dpdk版本:
网卡: intel E810
测试拓扑如下:
root@:/usr/share/jmnd_sy_admin2.0/bin# ./testpmd -l 3-5 -n 4 -a ec:01.1 -a ec:09.1 – -i --rxq=2 --txq=2 --rxd=1024 --txd=1024
EAL: Detected CPU lcores: 8
EAL: Detected NUMA nodes: 1
EAL: Detected static linkage of DPDK
EAL: Multi-process socket /var/run/dpdk/rte/mp_socket
EAL: Selected IOVA mode ‘VA’
EAL: No available 1048576 kB hugepages reported
EAL: VFIO support initialized
EAL: Using IOMMU type 1 (Type 1)
EAL: Probe PCI driver: net_iavf (8086:1889) device: 0000:ec:01.1 (socket 0)
EAL: Probe PCI driver: net_iavf (8086:1889) device: 0000:ec:09.1 (socket 0)
Interactive-mode selected
testpmd: create a new mbuf pool <mb_pool_0>: n=1389376, size=2176, socket=0
testpmd: preferred mempool ops selected: ring_mp_mc
Configuring Port 0 (socket 0)
iavf_configure_queues(): request RXDID[22] in Queue[0]
iavf_configure_queues(): request RXDID[22] in Queue[1]
Port 0: link state change event
Port 0: link state change event
Port 0: link state change event
Port 0: link state change event
Port 0: 4A:2B:EA:D7:A1:72
Configuring Port 1 (socket 0)
iavf_configure_queues(): request RXDID[22] in Queue[0]
iavf_configure_queues(): request RXDID[22] in Queue[1]
Port 1: link state change event
Port 1: link state change event
Port 1: link state change event
Port 1: link state change event
Port 1: 3A:09:87:9C:32:A7
Checking link statuses…
Done
testpmd>
testpmd>
testpmd>
testpmd>
testpmd> show port info all
********************* Infos for port 0 *********************
MAC address: 4A:2B:EA:D7:A1:72
Device name: ec:01.1
Driver name: net_iavf
Firmware-version: not available
Devargs:
Connect to socket: 0
memory allocation on the socket: 0
Link status: up
Link speed: 25 Gbps
Link duplex: full-duplex
Autoneg status: On
MTU: 1500
Promiscuous mode: enabled
Allmulticast mode: disabled
Maximum number of MAC addresses: 64
Maximum number of MAC addresses of hash filtering: 0
VLAN offload:
strip off, filter off, extend off, qinq strip off
Hash key size in bytes: 52
Redirection table size: 64
Supported RSS offload flow types:
ipv4
ipv4-frag
ipv4-tcp
ipv4-udp
ipv4-sctp
ipv4-other
ipv6
ipv6-frag
ipv6-tcp
ipv6-udp
ipv6-sctp
ipv6-other
Minimum size of RX buffer: 1024
Maximum configurable length of RX packet: 9728
Maximum configurable size of LRO aggregated packet: 0
Current number of RX queues: 2
Max possible RX queues: 256
Max possible number of RXDs per queue: 4096
Min possible number of RXDs per queue: 64
RXDs number alignment: 32
Current number of TX queues: 2
Max possible TX queues: 256
Max possible number of TXDs per queue: 4096
Min possible number of TXDs per queue: 64
TXDs number alignment: 32
Max segment number per packet: 0
Max segment number per MTU/TSO: 0
Device capabilities: 0x0( )
********************* Infos for port 1 *********************
MAC address: 3A:09:87:9C:32:A7
Device name: ec:09.1
Driver name: net_iavf
Firmware-version: not available
Devargs:
Connect to socket: 0
memory allocation on the socket: 0
Link status: up
Link speed: 25 Gbps
Link duplex: full-duplex
Autoneg status: On
MTU: 1500
Promiscuous mode: enabled
Allmulticast mode: disabled
Maximum number of MAC addresses: 64
Maximum number of MAC addresses of hash filtering: 0
VLAN offload:
strip off, filter off, extend off, qinq strip off
Hash key size in bytes: 52
Redirection table size: 64
Supported RSS offload flow types:
ipv4
ipv4-frag
ipv4-tcp
ipv4-udp
ipv4-sctp
ipv4-other
ipv6
ipv6-frag
ipv6-tcp
ipv6-udp
ipv6-sctp
ipv6-other
Minimum size of RX buffer: 1024
Maximum configurable length of RX packet: 9728
Maximum configurable size of LRO aggregated packet: 0
Current number of RX queues: 2
Max possible RX queues: 256
Max possible number of RXDs per queue: 4096
Min possible number of RXDs per queue: 64
RXDs number alignment: 32
Current number of TX queues: 2
Max possible TX queues: 256
Max possible number of TXDs per queue: 4096
Min possible number of TXDs per queue: 64
TXDs number alignment: 32
Max segment number per packet: 0
Max segment number per MTU/TSO: 0
Device capabilities: 0x0( )
testpmd>
testpmd>
testpmd>
testpmd>
testpmd>
testpmd>
testpmd>
testpmd> set verbose 1
Change verbose level from 0 to 1
testpmd>
testpmd>
testpmd>
testpmd>
testpmd> show config fwd
io packet forwarding - ports=2 - cores=1 - streams=4 - NUMA support enabled, MP allocation mode: native
Logical Core 4 (socket 0) forwards packets on 4 streams:
RX P=0/Q=0 (socket 0) -> TX P=1/Q=0 (socket 0) peer=02:00:00:00:00:01
RX P=1/Q=0 (socket 0) -> TX P=0/Q=0 (socket 0) peer=02:00:00:00:00:00
RX P=0/Q=1 (socket 0) -> TX P=1/Q=1 (socket 0) peer=02:00:00:00:00:01
RX P=1/Q=1 (socket 0) -> TX P=0/Q=1 (socket 0) peer=02:00:00:00:00:00
testpmd> set fwd csum
Set csum packet forwarding mode
testpmd>
testpmd> set nbcore 2
Number of forwarding cores set to 2
testpmd> show config fwd
csum packet forwarding - ports=2 - cores=2 - streams=4 - NUMA support enabled, MP allocation mode: native
Logical Core 4 (socket 0) forwards packets on 2 streams:
RX P=0/Q=0 (socket 0) -> TX P=1/Q=0 (socket 0) peer=02:00:00:00:00:01
RX P=1/Q=0 (socket 0) -> TX P=0/Q=0 (socket 0) peer=02:00:00:00:00:00
Logical Core 5 (socket 0) forwards packets on 2 streams:
RX P=0/Q=1 (socket 0) -> TX P=1/Q=1 (socket 0) peer=02:00:00:00:00:01
RX P=1/Q=1 (socket 0) -> TX P=0/Q=1 (socket 0) peer=02:00:00:00:00:00
testpmd> start
csum packet forwarding - ports=2 - cores=2 - streams=4 - NUMA support enabled, MP allocation mode: native
Logical Core 4 (socket 0) forwards packets on 2 streams:
RX P=0/Q=0 (socket 0) -> TX P=1/Q=0 (socket 0) peer=02:00:00:00:00:01
RX P=1/Q=0 (socket 0) -> TX P=0/Q=0 (socket 0) peer=02:00:00:00:00:00
Logical Core 5 (socket 0) forwards packets on 2 streams:
RX P=0/Q=1 (socket 0) -> TX P=1/Q=1 (socket 0) peer=02:00:00:00:00:01
RX P=1/Q=1 (socket 0) -> TX P=0/Q=1 (socket 0) peer=02:00:00:00:00:00
port 0/queue 0: received 2 packets
src=00:00:00:12:30:10 - dst=4A:2B:EA:D7:A1:72 - type=0x0800 - length=124 - nb_segs=1 - RSS hash=0x535016d0 - RSS queue=0x0 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x0
ol_flags: RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
src=00:00:00:12:30:10 - dst=4A:2B:EA:D7:A1:72 - type=0x0800 - length=124 - nb_segs=1 - RSS hash=0x535016d0 - RSS queue=0x0 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x0
ol_flags: RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
port 0/queue 1: received 4 packets
src=A2:D7:57:2E:9B:4E - dst=FF:FF:FF:FF:FF:FF - type=0x0800 - length=342 - nb_segs=1 - RSS hash=0x1db0ed37 - RSS queue=0x1 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x1
ol_flags: RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
src=9E:75:08:E4:DE:A5 - dst=FF:FF:FF:FF:FF:FF - type=0x0800 - length=342 - nb_segs=1 - RSS hash=0x1db0ed37 - RSS queue=0x1 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x1
ol_flags: RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
src=A2:D7:57:2E:9B:4E - dst=FF:FF:FF:FF:FF:FF - type=0x0800 - length=342 - nb_segs=1 - RSS hash=0x1db0ed37 - RSS queue=0x1 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x1
ol_flags: RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
src=9E:75:08:E4:DE:A5 - dst=FF:FF:FF:FF:FF:FF - type=0x0800 - length=342 - nb_segs=1 - RSS hash=0x1db0ed37 - RSS queue=0x1 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x1
ol_flags: RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
port 1/queue 1: received 5 packets
src=02:9C:D6:84:61:7E - dst=FF:FF:FF:FF:FF:FF - type=0x0800 - length=342 - nb_segs=1 - RSS hash=0x995baca7 - RSS queue=0x1 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x1
ol_flags: RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
src=9E:98:EB:77:DC:AC - dst=FF:FF:FF:FF:FF:FF - type=0x0800 - length=342 - nb_segs=1 - RSS hash=0x995baca7 - RSS queue=0x1 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x1
ol_flags: RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
src=9E:98:EB:77:DC:AC - dst=FF:FF:FF:FF:FF:FF - type=0x0800 - length=342 - nb_segs=1 - RSS hash=0x995baca7 - RSS queue=0x1 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x1
ol_flags: RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
src=02:9C:D6:84:61:7E - dst=FF:FF:FF:FF:FF:FF - type=0x0800 - length=342 - nb_segs=1 - RSS hash=0x995baca7 - RSS queue=0x1 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x1
ol_flags: RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
src=9E:98:EB:77:DC:AC - dst=FF:FF:FF:FF:FF:FF - type=0x0800 - length=342 - nb_segs=1 - RSS hash=0x995baca7 - RSS queue=0x1 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x1
ol_flags: RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
csum packet forwarding packets/burst=32
nb forwarding cores=2 - nb forwarding ports=2
port 0: RX queue number: 2 Tx queue number: 2
Rx offloads=0x80000 Tx offloads=0x10000
RX queue: 0
RX desc=1024 - RX free threshold=32
RX threshold registers: pthresh=0 hthresh=0 wthresh=0
RX Offloads=0x0
TX queue: 0
TX desc=1024 - TX free threshold=32
TX threshold registers: pthresh=0 hthresh=0 wthresh=0
TX offloads=0x10000 - TX RS bit threshold=32
port 1: RX queue number: 2 Tx queue number: 2
Rx offloads=0x80000 Tx offloads=0x10000
RX queue: 0
RX desc=1024 - RX free threshold=32
RX threshold registers: pthresh=0 hthresh=0 wthresh=0
RX Offloads=0x0
TX queue: 0
TX desc=1024 - TX free threshold=32
TX threshold registers: pthresh=0 hthresh=0 wthresh=0
TX offloads=0x10000 - TX RS bit threshold=32
testpmd>
testpmd>
testpmd> stop
Telling cores to stop…
Waiting for lcores to finish…
------- Forward Stats for RX Port= 0/Queue= 0 -> TX Port= 1/Queue= 0 -------
RX-packets: 1 TX-packets: 1 TX-dropped: 0 RX- bad IP checksum: 0 Rx- bad L4 checksum: 0 Rx- bad outer L4 checksum: 0
RX- bad outer IP checksum: 0
------- Forward Stats for RX Port= 0/Queue= 1 -> TX Port= 1/Queue= 1 -------
RX-packets: 9 TX-packets: 9 TX-dropped: 0 RX- bad IP checksum: 0 Rx- bad L4 checksum: 0 Rx- bad outer L4 checksum: 0
RX- bad outer IP checksum: 0
------- Forward Stats for RX Port= 1/Queue= 1 -> TX Port= 0/Queue= 1 -------
RX-packets: 7 TX-packets: 7 TX-dropped: 0 RX- bad IP checksum: 0 Rx- bad L4 checksum: 0 Rx- bad outer L4 checksum: 0
RX- bad outer IP checksum: 0
---------------------- Forward statistics for port 0 ----------------------
RX-packets: 10 RX-dropped: 0 RX-total: 10
Bad-ipcsum: 0 Bad-l4csum: 0 Bad-outer-l4csum: 0
Bad-outer-ipcsum: 0
TX-packets: 7 TX-dropped: 0 TX-total: 7
---------------------- Forward statistics for port 1 ----------------------
RX-packets: 8 RX-dropped: 0 RX-total: 8
Bad-ipcsum: 0 Bad-l4csum: 0 Bad-outer-l4csum: 0
Bad-outer-ipcsum: 0
TX-packets: 10 TX-dropped: 0 TX-total: 10
+++++++++++++++ Accumulated forward statistics for all ports+++++++++++++++
RX-packets: 18 RX-dropped: 0 RX-total: 18
TX-packets: 17 TX-dropped: 0 TX-total: 17
++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
Done.
testpmd>
testpmd>
testpmd> port stop all
Stopping ports…
Checking link statuses…
Done
testpmd>
testpmd>
testpmd>
testpmd>
testpmd> csum set ip hw 0
Parse tunnel is off
IP checksum offload is hw
UDP checksum offload is sw
TCP checksum offload is sw
SCTP checksum offload is sw
Outer-Ip checksum offload is sw
Outer-Udp checksum offload is sw
testpmd> csum set tcp hw 0
Parse tunnel is off
IP checksum offload is hw
UDP checksum offload is sw
TCP checksum offload is hw
SCTP checksum offload is sw
Outer-Ip checksum offload is sw
Outer-Udp checksum offload is sw
testpmd> csum set udp hw 0
Parse tunnel is off
IP checksum offload is hw
UDP checksum offload is hw
TCP checksum offload is hw
SCTP checksum offload is sw
Outer-Ip checksum offload is sw
Outer-Udp checksum offload is sw
testpmd> csum set outer-udp hw 0
Outer UDP checksum offload is not supported by port 0
Parse tunnel is off
IP checksum offload is hw
UDP checksum offload is hw
TCP checksum offload is hw
SCTP checksum offload is sw
Outer-Ip checksum offload is sw
Outer-Udp checksum offload is sw
testpmd> csum set outer-ip hw 0
Parse tunnel is off
IP checksum offload is hw
UDP checksum offload is hw
TCP checksum offload is hw
SCTP checksum offload is sw
Outer-Ip checksum offload is hw
Outer-Udp checksum offload is sw
testpmd> csum set sctp hw 0
Parse tunnel is off
IP checksum offload is hw
UDP checksum offload is hw
TCP checksum offload is hw
SCTP checksum offload is hw
Outer-Ip checksum offload is hw
Outer-Udp checksum offload is sw
testpmd> csum parse-tunnel on 0
Parse tunnel is on
IP checksum offload is hw
UDP checksum offload is hw
TCP checksum offload is hw
SCTP checksum offload is hw
Outer-Ip checksum offload is hw
Outer-Udp checksum offload is sw
testpmd> port start all
Configuring Port 0 (socket 0)
iavf_configure_queues(): request RXDID[22] in Queue[0]
iavf_configure_queues(): request RXDID[22] in Queue[1]
Port 0: link state change event
Port 0: link state change event
Port 0: link state change event
Port 0: link state change event
Port 0: 4A:2B:EA:D7:A1:72
iavf_configure_queues(): request RXDID[22] in Queue[0]
iavf_configure_queues(): request RXDID[22] in Queue[1]
Port 1: link state change event
Port 1: link state change event
Port 1: link state change event
Port 1: link state change event
Port 1: 3A:09:87:9C:32:A7
Checking link statuses…
Done
testpmd>
testpmd>
testpmd>
testpmd>
testpmd> start
csum packet forwarding - ports=2 - cores=2 - streams=4 - NUMA support enabled, MP allocation mode: nati ve
Logical Core 4 (socket 0) forwards packets on 2 streams:
RX P=0/Q=0 (socket 0) -> TX P=1/Q=0 (socket 0) peer=02:00:00:00:00:01
RX P=1/Q=0 (socket 0) -> TX P=0/Q=0 (socket 0) peer=02:00:00:00:00:00
Logical Core 5 (socket 0) forwards packets on 2 streams:
RX P=0/Q=1 (socket 0) -> TX P=1/Q=1 (socket 0) peer=02:00:00:00:00:01
RX P=1/Q=1 (socket 0) -> TX P=0/Q=1 (socket 0) peer=02:00:00:00:00:00
csum packet forwarding packets/burst=32
nb forwarding cores=2 - nb forwarding ports=2
port 0: RX queue number: 2 Tx queue number: 2
Rx offloads=0x80000 Tx offloads=0x1009e
RX queue: 0
RX desc=1024 - RX free threshold=32
RX threshold registers: pthresh=0 hthresh=0 wthresh=0
RX Offloads=0x0
TX queue: 0
TX desc=1024 - TX free threshold=32
TX threshold registers: pthresh=0 hthresh=0 wthresh=0
TX offloads=0x1009e - TX RS bit threshold=32
port 1: RX queue number: 2 Tx queue number: 2
Rx offloads=0x80000 Tx offloads=0x10000
RX queue: 0
RX desc=1024 - RX free threshold=32
RX threshold registers: pthresh=0 hthresh=0 wthresh=0
RX Offloads=0x0
TX queue: 0
TX desc=1024 - TX free threshold=32
TX threshold registers: pthresh=0 hthresh=0 wthresh=0
TX offloads=0x10000 - TX RS bit threshold=32
testpmd>
发送的vxlan报文格式如下:
外层ip不带checksum
外层udp不带checksum
内层ip不带checksum
内层udp不带checksum
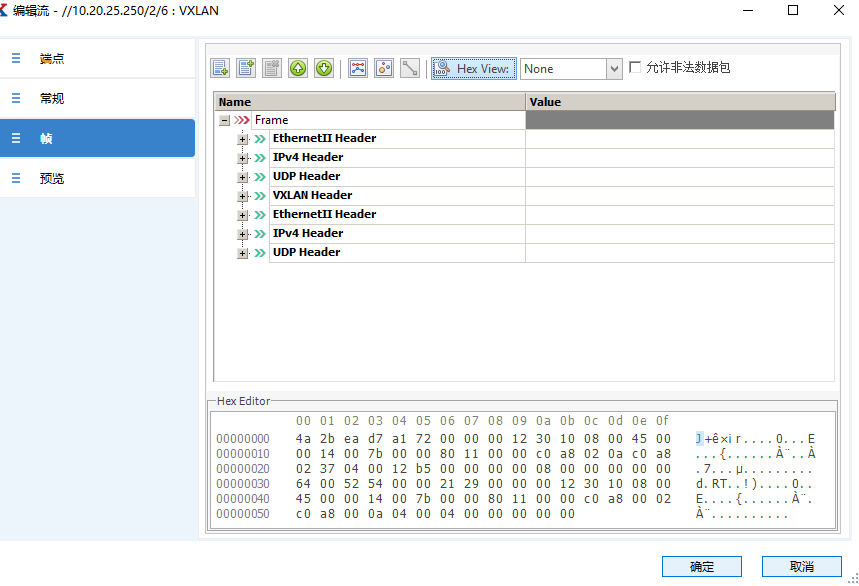
另外一个口接收到的报文:
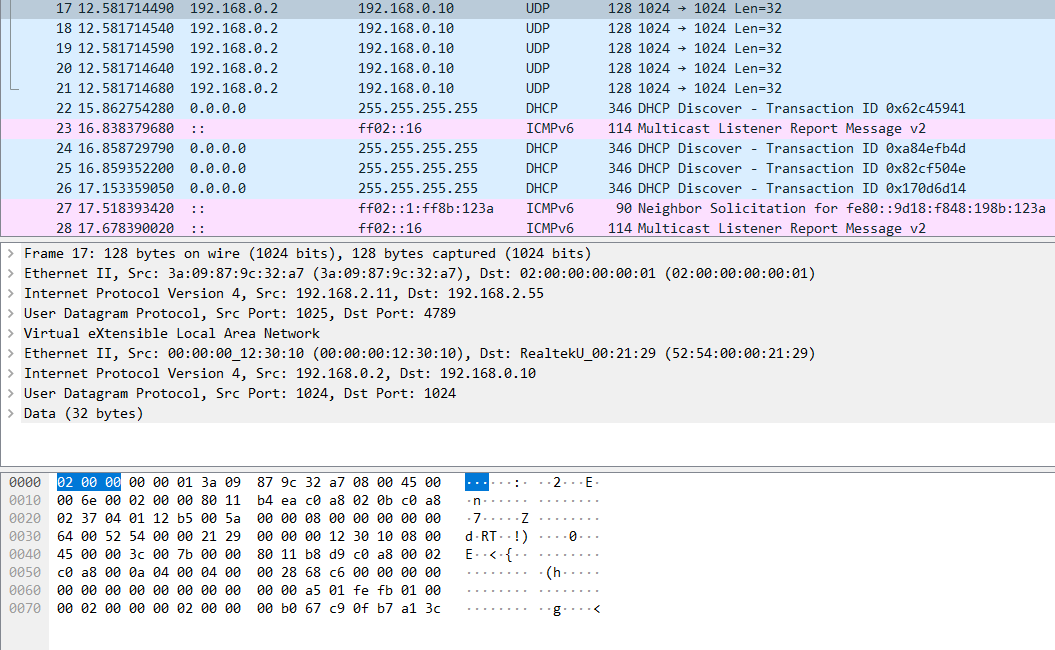
src=00:00:00:12:30:10 - dst=4A:2B:EA:D7:A1:72 - type=0x0800 - length=124 - nb_segs=1 - RSS hash=0xe7de5cb - RSS queue=0x1 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x1
ol_flags: RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
port=0, mbuf=0x1073fe800, pkt_len=124, nb_segs=1:
rx: l2_len=14 ethertype=800 l3_len=20 l4_proto=17 l4_len=8 flags=RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
tx: flags=RTE_MBUF_F_TX_L4_NO_CKSUM RTE_MBUF_F_TX_IPV4
port=0, mbuf=0x1073fdec0, pkt_len=124, nb_segs=1:
rx: l2_len=14 ethertype=800 l3_len=20 l4_proto=17 l4_len=8 flags=RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
tx: flags=RTE_MBUF_F_TX_L4_NO_CKSUM RTE_MBUF_F_TX_IPV4
port=0, mbuf=0x1073fd580, pkt_len=124, nb_segs=1:
rx: l2_len=14 ethertype=800 l3_len=20 l4_proto=17 l4_len=8 flags=RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
tx: flags=RTE_MBUF_F_TX_L4_NO_CKSUM RTE_MBUF_F_TX_IPV4
port=0, mbuf=0x1073fcc40, pkt_len=124, nb_segs=1:
rx: l2_len=14 ethertype=800 l3_len=20 l4_proto=17 l4_len=8 flags=RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
tx: flags=RTE_MBUF_F_TX_L4_NO_CKSUM RTE_MBUF_F_TX_IPV4
port=0, mbuf=0x1073fc300, pkt_len=124, nb_segs=1:
rx: l2_len=14 ethertype=800 l3_len=20 l4_proto=17 l4_len=8 flags=RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
tx: flags=RTE_MBUF_F_TX_L4_NO_CKSUM RTE_MBUF_F_TX_IPV4
port 1/queue 0: received 1 packets
src=02:9C:D6:84:61:7E - dst=FF:FF:FF:FF:FF:FF - type=0x0800 - length=342 - nb_segs=1 - RSS hash=0x80b70466 - RSS queue=0x0 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x0
ol_flags: RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
port=1, mbuf=0x1075dbd00, pkt_len=342, nb_segs=1:
rx: l2_len=14 ethertype=800 l3_len=20 l4_proto=17 l4_len=8 flags=RTE_MBUF_F_RX_RSS_HASH RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
tx: m->l2_len=14 m->l3_len=20 m->l4_len=8
tx: flags=RTE_MBUF_F_TX_IP_CKSUM RTE_MBUF_F_TX_UDP_CKSUM RTE_MBUF_F_TX_IPV4
#define IAVF_TX_OFFLOAD_MASK (
RTE_MBUF_F_TX_OUTER_IPV6 |
RTE_MBUF_F_TX_OUTER_IPV4 |
RTE_MBUF_F_TX_IPV6 |
RTE_MBUF_F_TX_IPV4 |
RTE_MBUF_F_TX_VLAN |
RTE_MBUF_F_TX_IP_CKSUM |
RTE_MBUF_F_TX_L4_MASK |
RTE_MBUF_F_TX_TCP_SEG |
RTE_ETH_TX_OFFLOAD_SECURITY)
testpmd> port 0/queue 0: received 1 packets
src=00:00:00:12:30:10 - dst=4A:2B:EA:D7:A1:72 - type=0x0800 - length=124 - nb_segs=1 - hw ptype: L2_ETHER L3_IPV4_EXT_UNKNOWN L4_UDP - sw ptype: L2_ETHER L3_IPV4 L4_UDP - l2_len=14 - l3_len=20 - l4_len=8 - Receive queue=0x0
ol_flags: RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
m->ol_flags = 0x180
m->pkt_len = 124
0x4a 2b ea d7 a1 72 00 00 00 12 30 10 08 00 45 00
0x00 6e 00 01 00 00 80 11 b4 ec c0 a8 02 0a c0 a8
0x02 37 04 00 12 b5 00 5a 00 00 08 00 00 00 00 00
0x64 00 52 54 00 00 21 29 00 00 00 12 30 10 08 00
0x45 00 00 3c 00 7b 00 00 80 11 b8 d9 c0 a8 00 02
0xc0 a8 00 0a 04 00 04 00 00 28 f3 76 00 00 00 00
0x00 00 00 00 00 00 00 00 00 00 a5 01 fe fc 01 00
0x00 02 00 00 00 01 00 00 00 76 dd 52
txp->parse_tunnel = 1
vxlan parse start
vxlan parse update_tunnel_outer last
info->is_tunnel = 1
port=0, mbuf=0x10c5d1680, pkt_len=124, nb_segs=1:
rx: l2_len=30 ethertype=800 l3_len=20 l4_proto=17 l4_len=8 flags=RTE_MBUF_F_RX_L4_CKSUM_GOOD RTE_MBUF_F_RX_IP_CKSUM_GOOD RTE_MBUF_F_RX_OUTER_L4_CKSUM_UNKNOWN
is_tunnel = 1, tx_offloads = 0x10086, tx_ol_flags = 0xcf0200000000000
tx: m->l2_len=30 m->l3_len=20 m->l4_len=8
tx: m->outer_l2_len=14 m->outer_l3_len=20
rx: outer_l2_len=14 outer_ethertype=800 outer_l3_len=20
tx: m->l2_len=30 m->l3_len=20 m->l4_len=8
tx: m->outer_l2_len=14 m->outer_l3_len=20
tx: flags=RTE_MBUF_F_TX_IP_CKSUM RTE_MBUF_F_TX_UDP_CKSUM RTE_MBUF_F_TX_IPV4 RTE_MBUF_F_TX_OUTER_IP_CKSUM RTE_MBUF_F_TX_OUTER_IPV4 RTE_MBUF_F_TX_TUNNEL_VXLAN
nb_pkts = 1
iavf_prep_pkts, nb_pkts = 1
333333nb_prep = 0
Preparing packet burst to transmit failed: Operation not supported
本文内容由网友自发贡献,版权归原作者所有,本站不承担相应法律责任。如您发现有涉嫌抄袭侵权的内容,请联系:hwhale#tublm.com(使用前将#替换为@)