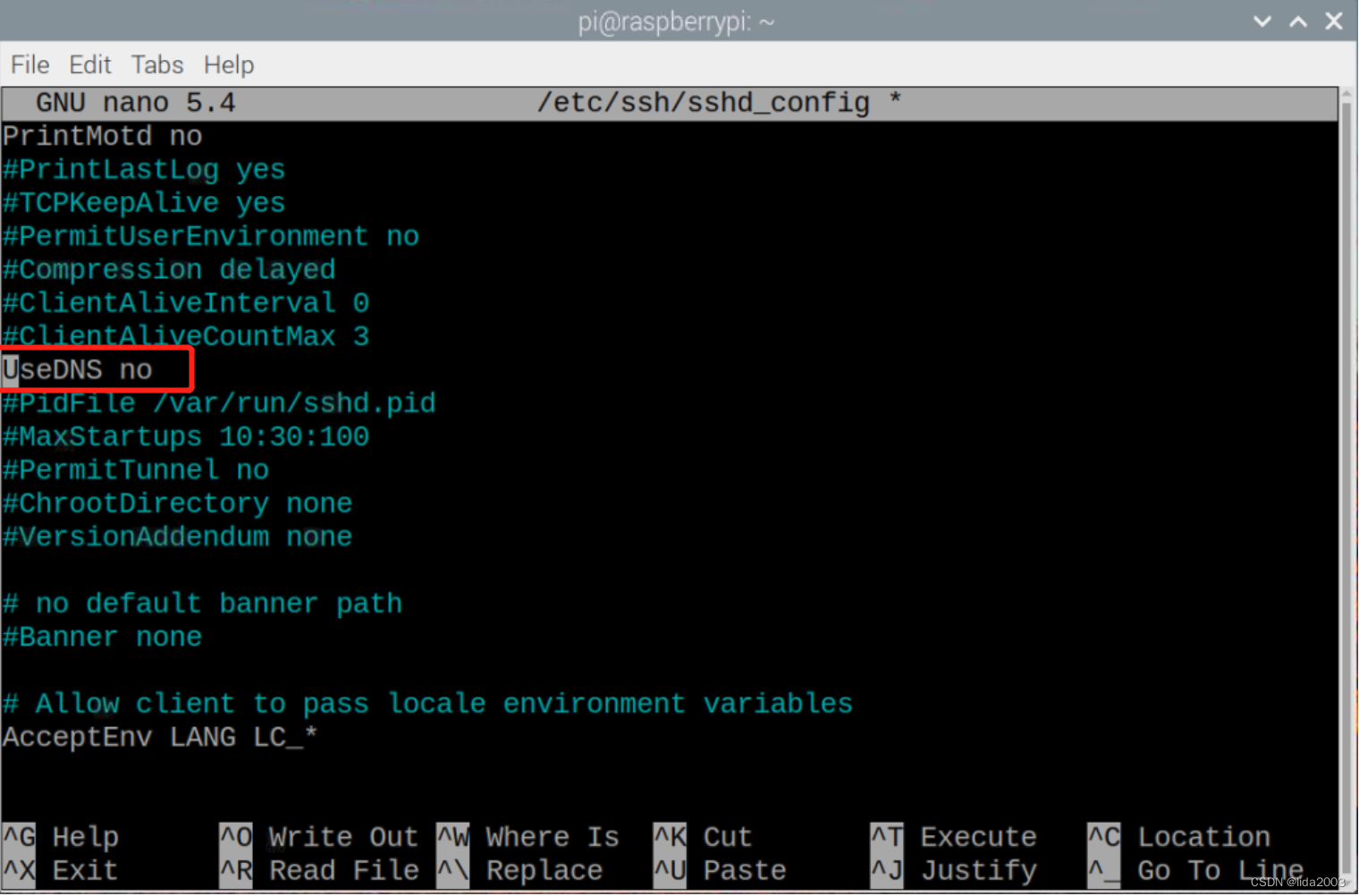
3.3 无线WiFi信号优化
鉴于Raspberry Zero WH板子上天线也是非常紧凑的,且2.4G也可能存在遮挡导致信号相对较差,如果能将报文长度减小,受干扰的机会就会减少。

这里确实找到网络上的一个方法,减少MTU的大小。
方法一:ifconfig操作
$ sudo ifconfig wlan0
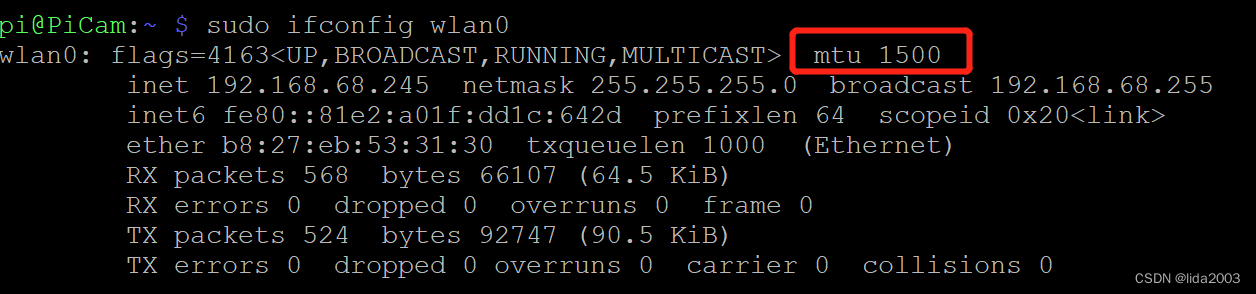
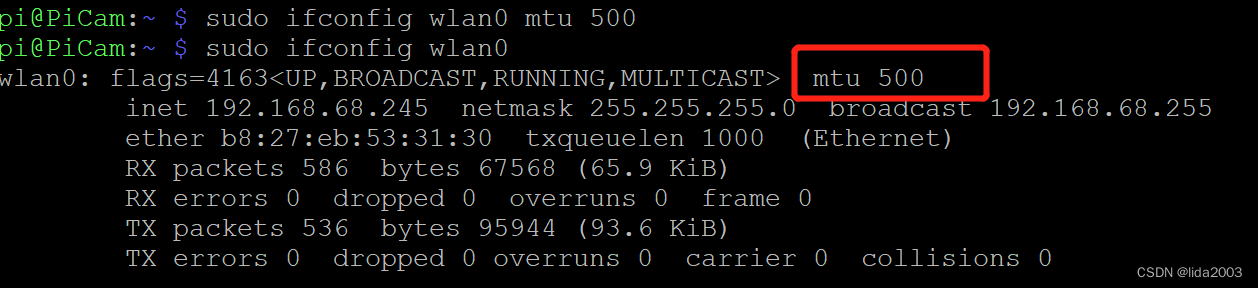
$ sudo ifconfig wlan0 mtu 500
$ sudo ifconfig wlan0
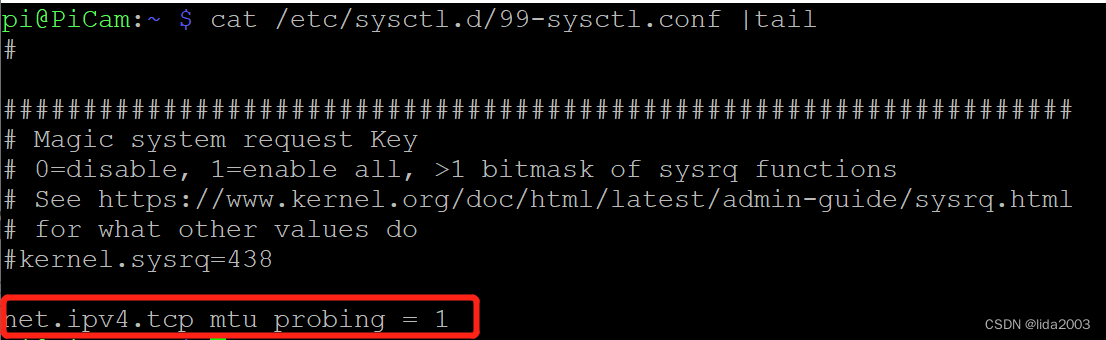
方法二:内核自动检测
比较优雅的操作方法是在/etc/sysctl.d/99-sysctl.conf加上net.ipv4.tcp_mtu_probing = 1:
$ sudo vi /etc/sysctl.d/99-sysctl.conf
$ sudo sysctl --system
4. 结果
4.1 测试结果一
感觉确实不会超级响应缓慢,但是还是有点磕磕碰碰的感觉。
- 树莓派直接放在路由器边上(可是距离)
- 内核自动调参,实际MTU1500没有什么变化(排除无线通信干扰)
- 整体感觉确实比之前无法忍受的情况有所改善,但是还是有点磕磕碰碰。
应该还有问题,但是不知道具体是什么,存疑!
- 14:16:20 - 14:17:06 完成登录,耗时46秒(含用户密码输入)
- 14:16:28 - 3 14:16:47 环境变量复制,耗时19秒(太长了)
- 14:16:47 - 14:17:01 一段空隙时间,长度14秒(不太清楚具体工作)
- 14:17:01 - 14:17:06 pam_unix鉴权耗时5秒
- 其他不概述耗时:46 - 19 -14 - 5 = 8秒
注:有知道的兄弟朋友,请批注指点下,谢谢!
$ cat /var/log/auth.log
Feb 3 14:16:20 PiCam sshd[410]: debug3: fd 5 is not O_NONBLOCK
Feb 3 14:16:20 PiCam sshd[410]: debug1: Forked child 783.
Feb 3 14:16:20 PiCam sshd[410]: debug3: send_rexec_state: entering fd = 8 config len 306
Feb 3 14:16:20 PiCam sshd[410]: debug3: ssh_msg_send: type 0
Feb 3 14:16:20 PiCam sshd[410]: debug3: send_rexec_state: done
Feb 3 14:16:20 PiCam sshd[783]: debug3: oom_adjust_restore
Feb 3 14:16:20 PiCam sshd[783]: debug1: Set /proc/self/oom_score_adj to 0
Feb 3 14:16:20 PiCam sshd[783]: debug1: rexec start in 5 out 5 newsock 5 pipe 7 sock 8
Feb 3 14:16:21 PiCam sshd[783]: debug1: inetd sockets after dupping: 3, 3
Feb 3 14:16:21 PiCam sshd[783]: Connection from 192.168.68.52 port 65369 on 192.168.68.245 port 22
Feb 3 14:16:21 PiCam sshd[783]: debug1: Client protocol version 2.0; client software version PuTTY_Release_0.78
Feb 3 14:16:21 PiCam sshd[783]: debug1: no match: PuTTY_Release_0.78
Feb 3 14:16:21 PiCam sshd[783]: debug1: Local version string SSH-2.0-OpenSSH_7.9p1 Raspbian-10+deb10u2+rpt1
Feb 3 14:16:21 PiCam sshd[783]: debug2: fd 3 setting O_NONBLOCK
Feb 3 14:16:21 PiCam sshd[783]: debug3: ssh_sandbox_init: preparing seccomp filter sandbox
Feb 3 14:16:21 PiCam sshd[783]: debug2: Network child is on pid 784
Feb 3 14:16:21 PiCam sshd[783]: debug3: preauth child monitor started
Feb 3 14:16:21 PiCam sshd[783]: debug3: privsep user:group 107:65534 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: permanently_set_uid: 107/65534 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: ssh_sandbox_child: setting PR_SET_NO_NEW_PRIVS [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: ssh_sandbox_child: attaching seccomp filter program [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: list_hostkey_types: rsa-sha2-512,rsa-sha2-256,ssh-rsa,ecdsa-sha2-nistp256,ssh-ed25519 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: send packet: type 20 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: SSH2_MSG_KEXINIT sent [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: receive packet: type 20 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: SSH2_MSG_KEXINIT received [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: local server KEXINIT proposal [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: host key algorithms: rsa-sha2-512,rsa-sha2-256,ssh-rsa,ecdsa-sha2-nistp256,ssh-ed25519 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: compression ctos: none,zlib@openssh.com [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: compression stoc: none,zlib@openssh.com [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: languages ctos: [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: languages stoc: [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: first_kex_follows 0 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: reserved 0 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: peer client KEXINIT proposal [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: KEX algorithms: sntrup761x25519-sha512@openssh.com,curve448-sha512,curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group-exchange-sha1,diffie-hellman-group18-sha512,diffie-hellman-group17-sha512,diffie-hellman-group16-sha512,diffie-hellman-group15-sha512,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,rsa2048-sha256,rsa1024-sha1,diffie-hellman-group1-sha1,ext-info-c [prea
Feb 3 14:16:21 PiCam sshd[783]: debug2: host key algorithms: ssh-ed25519,ssh-ed448,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,rsa-sha2-512,rsa-sha2-256,ssh-rsa,ssh-dss [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: ciphers ctos: aes256-ctr,aes256-cbc,rijndael-cbc@lysator.liu.se,aes192-ctr,aes192-cbc,aes128-ctr,aes128-cbc,chacha20-poly1305@openssh.com,aes128-gcm@openssh.com,aes256-gcm@openssh.com,3des-ctr,3des-cbc,blowfish-ctr,blowfish-cbc,arcfour256,arcfour128 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: ciphers stoc: aes256-ctr,aes256-cbc,rijndael-cbc@lysator.liu.se,aes192-ctr,aes192-cbc,aes128-ctr,aes128-cbc,chacha20-poly1305@openssh.com,aes128-gcm@openssh.com,aes256-gcm@openssh.com,3des-ctr,3des-cbc,blowfish-ctr,blowfish-cbc,arcfour256,arcfour128 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: MACs ctos: hmac-sha2-256,hmac-sha1,hmac-sha1-96,hmac-md5,hmac-sha2-256-etm@openssh.com,hmac-sha1-etm@openssh.com,hmac-sha1-96-etm@openssh.com,hmac-md5-etm@openssh.com [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: MACs stoc: hmac-sha2-256,hmac-sha1,hmac-sha1-96,hmac-md5,hmac-sha2-256-etm@openssh.com,hmac-sha1-etm@openssh.com,hmac-sha1-96-etm@openssh.com,hmac-md5-etm@openssh.com [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: compression ctos: none,zlib,zlib@openssh.com [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: compression stoc: none,zlib,zlib@openssh.com [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: languages ctos: [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: languages stoc: [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: first_kex_follows 0 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: reserved 0 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: kex: algorithm: curve25519-sha256 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: kex: host key algorithm: ssh-ed25519 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: kex: client->server cipher: aes256-ctr MAC: hmac-sha2-256 compression: none [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: kex: server->client cipher: aes256-ctr MAC: hmac-sha2-256 compression: none [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: expecting SSH2_MSG_KEX_ECDH_INIT [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: receive packet: type 30 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: mm_sshkey_sign entering [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: mm_request_send entering: type 6 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: mm_request_receive entering
Feb 3 14:16:21 PiCam sshd[783]: debug3: monitor_read: checking request 6
Feb 3 14:16:21 PiCam sshd[783]: debug3: mm_answer_sign
Feb 3 14:16:21 PiCam sshd[783]: debug3: mm_answer_sign: hostkey proof signature 0x14cec20(83)
Feb 3 14:16:21 PiCam sshd[783]: debug3: mm_request_send entering: type 7
Feb 3 14:16:21 PiCam sshd[783]: debug2: monitor_read: 6 used once, disabling now
Feb 3 14:16:21 PiCam sshd[783]: debug3: mm_sshkey_sign: waiting for MONITOR_ANS_SIGN [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: mm_request_receive_expect entering: type 7 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: mm_request_receive entering [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: send packet: type 31 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: send packet: type 21 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: set_newkeys: mode 1 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: rekey after 4294967296 blocks [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: SSH2_MSG_NEWKEYS sent [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: expecting SSH2_MSG_NEWKEYS [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: send packet: type 7 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: receive packet: type 21 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: SSH2_MSG_NEWKEYS received [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug2: set_newkeys: mode 0 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: rekey after 4294967296 blocks [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug1: KEX done [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: receive packet: type 5 [preauth]
Feb 3 14:16:21 PiCam sshd[783]: debug3: send packet: type 6 [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: receive packet: type 50 [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug1: userauth-request for user pi service ssh-connection method none [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug1: attempt 0 failures 0 [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_getpwnamallow entering [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_request_send entering: type 8 [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_getpwnamallow: waiting for MONITOR_ANS_PWNAM [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_request_receive_expect entering: type 9 [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_request_receive entering [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_request_receive entering
Feb 3 14:16:24 PiCam sshd[783]: debug3: monitor_read: checking request 8
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_answer_pwnamallow
Feb 3 14:16:24 PiCam sshd[783]: debug2: parse_server_config: config reprocess config len 306
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_answer_pwnamallow: sending MONITOR_ANS_PWNAM: 1
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_request_send entering: type 9
Feb 3 14:16:24 PiCam sshd[783]: debug2: monitor_read: 8 used once, disabling now
Feb 3 14:16:24 PiCam sshd[783]: debug2: input_userauth_request: setting up authctxt for pi [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_start_pam entering [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_request_send entering: type 100 [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_inform_authserv entering [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_request_send entering: type 4 [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug2: input_userauth_request: try method none [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: user_specific_delay: user specific delay 0.000ms [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: ensure_minimum_time_since: elapsed 35.713ms, delaying 32.016ms (requested 8.466ms) [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_request_receive entering
Feb 3 14:16:24 PiCam sshd[783]: debug3: monitor_read: checking request 100
Feb 3 14:16:24 PiCam sshd[783]: debug1: PAM: initializing for "pi"
Feb 3 14:16:24 PiCam sshd[783]: debug1: PAM: setting PAM_RHOST to "192.168.68.52"
Feb 3 14:16:24 PiCam sshd[783]: debug1: PAM: setting PAM_TTY to "ssh"
Feb 3 14:16:24 PiCam sshd[783]: debug2: monitor_read: 100 used once, disabling now
Feb 3 14:16:24 PiCam sshd[783]: debug3: userauth_finish: failure partial=0 next methods="publickey,password" [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: send packet: type 51 [preauth]
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_request_receive entering
Feb 3 14:16:24 PiCam sshd[783]: debug3: monitor_read: checking request 4
Feb 3 14:16:24 PiCam sshd[783]: debug3: mm_answer_authserv: service=ssh-connection, style=, role=
Feb 3 14:16:24 PiCam sshd[783]: debug2: monitor_read: 4 used once, disabling now
Feb 3 14:16:26 PiCam sshd[783]: debug3: receive packet: type 2 [preauth]
Feb 3 14:16:26 PiCam sshd[783]: debug3: Received SSH2_MSG_IGNORE [preauth]
Feb 3 14:16:26 PiCam sshd[783]: debug3: receive packet: type 50 [preauth]
Feb 3 14:16:26 PiCam sshd[783]: debug1: userauth-request for user pi service ssh-connection method password [preauth]
Feb 3 14:16:26 PiCam sshd[783]: debug1: attempt 1 failures 0 [preauth]
Feb 3 14:16:26 PiCam sshd[783]: debug2: input_userauth_request: try method password [preauth]
Feb 3 14:16:26 PiCam sshd[783]: debug3: mm_auth_password entering [preauth]
Feb 3 14:16:26 PiCam sshd[783]: debug3: mm_request_send entering: type 12 [preauth]
Feb 3 14:16:26 PiCam sshd[783]: debug3: mm_auth_password: waiting for MONITOR_ANS_AUTHPASSWORD [preauth]
Feb 3 14:16:26 PiCam sshd[783]: debug3: mm_request_receive_expect entering: type 13 [preauth]
Feb 3 14:16:26 PiCam sshd[783]: debug3: mm_request_receive entering [preauth]
Feb 3 14:16:26 PiCam sshd[783]: debug3: mm_request_receive entering
Feb 3 14:16:26 PiCam sshd[783]: debug3: monitor_read: checking request 12
Feb 3 14:16:26 PiCam sshd[783]: debug3: PAM: sshpam_passwd_conv called with 1 messages
Feb 3 14:16:27 PiCam sshd[783]: debug1: PAM: password authentication accepted for pi
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_answer_authpassword: sending result 1
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_request_send entering: type 13
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_request_receive_expect entering: type 102
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_request_receive entering
Feb 3 14:16:27 PiCam sshd[783]: debug1: do_pam_account: called
Feb 3 14:16:27 PiCam sshd[783]: debug2: do_pam_account: auth information in SSH_AUTH_INFO_0
Feb 3 14:16:27 PiCam sshd[783]: debug3: PAM: do_pam_account pam_acct_mgmt = 0 (Success)
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_request_send entering: type 103
Feb 3 14:16:27 PiCam sshd[783]: Accepted password for pi from 192.168.68.52 port 65369 ssh2
Feb 3 14:16:27 PiCam sshd[783]: debug1: monitor_child_preauth: pi has been authenticated by privileged process
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_get_keystate: Waiting for new keys
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_request_receive_expect entering: type 26
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_request_receive entering
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_get_keystate: GOT new keys
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_auth_password: user authenticated [preauth]
Feb 3 14:16:27 PiCam sshd[783]: debug3: user_specific_delay: user specific delay 0.000ms [preauth]
Feb 3 14:16:27 PiCam sshd[783]: debug3: ensure_minimum_time_since: elapsed 348.066ms, delaying 193.765ms (requested 8.466ms) [preauth]
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_do_pam_account entering [preauth]
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_request_send entering: type 102 [preauth]
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_request_receive_expect entering: type 103 [preauth]
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_request_receive entering [preauth]
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_do_pam_account returning 1 [preauth]
Feb 3 14:16:27 PiCam sshd[783]: debug3: send packet: type 52 [preauth]
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_request_send entering: type 26 [preauth]
Feb 3 14:16:27 PiCam sshd[783]: debug3: mm_send_keystate: Finished sending state [preauth]
Feb 3 14:16:27 PiCam sshd[783]: debug1: monitor_read_log: child log fd closed
Feb 3 14:16:27 PiCam sshd[783]: debug3: ssh_sandbox_parent_finish: finished
Feb 3 14:16:27 PiCam sshd[783]: debug1: PAM: establishing credentials
Feb 3 14:16:27 PiCam sshd[783]: debug3: PAM: opening session
Feb 3 14:16:27 PiCam sshd[783]: debug2: do_pam_session: auth information in SSH_AUTH_INFO_0
Feb 3 14:16:27 PiCam sshd[783]: pam_unix(sshd:session): session opened for user pi by (uid=0)
Feb 3 14:16:27 PiCam sshd[783]: debug3: PAM: sshpam_store_conv called with 1 messages
Feb 3 14:16:27 PiCam sshd[783]: debug3: PAM: sshpam_store_conv called with 1 messages
Feb 3 14:16:27 PiCam sshd[783]: User child is on pid 804
Feb 3 14:16:27 PiCam sshd[804]: debug1: SELinux support disabled
Feb 3 14:16:27 PiCam sshd[804]: debug1: PAM: establishing credentials
Feb 3 14:16:27 PiCam sshd[804]: debug1: permanently_set_uid: 1000/1000
Feb 3 14:16:27 PiCam sshd[804]: debug3: monitor_apply_keystate: packet_set_state
Feb 3 14:16:27 PiCam sshd[804]: debug2: set_newkeys: mode 0
Feb 3 14:16:27 PiCam sshd[804]: debug1: rekey after 4294967296 blocks
Feb 3 14:16:27 PiCam sshd[804]: debug2: set_newkeys: mode 1
Feb 3 14:16:27 PiCam sshd[804]: debug1: rekey after 4294967296 blocks
Feb 3 14:16:27 PiCam sshd[804]: debug1: ssh_packet_set_postauth: called
Feb 3 14:16:27 PiCam sshd[804]: debug3: ssh_packet_set_state: done
Feb 3 14:16:27 PiCam sshd[804]: debug3: notify_hostkeys: key 0: ssh-rsa SHA256:GYL4YKHmZdne8EruM3iouiQu/ro3l/N0JDgt5llRV3s
Feb 3 14:16:27 PiCam sshd[804]: debug3: notify_hostkeys: key 1: ecdsa-sha2-nistp256 SHA256:7oDr2m9yO4W7LjkIyxFjfMml7G19ilck111wJkLAhnM
Feb 3 14:16:27 PiCam sshd[804]: debug3: notify_hostkeys: key 2: ssh-ed25519 SHA256:xJV6fMkLEDSuzHVTuqEbiBeIkQ3s/7yNIm9Te1tiSjk
Feb 3 14:16:27 PiCam sshd[804]: debug3: notify_hostkeys: sent 3 hostkeys
Feb 3 14:16:27 PiCam sshd[804]: debug3: send packet: type 80
Feb 3 14:16:27 PiCam sshd[804]: debug1: active: key options: agent-forwarding port-forwarding pty user-rc x11-forwarding
Feb 3 14:16:27 PiCam sshd[804]: debug1: Entering interactive session for SSH2.
Feb 3 14:16:27 PiCam sshd[804]: debug2: fd 5 setting O_NONBLOCK
Feb 3 14:16:27 PiCam sshd[804]: debug2: fd 7 setting O_NONBLOCK
Feb 3 14:16:27 PiCam sshd[804]: debug1: server_init_dispatch
Feb 3 14:16:27 PiCam sshd[804]: debug3: receive packet: type 90
Feb 3 14:16:27 PiCam sshd[804]: debug1: server_input_channel_open: ctype session rchan 256 win 16384 max 16384
Feb 3 14:16:27 PiCam sshd[804]: debug1: input_session_request
Feb 3 14:16:27 PiCam sshd[804]: debug1: channel 0: new [server-session]
Feb 3 14:16:27 PiCam sshd[804]: debug2: session_new: allocate (allocated 0 max 10)
Feb 3 14:16:27 PiCam sshd[804]: debug3: session_unused: session id 0 unused
Feb 3 14:16:27 PiCam sshd[804]: debug1: session_new: session 0
Feb 3 14:16:27 PiCam sshd[804]: debug1: session_open: channel 0
Feb 3 14:16:27 PiCam sshd[804]: debug1: session_open: session 0: link with channel 0
Feb 3 14:16:27 PiCam sshd[804]: debug1: server_input_channel_open: confirm session
Feb 3 14:16:27 PiCam sshd[804]: debug3: send packet: type 91
Feb 3 14:16:28 PiCam sshd[804]: debug3: receive packet: type 98
Feb 3 14:16:28 PiCam sshd[804]: debug1: server_input_channel_req: channel 0 request pty-req reply 1
Feb 3 14:16:28 PiCam sshd[804]: debug1: session_by_channel: session 0 channel 0
Feb 3 14:16:28 PiCam sshd[804]: debug1: session_input_channel_req: session 0 req pty-req
Feb 3 14:16:28 PiCam sshd[804]: debug1: Allocating pty.
Feb 3 14:16:28 PiCam sshd[804]: debug3: mm_request_send entering: type 28
Feb 3 14:16:28 PiCam sshd[783]: debug3: mm_request_receive entering
Feb 3 14:16:28 PiCam sshd[783]: debug3: monitor_read: checking request 28
Feb 3 14:16:28 PiCam sshd[783]: debug3: mm_answer_pty entering
Feb 3 14:16:28 PiCam sshd[783]: debug2: session_new: allocate (allocated 0 max 10)
Feb 3 14:16:28 PiCam sshd[783]: debug3: session_unused: session id 0 unused
Feb 3 14:16:28 PiCam sshd[783]: debug1: session_new: session 0
Feb 3 14:16:28 PiCam sshd[783]: debug1: SELinux support disabled
Feb 3 14:16:28 PiCam sshd[783]: debug3: mm_request_send entering: type 29
Feb 3 14:16:28 PiCam sshd[783]: debug3: mm_answer_pty: tty /dev/pts/0 ptyfd 4
Feb 3 14:16:28 PiCam sshd[804]: debug3: mm_pty_allocate: waiting for MONITOR_ANS_PTY
Feb 3 14:16:28 PiCam sshd[804]: debug3: mm_request_receive_expect entering: type 29
Feb 3 14:16:28 PiCam sshd[804]: debug3: mm_request_receive entering
Feb 3 14:16:28 PiCam sshd[804]: debug1: session_pty_req: session 0 alloc /dev/pts/0
Feb 3 14:16:28 PiCam sshd[804]: debug3: send packet: type 99
Feb 3 14:16:28 PiCam sshd[804]: debug3: receive packet: type 98
Feb 3 14:16:28 PiCam sshd[804]: debug1: server_input_channel_req: channel 0 request shell reply 1
Feb 3 14:16:28 PiCam sshd[804]: debug1: session_by_channel: session 0 channel 0
Feb 3 14:16:28 PiCam sshd[804]: debug1: session_input_channel_req: session 0 req shell
Feb 3 14:16:28 PiCam sshd[804]: Starting session: shell on pts/0 for pi from 192.168.68.52 port 65369 id 0
Feb 3 14:16:28 PiCam sshd[804]: debug2: fd 3 setting TCP_NODELAY
Feb 3 14:16:28 PiCam sshd[804]: debug3: ssh_packet_set_tos: set IP_TOS 0x10
Feb 3 14:16:28 PiCam sshd[804]: debug2: channel 0: rfd 10 isatty
Feb 3 14:16:28 PiCam sshd[804]: debug2: fd 10 setting O_NONBLOCK
Feb 3 14:16:28 PiCam sshd[804]: debug3: fd 8 is O_NONBLOCK
Feb 3 14:16:28 PiCam sshd[804]: debug3: send packet: type 99
Feb 3 14:16:28 PiCam sshd[813]: debug1: Setting controlling tty using TIOCSCTTY.
Feb 3 14:16:28 PiCam sshd[813]: debug3: Copy environment: LANG=en_HK
Feb 3 14:16:28 PiCam sshd[813]: debug3: Copy environment: LANGUAGE=en_HK
Feb 3 14:16:28 PiCam sshd[813]: debug3: Copy environment: LC_ALL=en_HK
Feb 3 14:16:47 PiCam sshd[804]: debug3: receive packet: type 98
Feb 3 14:16:47 PiCam sshd[804]: debug1: server_input_channel_req: channel 0 request window-change reply 0
Feb 3 14:16:47 PiCam sshd[804]: debug1: session_by_channel: session 0 channel 0
Feb 3 14:16:47 PiCam sshd[804]: debug1: session_input_channel_req: session 0 req window-change
Feb 3 14:17:01 PiCam CRON[911]: pam_unix(cron:session): session opened for user root by (uid=0)
Feb 3 14:17:01 PiCam CRON[911]: pam_unix(cron:session): session closed for user root
Feb 3 14:17:06 PiCam sshd[804]: debug3: receive packet: type 98
Feb 3 14:17:06 PiCam sshd[804]: debug1: server_input_channel_req: channel 0 request winadj@putty.projects.tartarus.org reply 1
Feb 3 14:17:06 PiCam sshd[804]: debug1: session_by_channel: session 0 channel 0
4.2 测试结果二
隔了一天,所有环境都一致,唯一可能存在的疑点:路由器晚上会关机重启。
目前所有情况都非常理想,也许是路由器或者网络无线干扰引起的问题。
- 10:33:27 - 10:33:43 完成登录,耗时16秒(含用户密码输入)
- 10:33:32 - 10:33:32 环境变量复制,耗时1秒
- 10:33:32 空隙消失
- 10:33:32 pam_unix只出现了一次(貌似上次异常)
- 对比之前,网络环境似乎好了很多
$ cat /var/log/auth.log
Feb 4 10:33:27 PiCam sshd[1131]: debug3: fd 5 is not O_NONBLOCK
Feb 4 10:33:27 PiCam sshd[1131]: debug1: Forked child 1149.
Feb 4 10:33:27 PiCam sshd[1131]: debug3: send_rexec_state: entering fd = 8 config len 306
Feb 4 10:33:27 PiCam sshd[1131]: debug3: ssh_msg_send: type 0
Feb 4 10:33:27 PiCam sshd[1131]: debug3: send_rexec_state: done
Feb 4 10:33:27 PiCam sshd[1149]: debug3: oom_adjust_restore
Feb 4 10:33:27 PiCam sshd[1149]: debug1: Set /proc/self/oom_score_adj to 0
Feb 4 10:33:27 PiCam sshd[1149]: debug1: rexec start in 5 out 5 newsock 5 pipe 7 sock 8
Feb 4 10:33:27 PiCam sshd[1149]: debug1: inetd sockets after dupping: 3, 3
Feb 4 10:33:27 PiCam sshd[1149]: Connection from 192.168.68.52 port 54731 on 192.168.68.245 port 22
Feb 4 10:33:27 PiCam sshd[1149]: debug1: Client protocol version 2.0; client software version PuTTY_Release_0.78
Feb 4 10:33:27 PiCam sshd[1149]: debug1: no match: PuTTY_Release_0.78
Feb 4 10:33:27 PiCam sshd[1149]: debug1: Local version string SSH-2.0-OpenSSH_7.9p1 Raspbian-10+deb10u2+rpt1
Feb 4 10:33:27 PiCam sshd[1149]: debug2: fd 3 setting O_NONBLOCK
Feb 4 10:33:27 PiCam sshd[1149]: debug3: ssh_sandbox_init: preparing seccomp filter sandbox
Feb 4 10:33:27 PiCam sshd[1149]: debug2: Network child is on pid 1150
Feb 4 10:33:27 PiCam sshd[1149]: debug3: preauth child monitor started
Feb 4 10:33:27 PiCam sshd[1149]: debug3: privsep user:group 107:65534 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: permanently_set_uid: 107/65534 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: ssh_sandbox_child: setting PR_SET_NO_NEW_PRIVS [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: ssh_sandbox_child: attaching seccomp filter program [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: list_hostkey_types: rsa-sha2-512,rsa-sha2-256,ssh-rsa,ecdsa-sha2-nistp256,ssh-ed25519 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: send packet: type 20 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: SSH2_MSG_KEXINIT sent [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: receive packet: type 20 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: SSH2_MSG_KEXINIT received [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: local server KEXINIT proposal [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: host key algorithms: rsa-sha2-512,rsa-sha2-256,ssh-rsa,ecdsa-sha2-nistp256,ssh-ed25519 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: compression ctos: none,zlib@openssh.com [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: compression stoc: none,zlib@openssh.com [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: languages ctos: [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: languages stoc: [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: first_kex_follows 0 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: reserved 0 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: peer client KEXINIT proposal [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: KEX algorithms: sntrup761x25519-sha512@openssh.com,curve448-sha512,curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group-exchange-sha1,diffie-hellman-group18-sha512,diffie-hellman-group17-sha512,diffie-hellman-group16-sha512,diffie-hellman-group15-sha512,diffie-hellman-group14-sha256,diffie-hellman-group14-sha1,rsa2048-sha256,rsa1024-sha1,diffie-hellman-group1-sha1,ext-info-c [prea
Feb 4 10:33:27 PiCam sshd[1149]: debug2: host key algorithms: ssh-ed25519,ssh-ed448,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,rsa-sha2-512,rsa-sha2-256,ssh-rsa,ssh-dss [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: ciphers ctos: aes256-ctr,aes256-cbc,rijndael-cbc@lysator.liu.se,aes192-ctr,aes192-cbc,aes128-ctr,aes128-cbc,chacha20-poly1305@openssh.com,aes128-gcm@openssh.com,aes256-gcm@openssh.com,3des-ctr,3des-cbc,blowfish-ctr,blowfish-cbc,arcfour256,arcfour128 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: ciphers stoc: aes256-ctr,aes256-cbc,rijndael-cbc@lysator.liu.se,aes192-ctr,aes192-cbc,aes128-ctr,aes128-cbc,chacha20-poly1305@openssh.com,aes128-gcm@openssh.com,aes256-gcm@openssh.com,3des-ctr,3des-cbc,blowfish-ctr,blowfish-cbc,arcfour256,arcfour128 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: MACs ctos: hmac-sha2-256,hmac-sha1,hmac-sha1-96,hmac-md5,hmac-sha2-256-etm@openssh.com,hmac-sha1-etm@openssh.com,hmac-sha1-96-etm@openssh.com,hmac-md5-etm@openssh.com [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: MACs stoc: hmac-sha2-256,hmac-sha1,hmac-sha1-96,hmac-md5,hmac-sha2-256-etm@openssh.com,hmac-sha1-etm@openssh.com,hmac-sha1-96-etm@openssh.com,hmac-md5-etm@openssh.com [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: compression ctos: none,zlib,zlib@openssh.com [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: compression stoc: none,zlib,zlib@openssh.com [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: languages ctos: [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: languages stoc: [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: first_kex_follows 0 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: reserved 0 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: kex: algorithm: curve25519-sha256 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: kex: host key algorithm: ssh-ed25519 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: kex: client->server cipher: aes256-ctr MAC: hmac-sha2-256 compression: none [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: kex: server->client cipher: aes256-ctr MAC: hmac-sha2-256 compression: none [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: expecting SSH2_MSG_KEX_ECDH_INIT [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: receive packet: type 30 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: mm_sshkey_sign entering [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: mm_request_send entering: type 6 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: mm_request_receive entering
Feb 4 10:33:27 PiCam sshd[1149]: debug3: monitor_read: checking request 6
Feb 4 10:33:27 PiCam sshd[1149]: debug3: mm_answer_sign
Feb 4 10:33:27 PiCam sshd[1149]: debug3: mm_answer_sign: hostkey proof signature 0x855c38(83)
Feb 4 10:33:27 PiCam sshd[1149]: debug3: mm_request_send entering: type 7
Feb 4 10:33:27 PiCam sshd[1149]: debug2: monitor_read: 6 used once, disabling now
Feb 4 10:33:27 PiCam sshd[1149]: debug3: mm_sshkey_sign: waiting for MONITOR_ANS_SIGN [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: mm_request_receive_expect entering: type 7 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: mm_request_receive entering [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: send packet: type 31 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: send packet: type 21 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: set_newkeys: mode 1 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: rekey after 4294967296 blocks [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: SSH2_MSG_NEWKEYS sent [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: expecting SSH2_MSG_NEWKEYS [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: send packet: type 7 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: receive packet: type 21 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: SSH2_MSG_NEWKEYS received [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug2: set_newkeys: mode 0 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: rekey after 4294967296 blocks [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug1: KEX done [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: receive packet: type 5 [preauth]
Feb 4 10:33:27 PiCam sshd[1149]: debug3: send packet: type 6 [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: receive packet: type 50 [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug1: userauth-request for user pi service ssh-connection method none [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug1: attempt 0 failures 0 [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_getpwnamallow entering [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_request_send entering: type 8 [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_getpwnamallow: waiting for MONITOR_ANS_PWNAM [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_request_receive_expect entering: type 9 [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_request_receive entering [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_request_receive entering
Feb 4 10:33:30 PiCam sshd[1149]: debug3: monitor_read: checking request 8
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_answer_pwnamallow
Feb 4 10:33:30 PiCam sshd[1149]: debug2: parse_server_config: config reprocess config len 306
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_answer_pwnamallow: sending MONITOR_ANS_PWNAM: 1
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_request_send entering: type 9
Feb 4 10:33:30 PiCam sshd[1149]: debug2: monitor_read: 8 used once, disabling now
Feb 4 10:33:30 PiCam sshd[1149]: debug2: input_userauth_request: setting up authctxt for pi [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_start_pam entering [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_request_send entering: type 100 [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_inform_authserv entering [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_request_send entering: type 4 [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug2: input_userauth_request: try method none [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: user_specific_delay: user specific delay 0.000ms [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: ensure_minimum_time_since: elapsed 29.097ms, delaying 4.768ms (requested 8.466ms) [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: userauth_finish: failure partial=0 next methods="publickey,password" [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: send packet: type 51 [preauth]
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_request_receive entering
Feb 4 10:33:30 PiCam sshd[1149]: debug3: monitor_read: checking request 100
Feb 4 10:33:30 PiCam sshd[1149]: debug1: PAM: initializing for "pi"
Feb 4 10:33:30 PiCam sshd[1149]: debug1: PAM: setting PAM_RHOST to "192.168.68.52"
Feb 4 10:33:30 PiCam sshd[1149]: debug1: PAM: setting PAM_TTY to "ssh"
Feb 4 10:33:30 PiCam sshd[1149]: debug2: monitor_read: 100 used once, disabling now
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_request_receive entering
Feb 4 10:33:30 PiCam sshd[1149]: debug3: monitor_read: checking request 4
Feb 4 10:33:30 PiCam sshd[1149]: debug3: mm_answer_authserv: service=ssh-connection, style=, role=
Feb 4 10:33:30 PiCam sshd[1149]: debug2: monitor_read: 4 used once, disabling now
Feb 4 10:33:32 PiCam sshd[1149]: debug3: receive packet: type 2 [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: Received SSH2_MSG_IGNORE [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: receive packet: type 50 [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug1: userauth-request for user pi service ssh-connection method password [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug1: attempt 1 failures 0 [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug2: input_userauth_request: try method password [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_auth_password entering [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_send entering: type 12 [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_auth_password: waiting for MONITOR_ANS_AUTHPASSWORD [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_receive_expect entering: type 13 [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_receive entering [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_receive entering
Feb 4 10:33:32 PiCam sshd[1149]: debug3: monitor_read: checking request 12
Feb 4 10:33:32 PiCam sshd[1149]: debug3: PAM: sshpam_passwd_conv called with 1 messages
Feb 4 10:33:32 PiCam sshd[1149]: debug1: PAM: password authentication accepted for pi
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_answer_authpassword: sending result 1
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_send entering: type 13
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_receive_expect entering: type 102
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_receive entering
Feb 4 10:33:32 PiCam sshd[1149]: debug1: do_pam_account: called
Feb 4 10:33:32 PiCam sshd[1149]: debug2: do_pam_account: auth information in SSH_AUTH_INFO_0
Feb 4 10:33:32 PiCam sshd[1149]: debug3: PAM: do_pam_account pam_acct_mgmt = 0 (Success)
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_send entering: type 103
Feb 4 10:33:32 PiCam sshd[1149]: Accepted password for pi from 192.168.68.52 port 54731 ssh2
Feb 4 10:33:32 PiCam sshd[1149]: debug1: monitor_child_preauth: pi has been authenticated by privileged process
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_get_keystate: Waiting for new keys
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_receive_expect entering: type 26
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_receive entering
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_get_keystate: GOT new keys
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_auth_password: user authenticated [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: user_specific_delay: user specific delay 0.000ms [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: ensure_minimum_time_since: elapsed 214.337ms, delaying 56.579ms (requested 8.466ms) [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_do_pam_account entering [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_send entering: type 102 [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_receive_expect entering: type 103 [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_receive entering [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_do_pam_account returning 1 [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: send packet: type 52 [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_send entering: type 26 [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_send_keystate: Finished sending state [preauth]
Feb 4 10:33:32 PiCam sshd[1149]: debug1: monitor_read_log: child log fd closed
Feb 4 10:33:32 PiCam sshd[1149]: debug3: ssh_sandbox_parent_finish: finished
Feb 4 10:33:32 PiCam sshd[1149]: debug1: PAM: establishing credentials
Feb 4 10:33:32 PiCam sshd[1149]: debug3: PAM: opening session
Feb 4 10:33:32 PiCam sshd[1149]: debug2: do_pam_session: auth information in SSH_AUTH_INFO_0
Feb 4 10:33:32 PiCam sshd[1149]: pam_unix(sshd:session): session opened for user pi by (uid=0)
Feb 4 10:33:32 PiCam sshd[1149]: debug3: PAM: sshpam_store_conv called with 1 messages
Feb 4 10:33:32 PiCam sshd[1149]: debug3: PAM: sshpam_store_conv called with 1 messages
Feb 4 10:33:32 PiCam sshd[1149]: User child is on pid 1155
Feb 4 10:33:32 PiCam sshd[1155]: debug1: SELinux support disabled
Feb 4 10:33:32 PiCam sshd[1155]: debug1: PAM: establishing credentials
Feb 4 10:33:32 PiCam sshd[1155]: debug1: permanently_set_uid: 1000/1000
Feb 4 10:33:32 PiCam sshd[1155]: debug3: monitor_apply_keystate: packet_set_state
Feb 4 10:33:32 PiCam sshd[1155]: debug2: set_newkeys: mode 0
Feb 4 10:33:32 PiCam sshd[1155]: debug1: rekey after 4294967296 blocks
Feb 4 10:33:32 PiCam sshd[1155]: debug2: set_newkeys: mode 1
Feb 4 10:33:32 PiCam sshd[1155]: debug1: rekey after 4294967296 blocks
Feb 4 10:33:32 PiCam sshd[1155]: debug1: ssh_packet_set_postauth: called
Feb 4 10:33:32 PiCam sshd[1155]: debug3: ssh_packet_set_state: done
Feb 4 10:33:32 PiCam sshd[1155]: debug3: notify_hostkeys: key 0: ssh-rsa SHA256:GYL4YKHmZdne8EruM3iouiQu/ro3l/N0JDgt5llRV3s
Feb 4 10:33:32 PiCam sshd[1155]: debug3: notify_hostkeys: key 1: ecdsa-sha2-nistp256 SHA256:7oDr2m9yO4W7LjkIyxFjfMml7G19ilck111wJkLAhnM
Feb 4 10:33:32 PiCam sshd[1155]: debug3: notify_hostkeys: key 2: ssh-ed25519 SHA256:xJV6fMkLEDSuzHVTuqEbiBeIkQ3s/7yNIm9Te1tiSjk
Feb 4 10:33:32 PiCam sshd[1155]: debug3: notify_hostkeys: sent 3 hostkeys
Feb 4 10:33:32 PiCam sshd[1155]: debug3: send packet: type 80
Feb 4 10:33:32 PiCam sshd[1155]: debug1: active: key options: agent-forwarding port-forwarding pty user-rc x11-forwarding
Feb 4 10:33:32 PiCam sshd[1155]: debug1: Entering interactive session for SSH2.
Feb 4 10:33:32 PiCam sshd[1155]: debug2: fd 5 setting O_NONBLOCK
Feb 4 10:33:32 PiCam sshd[1155]: debug2: fd 7 setting O_NONBLOCK
Feb 4 10:33:32 PiCam sshd[1155]: debug1: server_init_dispatch
Feb 4 10:33:32 PiCam sshd[1155]: debug3: receive packet: type 90
Feb 4 10:33:32 PiCam sshd[1155]: debug1: server_input_channel_open: ctype session rchan 256 win 16384 max 16384
Feb 4 10:33:32 PiCam sshd[1155]: debug1: input_session_request
Feb 4 10:33:32 PiCam sshd[1155]: debug1: channel 0: new [server-session]
Feb 4 10:33:32 PiCam sshd[1155]: debug2: session_new: allocate (allocated 0 max 10)
Feb 4 10:33:32 PiCam sshd[1155]: debug3: session_unused: session id 0 unused
Feb 4 10:33:32 PiCam sshd[1155]: debug1: session_new: session 0
Feb 4 10:33:32 PiCam sshd[1155]: debug1: session_open: channel 0
Feb 4 10:33:32 PiCam sshd[1155]: debug1: session_open: session 0: link with channel 0
Feb 4 10:33:32 PiCam sshd[1155]: debug1: server_input_channel_open: confirm session
Feb 4 10:33:32 PiCam sshd[1155]: debug3: send packet: type 91
Feb 4 10:33:32 PiCam sshd[1155]: debug3: receive packet: type 98
Feb 4 10:33:32 PiCam sshd[1155]: debug1: server_input_channel_req: channel 0 request pty-req reply 1
Feb 4 10:33:32 PiCam sshd[1155]: debug1: session_by_channel: session 0 channel 0
Feb 4 10:33:32 PiCam sshd[1155]: debug1: session_input_channel_req: session 0 req pty-req
Feb 4 10:33:32 PiCam sshd[1155]: debug1: Allocating pty.
Feb 4 10:33:32 PiCam sshd[1155]: debug3: mm_request_send entering: type 28
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_receive entering
Feb 4 10:33:32 PiCam sshd[1149]: debug3: monitor_read: checking request 28
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_answer_pty entering
Feb 4 10:33:32 PiCam sshd[1149]: debug2: session_new: allocate (allocated 0 max 10)
Feb 4 10:33:32 PiCam sshd[1149]: debug3: session_unused: session id 0 unused
Feb 4 10:33:32 PiCam sshd[1149]: debug1: session_new: session 0
Feb 4 10:33:32 PiCam sshd[1149]: debug1: SELinux support disabled
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_request_send entering: type 29
Feb 4 10:33:32 PiCam sshd[1149]: debug3: mm_answer_pty: tty /dev/pts/1 ptyfd 4
Feb 4 10:33:32 PiCam sshd[1155]: debug3: mm_pty_allocate: waiting for MONITOR_ANS_PTY
Feb 4 10:33:32 PiCam sshd[1155]: debug3: mm_request_receive_expect entering: type 29
Feb 4 10:33:32 PiCam sshd[1155]: debug3: mm_request_receive entering
Feb 4 10:33:32 PiCam sshd[1155]: debug1: session_pty_req: session 0 alloc /dev/pts/1
Feb 4 10:33:32 PiCam sshd[1155]: debug3: send packet: type 99
Feb 4 10:33:32 PiCam sshd[1155]: debug3: receive packet: type 98
Feb 4 10:33:32 PiCam sshd[1155]: debug1: server_input_channel_req: channel 0 request shell reply 1
Feb 4 10:33:32 PiCam sshd[1155]: debug1: session_by_channel: session 0 channel 0
Feb 4 10:33:32 PiCam sshd[1155]: debug1: session_input_channel_req: session 0 req shell
Feb 4 10:33:32 PiCam sshd[1155]: Starting session: shell on pts/1 for pi from 192.168.68.52 port 54731 id 0
Feb 4 10:33:32 PiCam sshd[1155]: debug2: fd 3 setting TCP_NODELAY
Feb 4 10:33:32 PiCam sshd[1155]: debug3: ssh_packet_set_tos: set IP_TOS 0x10
Feb 4 10:33:32 PiCam sshd[1155]: debug2: channel 0: rfd 10 isatty
Feb 4 10:33:32 PiCam sshd[1155]: debug2: fd 10 setting O_NONBLOCK
Feb 4 10:33:32 PiCam sshd[1155]: debug3: fd 8 is O_NONBLOCK
Feb 4 10:33:32 PiCam sshd[1155]: debug3: send packet: type 99
Feb 4 10:33:32 PiCam sshd[1156]: debug1: Setting controlling tty using TIOCSCTTY.
Feb 4 10:33:32 PiCam sshd[1156]: debug3: Copy environment: LANG=en_HK
Feb 4 10:33:32 PiCam sshd[1156]: debug3: Copy environment: LANGUAGE=en_HK
Feb 4 10:33:32 PiCam sshd[1156]: debug3: Copy environment: LC_ALL=en_HK
Feb 4 10:33:32 PiCam sshd[1155]: debug3: receive packet: type 2
Feb 4 10:33:32 PiCam sshd[1155]: debug3: Received SSH2_MSG_IGNORE
Feb 4 10:33:33 PiCam sshd[1155]: debug3: receive packet: type 2
Feb 4 10:33:33 PiCam sshd[1155]: debug3: Received SSH2_MSG_IGNORE
Feb 4 10:33:34 PiCam sshd[1155]: debug3: receive packet: type 2
Feb 4 10:33:34 PiCam sshd[1155]: debug3: Received SSH2_MSG_IGNORE
Feb 4 10:33:35 PiCam sshd[1155]: debug3: receive packet: type 2
Feb 4 10:33:35 PiCam sshd[1155]: debug3: Received SSH2_MSG_IGNORE
Feb 4 10:33:36 PiCam sshd[1155]: debug3: receive packet: type 2
Feb 4 10:33:36 PiCam sshd[1155]: debug3: Received SSH2_MSG_IGNORE
Feb 4 10:33:37 PiCam sshd[1155]: debug3: receive packet: type 2
Feb 4 10:33:37 PiCam sshd[1155]: debug3: Received SSH2_MSG_IGNORE
Feb 4 10:33:38 PiCam sshd[1155]: debug3: receive packet: type 2
Feb 4 10:33:38 PiCam sshd[1155]: debug3: Received SSH2_MSG_IGNORE
Feb 4 10:33:39 PiCam sshd[1155]: debug3: receive packet: type 2
Feb 4 10:33:39 PiCam sshd[1155]: debug3: Received SSH2_MSG_IGNORE
Feb 4 10:33:40 PiCam sshd[1155]: debug3: receive packet: type 2
Feb 4 10:33:40 PiCam sshd[1155]: debug3: Received SSH2_MSG_IGNORE
Feb 4 10:33:41 PiCam sshd[1155]: debug3: receive packet: type 2
Feb 4 10:33:41 PiCam sshd[1155]: debug3: Received SSH2_MSG_IGNORE
Feb 4 10:33:42 PiCam sshd[1155]: debug3: receive packet: type 2
Feb 4 10:33:42 PiCam sshd[1155]: debug3: Received SSH2_MSG_IGNORE
Feb 4 10:33:43 PiCam sshd[1155]: debug3: receive packet: type 2
Feb 4 10:33:43 PiCam sshd[1155]: debug3: Received SSH2_MSG_IGNORE
4.3 RootCause
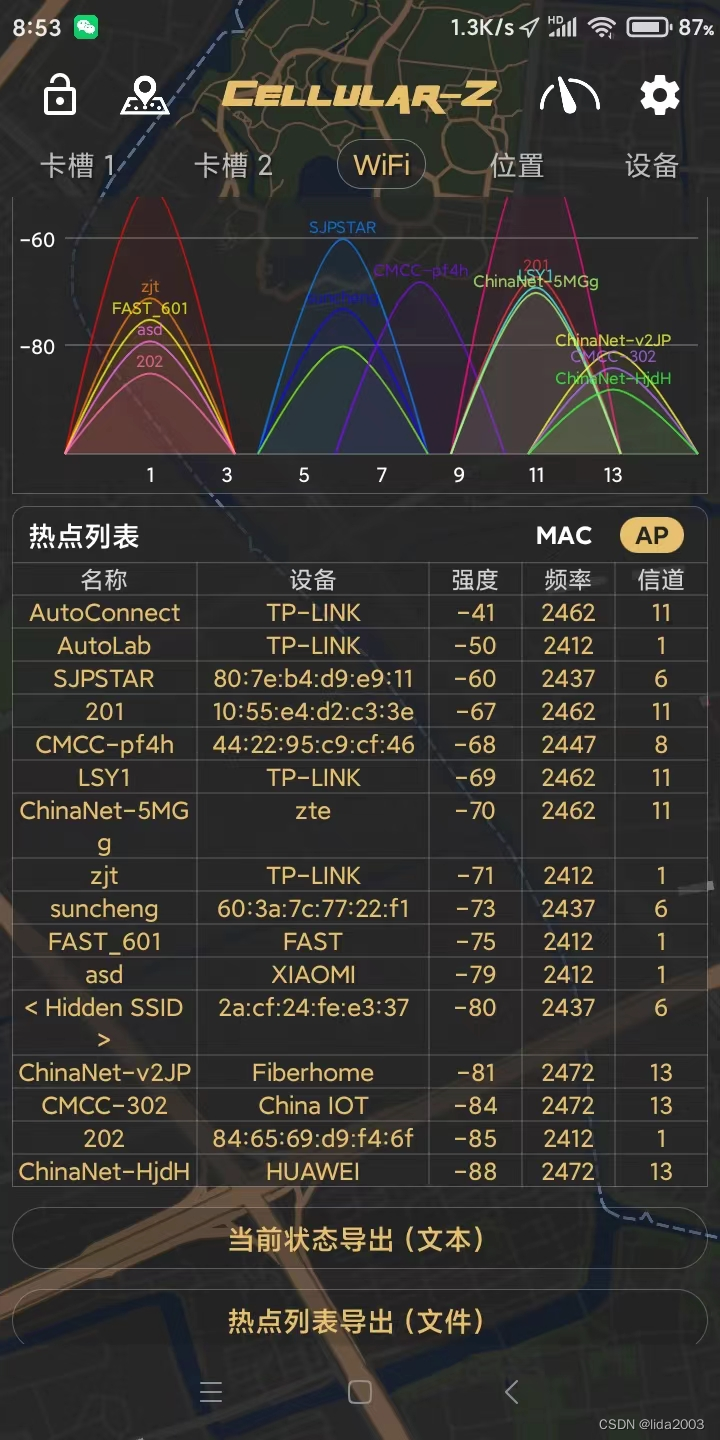
2.4G WiFi网络干扰,导致丢包严重。 在测试ESP32-Camera性能(简单)测试评估时问题尤为显著!
注:出问题的时刻,多个信道信号功率接近。
5. 补充资料
5.1 排除wifi网卡功率自管理问题
pi@PiCam:~ $ sudo journalctl | grep brcmfmac:
Feb 03 15:48:02 PiCam kernel: brcmfmac: F1 signature read @0x18000000=0x1541a9a6
Feb 03 15:48:02 PiCam kernel: brcmfmac: brcmf_fw_alloc_request: using brcm/brcmfmac43430-sdio for chip BCM43430/1
Feb 03 15:48:03 PiCam kernel: brcmfmac: brcmf_fw_alloc_request: using brcm/brcmfmac43430-sdio for chip BCM43430/1
Feb 03 15:48:03 PiCam kernel: brcmfmac: brcmf_fw_alloc_request: using brcm/brcmfmac43430-sdio for chip BCM43430/1
Feb 03 15:48:03 PiCam kernel: brcmfmac: brcmf_c_process_clm_blob: no clm_blob available (err=-2), device may have limited channels available
Feb 03 15:48:03 PiCam kernel: brcmfmac: brcmf_c_preinit_dcmds: Firmware: BCM43430/1 wl0: Oct 22 2019 01:59:28 version 7.45.98.94 (r723000 CY) FWID 01-3b33decd
Feb 03 15:48:29 PiCam kernel: brcmfmac: brcmf_cfg80211_set_power_mgmt: power save disabled
5.2 hostname已经修改(不存在重复)
pi@PiCam:~ $ cat /etc/hosts
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
127.0.1.1 PiCam
pi@PiCam:~ $ cat /etc/hostname
PiCam
6. 参考资料
【1】WiFi monitor模式的配置和运行检查(Ubuntu系统)
【2】ESP32-Camera性能(简单)测试评估
【3】ESP32-FPV-Camera介绍和使用
本文内容由网友自发贡献,版权归原作者所有,本站不承担相应法律责任。如您发现有涉嫌抄袭侵权的内容,请联系:hwhale#tublm.com(使用前将#替换为@)